You are vulnerable to cyberattacks even after disposing your network connected devices like modem, router, IP cameras, etc. Information such as device configuration, firmware details and no of devices present in the organization can be exposed by devices even after unplugging from the network. Secure disposing should be followed.
Table of Contents
- Introduction
- UART
- Attack on Mi speaker
- List of Requirement
- Audit Road Map
- Conclusion
- Resources
- You may be also interested on
Introduction
Most common people always think cyberattacks are performed based on website and network. Here is an interesting hardware hack that an attacker can perform with adequate skills by accessing the Hardware component from the junkyard/E-waste. People can sneak/eavesdrop your personal data even from the dump. Routers, IoT devices and other communication devices comes with intricate protocols; most of us do not know how these components communicate with each other. There are various protocols used in transfer of data between the lines such as UART, SPI, JTAG, I2C, CAN etc.
Here we are going to exploit the UART protocol as it is one of the most used in devices like routers, cameras, even your set top boxes.
Let us pick up a used router from a scrap yard and exploit..
UART
Universal Asynchronous Receiver Transmitter (UART) is a communication protocol. It transmits and receives data serially unlike SPI and I2C. The hardware consists of TX and RX pin followed by ground and Vcc. It is a physical circuit present in the printed circuit boards as shown below,
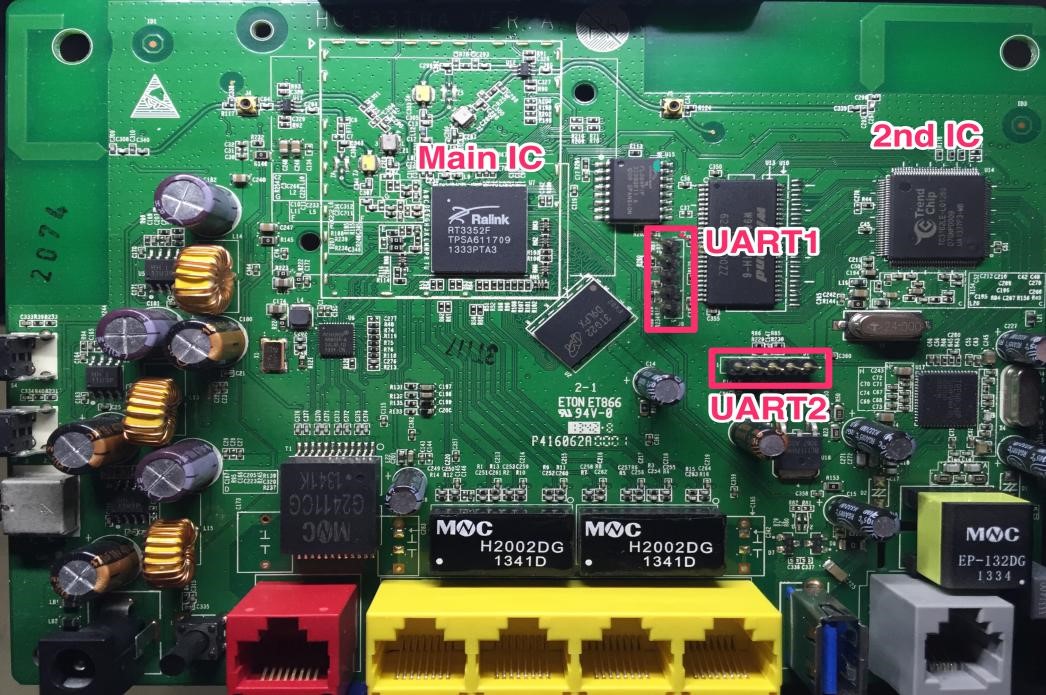
These UART pins can be seen in almost all routers and electronic devices. The intruders found a way to exploit from those pins. In the above image the pins appear as though they are soldered using bus stick, but they should be soldered manually.
Let me walk you through the process to connect and access UART pins.
Attack on Mi speaker
Recent attacks on Mi speaker CVE-2020-8994 exposed sensitive information's related to the Wi-Fi password or SSID via inducing a backdoor.
List of Requirements:
Hardware Required
- A PCB with UART pins
- Bus stick(optional)
- Single lead wires(optional)
- IPA solution
- Flux
- Soldering ion with lead
- Logic analyzer
- An serial interface (bus pirate in my case)
- Multimeter
- Header wire
Software Required
- Pulse view(A digital CRO)
- Putty or screen (if you are using attify badge then you should find the related attify GUI interface)
- You can also use shikra, Jtagulator, attify badge or ft2232h, whichever is convenient.
So now let’s start with the exploitation phase. This attack can also be performed by using Arduino development boards.
Audit Road Map:
Bus Pirate
It is an open source hardware for intercepting UART, SPI, i2c and JTAG protocols. Before using the bus pirate, check the changes to be made in the PC. We initially should modify the UDEV and other rules by using GEDIT.
For this exploitation, I personally used a v3.6a, where 4 is in beta stage of testing.

In this there will be an interface at the right corner of the board which is used for interfacing the bus pirate with the test equipment. These pins are used in a unique way where MOSI is used as a TX and MISO is used an RX.
UART works on both 3.3 and 5v where bus pirate is compatible with both the voltages.
To get updated about cyber-attacks subscribe to our Threatsploit
Identification of Transmitter and Receiver
In connections at times we might get confused between a transmitter and a receiver and also between a GND and VCC. Just take a multimeter and put it on to continuity mode and find the ground pin by turning off the test equipment. Then follow the same step to find the VCC pin but most probably this pin will be in direct contact with the capacitor.
*HINT:
At the test equipment, the power pin is an easy way to find the ground and VCC pin, but should be careful while checking it.
Once the GND and VCC pin is identified, we should find the transmitter and the receiver pin in the next step. To do this we require a logic analyzer which you might think saleae logic analyzer you can find a simple one from amazon or any Chinese websites. Once connected open the pulse-view software and select the logic analyzer as saleae and just click on the run button.
The TX and RX pin starts first. UART does not have a clock instead it has a start and stop bit. The below picture will give you an idea on it.
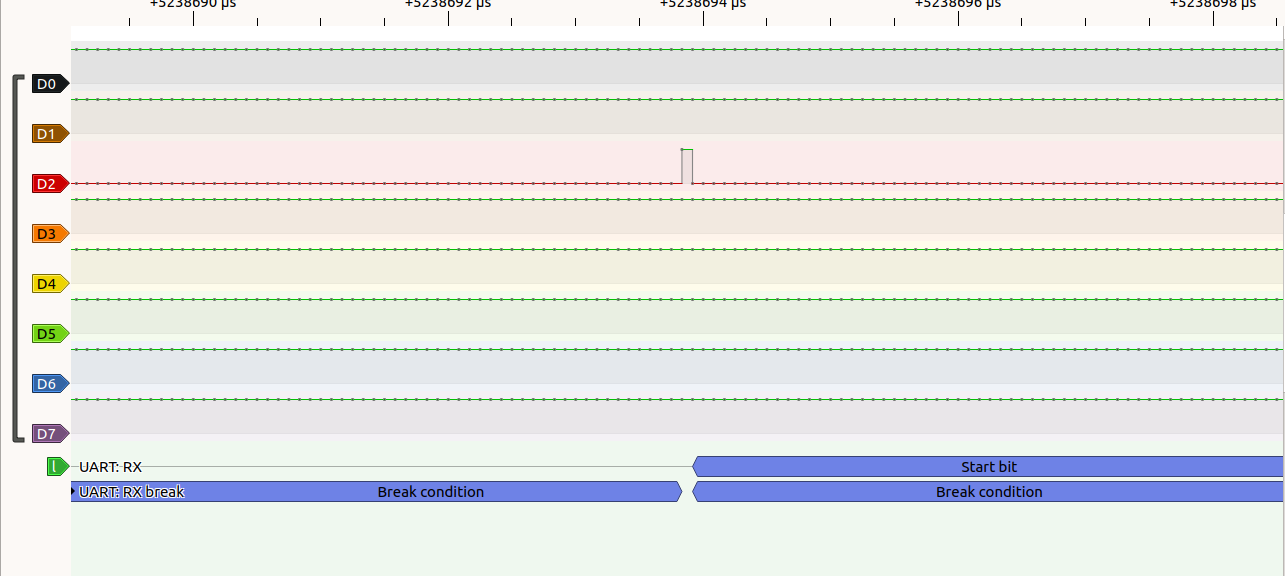
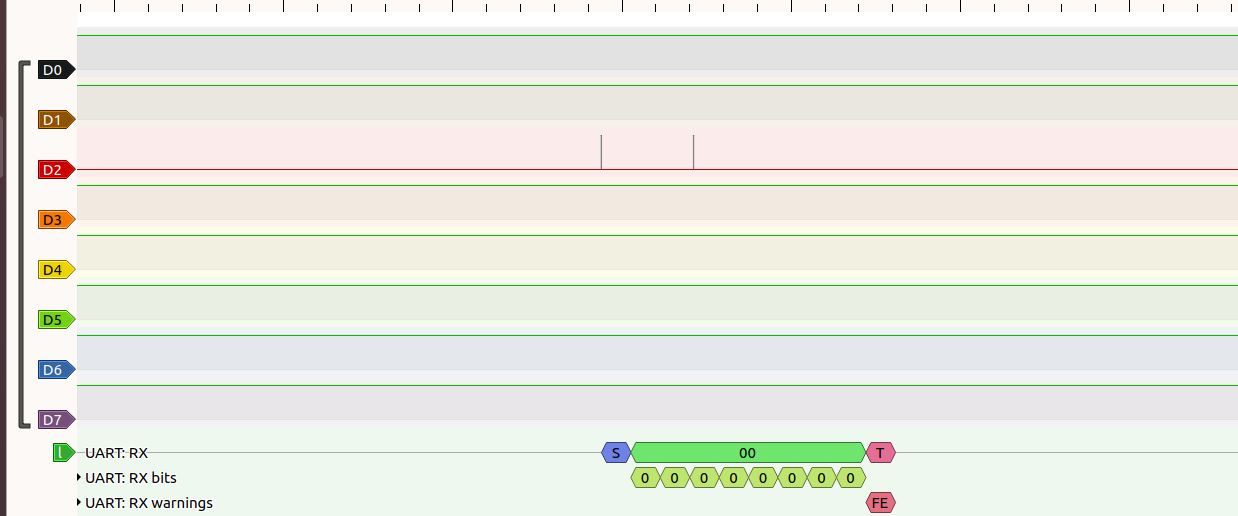
Here I manually assigned D2 pin as my transmitter and D3 as my receiver which can be modified in the first pin present at the bottom and make sure that you have not short circuited the VCC and GND.
So now we have the designators of 4 pins the TX, RX, GND and VCC. Now make the connection as per below table.
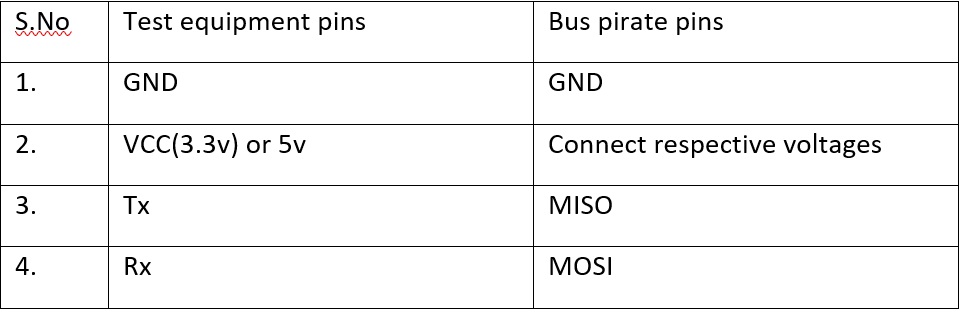
If the does not see any vref light blinking in the bus pirate just interchange the Tx and Rx pins. Once it gets connected, open the putty or screen and ascertain the baud-rate. Most probably 9600 or 115200 is a standard baud-rate used in UART.
Next is the exploitation phase. After opening the putty, make sure you set the desired baud-rate and serial communication option and start the process. In putty, provide “Hiz>m“ to choose the type of communication you need to intercept, select the first option and click enter till you see a message, “are you sure y/n”.
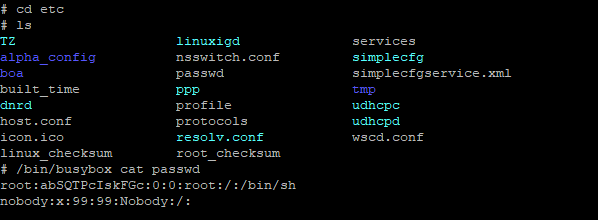
Now turn on/off the device multiple times until you get a shell access. Then it will ask you to either enter a password or it simply does not provide clutch engaged option while executing in my case. Once you get the shell access, just provide the “ls command” to get a list of all the devices, as in the image below.
For Further assistance contact to [email protected]
CONCLUSION
As mentioned earlier the UART can be exploited successfully with adequate knowledge and by using right hardware and software tools. Exploitation can be achieved by exploring more into hardware section. The exploitation of UART in cameras leads to sniffing of data means your firmware details and even they can make some changes in the firmware level which a user/corporate cannot identify. By performing this the user may get an idea of infrastructure and this leads to exploitation of either an individual or an organization.
Resources
You may also be Interested on




