Contents:
- Introduction
- Package Details
- API Information
- Android flags
- Permissions
- *User permission
- *App permission
- App components
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case studies?
- Last but not the least
- You may be interested on
Introduction:
Android Manifest file provides the system with necessary data like application’s configuration information, permissions, and app components. Android Manifest File can be obtained by extracting any APK File and also while doing assessment, you can use APKtool & Drozer for extracting the Manifest file from the application.
Package Details:
In Manifest file, the first thing to analyze is the application package details, which will be useful throughout the assessment. Followed by the application package name which is different from the app name. This package name is used by system. For example, data of the application will be saved with the application’s package named folder inside the “/data/data/” path. Apart from that, you can find the buildversion and buildversion code.
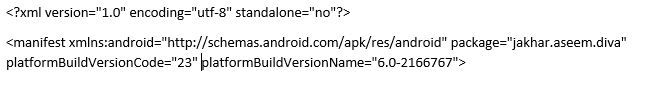
API Information:
The API level expressed by an application will be compared with the given Android version. API level is a single integer, and it can vary based on different Android OS versions. Here, it’s been assigned based on the minimum targeted and maximum SDK version and they are decided by the developer based on their app requirements.
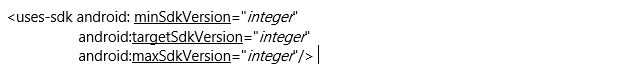
The figure below is an indication of a recent survey made by Google revealing that Active devices below API 19 (kitkat) are less than 4% which confirms that Google will no longer give support for those versions, and using those below API 19 is not advisable for security concerns. Refer the more details for API versions. (https://developer.android.com/about/dashboards).
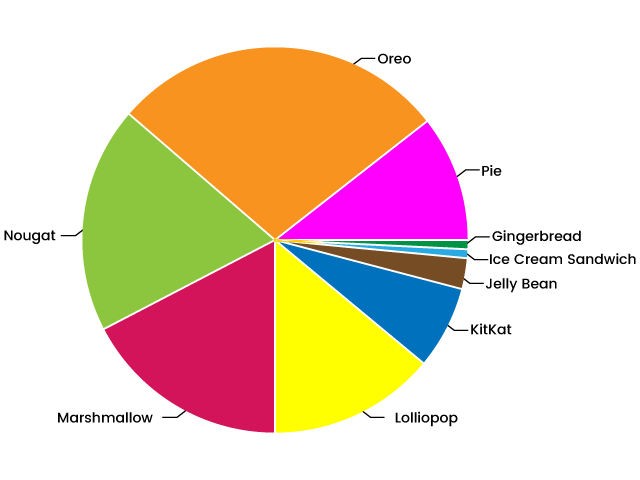
Android flags:
In application element, different components are there to declare. In security view, we need to check the following two components:
BACKUP MODE ENABLED:
The name usually describes the automatic enabling of the backup data. The backup mode allows backup option, as the attacker can take the backup of your data as well, steal sensitive information from and using your application, making it a vulnerable one. According to the security purpose, the google drive is the default storage place of the app backup’s and the backup option code that’s available in the manifest file is as follows:
< application… android: allow Backup = ”true” > < /app>
Prevention: Backup mode should be set false to prevent this kind of attacks.
DEBUG MODE:
The debug mode defines whether the applications are debuggable or not. Also, when the debug is enabled, the attacker can gather plenty of information. In Staging environment, when the app is not in production state, it can be set as true, and once when it moves to the final stage for execution, it should be set as false. It’s one of a critical vulnerability which leads anyone to capture sensitive information of an application.
Debug code available on manifest file
< application android: debuggable = "false" < /application>
Permissions:
An app can use anything that is created for it without requiring any permission. But to use any data, hardware, and software that doesn’t belong to it, it must get the permission for using the above needs. For example, if an application needs device camera or GPS, it must first get permission to access it. As a developer, they have to mention the permission to use the camera which is not owned by the application.
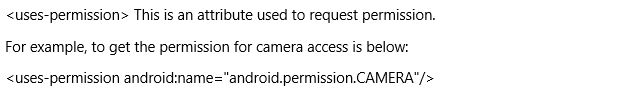
Hardware permissions can be declared in elements for google play to discover the application requirements and also for user’s privacy.
USER & APP PERMISSION:
Specifies system permission which the user must grant to run the app correctly. The user grants permissions either when the application is installed (on devices running Android 5.1 and lower) or while running (on devices running Android 6.0 and higher).
APP Permission is used to protect the privacy of the Android user. Android apps must request permission to access sensitive user data like SMS, CONTACTS and other certain features like (CAMERA, INTERNET, and WIFI) etc.
Permission request for any kind of APP is assigned in the manifest file of an APK file. In daily usage, you will be facing permission request whenever needed from the application for reasons like accessing folders like contacts, SMS, internet, etc., and their permissions are mentioned as shown below:
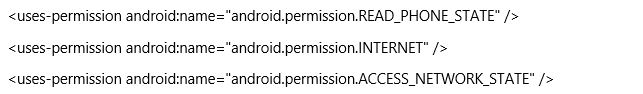
If an app has a typical kind of information, then the lower level of permissions can be used. But if your app contains any sensitive level of information, then you have to assign the above code for the security purpose.
APP PERMISSIONS:
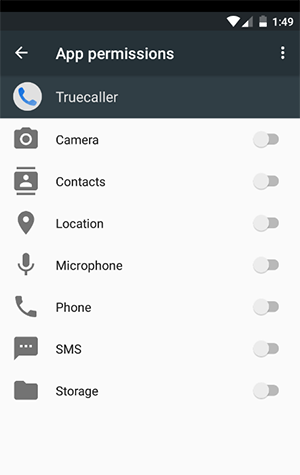
The above figure tells about the various permissions that have generally been allocated to an app and here I’ve checked the different authorities that are used for the Truecaller app. In this list of options, you can enable the required permission which you need to set for the app by default. Once you’ve selected any one of these permissions, it won’t ask for those permissions from the user. But, if you haven’t enabled any permissions, then it will ask for the app permissions every time like the diagram as follows.
DEFAULT APP PERMISSIONS:
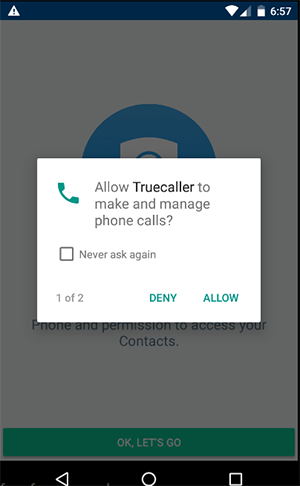
With permission elements, as a security professional, we have to look for dangerous permissions like the following but not just them alone.
- WRITE_EXTERNAL_STORAGE for writing data to external storage like SDcard.
- READ_LOGS permission for reading all the application logs.
- READ_ONLY or WRITE_ONLY permission for content providers.
APP COMPONENT VULNERABILITY:
There are four application components:
- Activity
- Services
- Content provider
- Broadcast receiver
These app components can be either private or public. The exported attribute in each component declaration on the manifest file defines that the component is either private or public.
If the component is public, it can be exported to the other apps. But if the component is private, then it cannot be accessed by other apps and this kind of export options should be reviewed for all of those components. Otherwise sensitive data from any component can be accessed from other third-party application. Intents can also be used to launch app components. Exporting can be defined in the following ways:
Using Exported tag:

To prevent app components attacks, review the exported components and if it’s necessary, then set the “permission” attribute to require a certain permission for accessing component. If not, then don’t export the components.
Conclusion:
As we’ve seen above, these are the most common ways to analyze the manifest file. If you choose to do it in automated way, you can use the static analysis tools like MobSF, Androbug & Qark but has dangers like false positives. But if you choose the manual way, you can follow the MAST standard and OWASP framework. Most importantly, a proper and complete mobile security assessment is mandatory.
How Briskinfosec helps you?
Briskinfosec provides a complete and competent mobile security assessment that fully assesses the security environment of your mobile devices/applications. With regards to that, Briskinfosec has its own mobile framework NCDRC-MAST (National Cyber Defense and Research Center – Mobile Application Security Testing) for doing mobile related security assessments, ZTF (Zero Trust Framework), and an own operating system named BIMOS (Brisk Intelligence Mobile Operating System). We also conduct malware analysis to detect the presence of any backdoor and other malware apps through our security veterans. Finally, practical awareness on all such related threats will be provided.
Curious to read our case studies?
Briskinfosec has earned the reputation as one among the top 20 most promising cybersecurity providers. This is primarily due to our spectacular fashion of eliminating the security vulnerabilities. To acknowledge the successful strategies used during security assessments, read our case studies now.
Last but not the least:
As a dedicated cybersecurity company, we’ve always visualized a “cyber-risks free world.” We know that to convert this dream into reality is really a herculean task that requires the contribution of every soul in this earth. As our contribution, we prepare a report named as Threatsploit Adversary report.. It’s a single report that contains the global collection of significant cyberbreaches, its impacts, the sufferings of companies and much more. Also, the best mitigation measures are suggested for you to remain safe against them. It’s an evidence of how much we care for the digital safety of people. With great efforts, this report is prepared. But, it’s just a click away from being opened and read. Just read it as its solely prepared for you.
You may be interested on:
- Getting Started with Frida
- Top Mobile App Security Best Practices
- Do you know connected clouds?
- Cyber Security Products Vs Cyber Security Services


