In this generation, most of us are always connected wirelessly using Wi-Fi, Bluetooth etc. These communication channels open the door for the intruders to conduct passive attacks, making the owner of the devices assumes that the device are malfunctioning.
CONTENTS:
- Introduction
- Radio Technology
- Classes Of Attacks In Radio Systems
- How Can These Attacks Be Prevented?
- How Briskinfosec Can Help You?
- Curious To Read Our Case Studies?
- Last But Not The Least
- You May Be Interested In
- Resources
Introduction:
RF remote controllers are used in most of the devices varying from remote control toy cars to heavy equipment’s used in mining operations and factory floors. The ubiquity and cost-effectiveness of RF hardware has made this innovation possible. We at Brisk Infosec, identified that most of the RF devices used in the market aren’t secure enough, thereby becoming the weakest link in the security chain.
Since these devices form an integral part of any industry infrastructure, it is necessary to secure these devices given its criticality. The consequences of these attacks can vary from sabotage to extortion.
In our research, we’ve found that RF has become a great target for intruders due to the ever-evolving needs in a wide variety of applications. We found that most of the devices used in a large scale cyber-physical system had less-to-no security when compared to that of a wireless garage door opener. With industries talking industry 4.0, where IoT and IIoT (Industrial Internet of Things) devices penetrate the market, securing the physical layer has obviously assumes importance. As IoT let these devices to be controlled over the internet, it is of paramount importance to at-least secure the physical layer of the entire system.
Radio Technology 101:
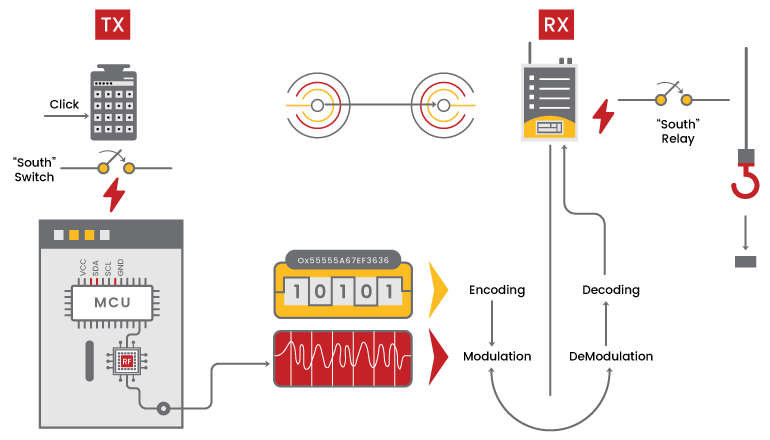
For any system to perform its role, there needs to be some data. In case of radio controller, the data is generated in the application layer just like all systems in practice. The application layer of a radio system consists of analog sticks and digital keys. Whereas in the case of an industrial remote controllers, it consists of an E-STOP button, to stop the device under risky conditions.
Now the obtained digital data needs to be line coded by using Return to Zero (RZ), Non-Return to Zero (NRZ), and Manchester coding schemes. This coded data is then modulated and up-sampled to intermediate frequencies, and then resampled to transmit at RF frequencies. This is the general workflow of any RF system in use. Sometimes, in many systems, due to small form factors, the baseband digital data is directly modulated and transmitted. The most general system block diagram is given below.
Classes Of Attacks In Radio Systems:
Now, as we know the basics of any radio system, let us next look into the different attacks that can occur in the radio system. The major classes of attacks used in a radio system are listed below:
- 1. Replay Attack
- 2. Command Injection
- 3. E-STOP abuse
With the mentioned classes of attacks, the major things that can occur in the radio layer are replay attack, command injection, E-STOP and wide range function abuse attacks. Malicious repairing and reprogramming attacks are not a category of radio layer attack as they involve access to the embedded hardware of the device as well and reprogramming its entire hardware base.
Replay Attack:
In this category of attack, the RF packet is simply recorded and replayed over the air to cause an effect at the receiver either be it a relay-clicking, or a bulb being turned on.
