Hardware attacks are very crucial and they cannot be easily patched like applications/website. Some hardware attacks cannot be patched as they needs to re-designed from scratch.
CONTENTS:
- Introduction
- Attack on LG Nexus Smart-phone
- What Are Cold Boot Attacks?
- Dram And Cold Boot Attacks: What’s The Link?
- How Dram Reacts With Different Turning Off Modes?
- Performing An Attack
- Best Ways For Preventing Them
- Conclusion
- Last But Not The Least
- Resources
- You May Be Interested In
INTRODUCTION:
Have you ever heard of stealing data from computer via hardware stuff? If you have not yet, I’ve got to reveal you that, yes, something like that is indeed done. Have you ever wondered how it is done and what are such attacks coined as? Well, one such hardware attack that is predominantly ongoing in many places is the ‘Cold Boot Attack’. This blog will explain you about the different segments of it in-depth.
Attack on LG Nexus smart-phone
This attack has also been recently discovered in LG nexus smart phone released by the Korean manufacture 5years back. This is mentioned as CV-2020-12753. Here, the attacker leads to exploit the qualcomm secure bootloader and flash a custom firmware which leads makes a brand new user if left unnoticed. Patch has been rolled out by the manufacturer make sure to update this.
This is considered to be one of the patches released to the smart phones even after exhausted warranty period. To get to know the recent trends in cyberattacks subscribe to our Threadsploit reports Patch:LVE-SMP-200006.
WHAT ARE COLD BOOT ATTACKS?
This attack is done by gaining the physical access of the target system. Here, the intruder removes the rear casing of the system and gains access to the memory portion (DRAM). Through this technique, the intruder can access the data of the device’s memory. Of course, it is done when the user is away from the system.
DRAM AND COLD BOOT ATTACKS: WHAT’S THE LINK?
This attack usually takes some time for the intruder as they need to have some pre-installed strategies to get it done.
From the above, you may have a doubt that why the intruder needs to target RAM?
Before knowing it, we need to dig in to the basics of RAM (Random Access Memory) and DRAM (Dynamic Random Access Memory). RAM is a volatile form of memory (temporary) and DRAM is a classification of RAM, that needs to be refreshed periodically. The working of DRAM is simple.
Just consider a capacitor in which one end is connected to power/ground and the other end is connected to the data line. Here the data is stored in the memory which is made of simple capacitor and transistor. Due to the type of memory formation, leakage of data occurs in DRAM. In order to overcome this, Engineers advice to refresh it periodically which when failed, results in the loss of data.
HOW DRAM REACTS WITH DIFFERENT TURNING OFF MODES?
Have you ever tried Hibernating your system? What happens when you hibernate/ shutdown/sleep your machine?
Let me give you a walkthrough of that.
While Sleep:
It is just like a normal human thing. Even when you sleep, your brain is still active. This is just the exact case over here. When you put your system into sleep mode, it just stops all the operations performed in the machine and goes to sleep but the memory (DRAM) still works. In DRAM, the data stored would not get erased but instead, it tends to refresh periodically. This creates a possibility for an intruder to perform the attack.
Now, you may assume that shutting down your machine prevents you from the intruder. But the truth is not that case!
Shut Down:
On this note, let me tell you what happens while you shut down your machine.
When you turn off, DRAM data starts to degrade slowly and it will take hours to erase the data from its memory since no power is flowing. So, by the use of liquid nitrogen, we can reconstruct about 90% of the data which is more than enough for the intruder and whenever the machine gets rebooted, the DRAM will have about 50% of the original data since it cannot be discarded as there is no power flow. This is a flaw in the windows OS which cannot be rectified since all the users need to reboot their machine like a rapid fire.
During Hibernate:
Last but not least is the Hibernate process. So, when you Hibernate your machine, the maximum power required by the DRAM flows to the device and all the data in it get erased.
This type of attack is possible in Apple MacBook but not in Linux machines. This makes them unique since it requires a root access for this process and Linux doesn’t allow them without the knowledge of the user.