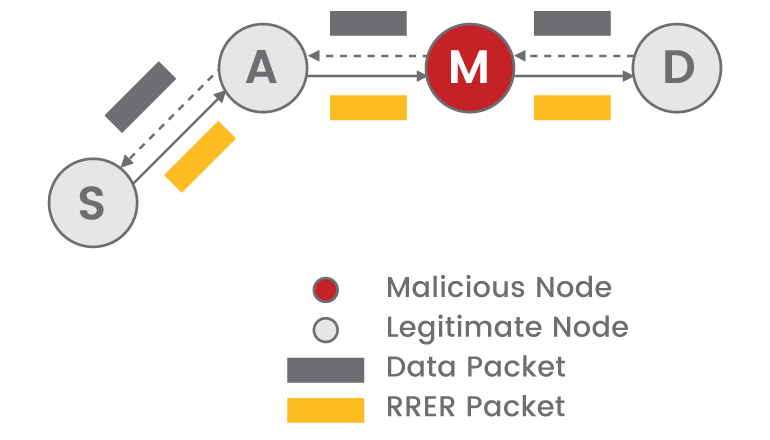
The above diagram is the most basic representation of a replay attack. The malicious user or the intruder captures the data in-between the devices and simply replays them to gain control of the device. This attack though simple can be deployed in various levels so that the data can be filtered and replayed with the intruder, emulating the entire transmitter.
Command Injection:
For conducting these sorts of attacks, the intruder needs to have knowledge of the layer-2 of the system. This means that the attacker needs to have a thorough understanding of the RF layer. This can be associated with the pressure that was applied in a certain key press or based on the data applied for a command, through which the intruder can forge packets for a different command and send it to the receiver, so the original command is not executed. We need to keep in mind that for performing a command injection attack, the attacker needs to first infiltrate the radio layer to perform this attack.
E-STOP Abuse And Wide Range Function Abuse:
The next two categories of attacks are of similar nature, but the outcome of this varies drastically as the working of the attack is different.
In the case of E-STOP abuse, it was noticed that the E-STOP packets are transmitted at a bit higher power when compared to that of a normal datagram packets. So, when an attacker needs to conduct this, he needs to capture the E-STOP data or sometimes, just simply transmit a dummy signal at a higher power to capture the channel and make the device unusable.
In the case of Wide Range Function abuse, the intruder next starts the data transmission from previously obtained data and uses the capture to craft custom packets and transmits the packet, thereby effectively taking control of the entire device.
How Can These Attacks Be Prevented?
The main way to prevent these attacks is to use a robust encryption scheme in the physical layer, and then mark the data link layer with a sequence counter such that previous packets do not get processed thereby preventing replay attacks completely. Some devices that we encountered used proprietary L2 protocols didn’t have enough hardening. Hence, we discourage the use of such protocols as these things aren’t field tested.
Another major fix that can be applied is to use hopping techniques where we can hop the frequency. But we need to keep in mind that with hopping, we need to have a powerful hardware that can actually chase the channel and not lose its synchronization.
How Briskinfosec Can Help You?
Briskinfosec provides contemporary and reliable wireless security assessments for strengthening and safeguarding the security of wireless devices. Our security professionals use best encryption schemes, thereby maintaining layer-wise security for any wireless systems. Further, practical awareness on how to stay adroit against such threats will also be demonstrated.
Curious To Read Our Case Studies?
Our case studies will tell you about the successful security strategies executed by us during the process of identifying and eliminating security vulnerabilities. Go ahead and read out our case studies now.
Last But Not The Least:
The best way to fleet from insanity is to seek towards sanity. Well, if you’re on a behemoth mission to see and learn about the world wide happened cyberattacks, the impacts they’ve caused to firms, the compromises made by firms to regain their lost data, and for much more, then the sanest choice to get all of these within a snap is through Threatsploit Adversary report. It’s a report that’s created and offered to the world by Briskinfosec, just to impart awareness and caution people about the notoriety of cyber breaches. Also, the best mitigation measures are provided to stay away from such threats. What else? Just read it and get yourself enlightened!
You May Be Interested In:
Resources