PERFORMING AN ATTACK:
To perform an attack, the intruder needs to have a strong knowledge in customization of Linux kernel and the ways to integrate the hardware with the machine. The main constraint behind building a kernel is to boot the OS with minimal memory constraint which makes the intruder to get more amount of data from the device. The main reason is, it should not get clashed with the new kernel data. If clashed, then data would get corrupted. Apart from interfacing and building a custom kernel, a liquid nitrogen to cool the RAM is needed which makes easy for the intruder to gain more amount of data.
Initially, when an intruder gains physical access to the device, he/she primarily removes all the other components and finds the RAM. Once found, liquid nitrogen is sprayed and it looks alike. Once the RAM gets cooled, data present in it will remain for a longer time.
Consider when the intruder does not spray, then the data gets lost in 10 minutes.

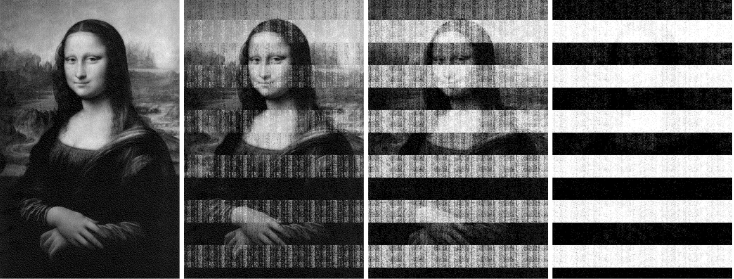
Above figure shows an exact scenario of how data gets degraded in DRAM. Let us split in stages.
Intruder can get the data till 3rd stage and to retain the data, nitrogen cooling method is used. Once the intruder takes the DRAM, the intruder can plug it to the hardware and now it is possible to see the data via a customized Linux Kernel which has been built before.
BEST WAYS FOR PREVENTING THEM:
The best way to stay from this attack is to move for the Linux OS. But, it is difficult for the users to change since they are well familiar with Windows.
The second way is the LIVE OS in which the OS is installed in an external portable device. Here, the user plugs in the external device, the data is processed and when unplugged, the features installed will be gone forever but the OS will still remain.
If the user needs to store the processed information, then he can go with PERSISTENT OS method which is same as LIVE OS but the main difference is, it can store the whatever feature that has newly installed. To perform this step, you need a minimum of 64GB of portable device. Moreover, this feature is available in WINDOWS named as WINDOWS TO GO.
The third and the final way to safeguard is, we need to step into the BIOS mode of the computer where we will find secure boot option. Once found, we need to change it from the standard mode to the custom mode. It is done mainly to prevent any malicious code booting in your computer since it works before the start of the boot process.
There are 4 main concerns of secure boot process. They are
- Platform key (PK)
- Key Exchange Key (KEK)
- db (allow)
- dbx (deny)
The PK is issued by the Hardware manufacturers whereas the KEK is issued by the software manufactures. To perform an exact secure boot process, we need to change the keys present in the PK and KEK. Before performing this action, make sure that you have a copy of the old keys in your hand and replace it with your randomly generated new keys. The db and dbx are like authentication factors. If found legit, they allow to boot the system. If not, they just thwart.
CONCLUSION:
However, cold boot attacks are possible only if an intruder has a physical access. Even if physical access is made possible by someone, then the intruder should not be let to take the data from the machine. Cold boot attacks are however a vintage old myth but are still a serious threat until DRAM exists. So, while using any machine, try to hibernate it or if you chose to shut down, just check with your secure boot settings.
With this, I would conclude my say!
LAST BUT NOT THE LEAST:
While travelling, when you see something good, you stand for a second, watch it, check it out and then you would leave with a smile. Similarly, one such great asset in Briskinfosec’s possession is Threatsploit Adversary Report. It is a single report that has the collection of worldwide occurred cyberattacks, the victims of it and much more on a monthly basis. Just check it out. The information provided in it is surely bound to put up a happy smile on your face!
Resources
YOU MAY BE INTERESTED IN:





