What is Phishing
Phishing is a type of social engineering attack used to obtain sensitive information from users, such as login credentials and credit card information.It occurs when an attacker impersonates a trustworthy entity and persuades a victim to open an email, instant message, or text message.Following that, the recipient is duped into clicking a malicious link, which can lead to malware installation.The freezing of a system as part of a ransomware attack, or the disclosure of sensitive information.
An attack has the potential to be extremely damaging.Individual examples include unauthorized purchases, money theft, and identity theft.
Furthermore, phishing is frequently used to gain a foothold in business or government networks as part of a larger attack, such as an advanced persistent threat (APT) event.In this scenario, employees are compromised in order to circumvent security perimeters, distribute malware within a closed environment, or gain privileged access to protected data.
A company that is the target of such an attack usually suffers significant financial losses as well as a loss of market share, reputation, and consumer trust.A phishing attempt, depending on its scope, could turn into a security disaster from which a company will struggle to recover.
How a corporate employees are targeted ?
Employees at all levels of a company can be duped, so no one should believe they are immune to phishing attacks.Scammers can easily obtain company email addresses, organisational hierarchy, and projects that different teams are working on by browsing a firm's website or social media page.They may use a variety of names, job titles, and coworker names to trick consumers into falling for phishing schemes and providing the information required to access business systems.
How Individuals are targeted ?
Whaling is a term used to describe this type of phishing attack. Whaling is a highly targeted phishing attack that masquerades as a legitimate email and targets senior executives.
Whaling is a type of digitally enabled social engineering fraud that encourages victims to perform a secondary action, such as initiating a wire transfer of funds.
How phishing is customized based on age group ?
Adolescents are the most likely victims of phishing.Teenagers are especially vulnerable to phishing attempts because they are often more careless and trusting; they are also more technically aware nowadays and can often easily circumvent parental controls and prohibitions.
They are one of the groups that makes greater use of internet programmers, ranging from social networking to gaming apps and multimedia sharing sites.
Malware-based phishing is still a common method for obtaining sensitive data illegally, as is impersonating a legitimate entity or friend in order to persuade others to provide the desired information. Young adults make a lot of contacts through their preferred communication channels, social networks and smart-phones, which can easily expose them to both threats.
Types of Phishing
What is Spear Phishing
Spear phishing, as opposed to random application users, targets a specific individual or company. It is a more sophisticated form of phishing that requires a thorough understanding of an organization's power structure.
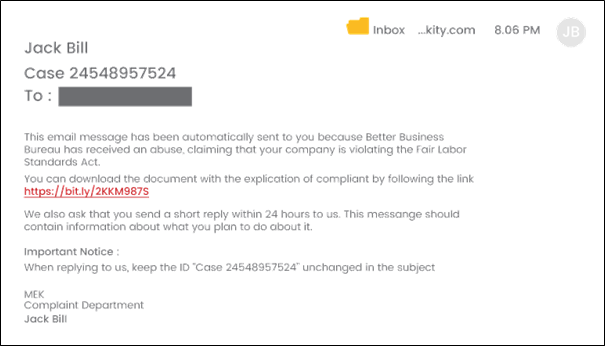
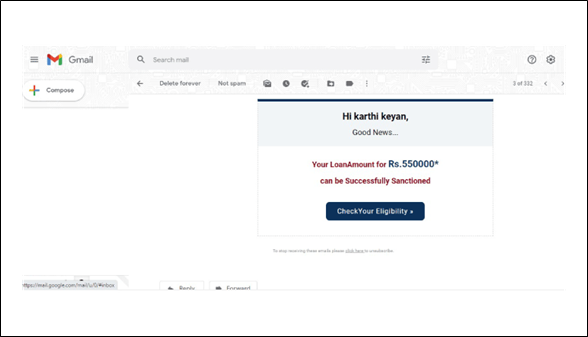
Below is an example of a spear phishing email.Take note of the recipient's industry, the download link that the victim is required to click, and the need for a quick response.
What is smishing?
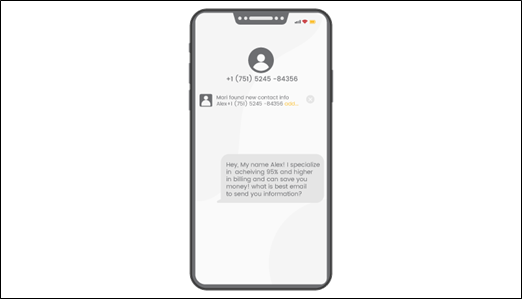
Smishing is a type of text messaging or short message service attack (SMS).A common smishing technique is to send an SMS message to a cell phone that contains a clickable link or a return phone number.
A common example of a smishing attack is an SMS message that appears to have come from your bank.It notifies you that your account has been compromised and that you must respond immediately.The attacker requests that you confirm your bank account number, Social Security number, and other personal information.After receiving the information, the attacker now has control of your bank account.
What is vishing?
Vishing accomplishes the same goal as other phishing schemes.
The attackers are still looking for sensitive personal or corporate information.This attack is carried out via voice call.A call from someone posing as a Microsoft representative is a common vishing attack.
This individual informs you that a virus has been discovered on your computer.You are then asked for credit card information so that the attacker can update your computer's anti-virus software.
Your credit card information has now been compromised, and you have most likely installed malware on your computer.
What is email phishing?
Email phishing, which has been around since the 1990s, is the most common type of phishing.These emails are sent by hackers to any address they can get their hands on.The email usually informs you that your account has been compromised and that you must respond immediately by clicking on a link provided.The language in the email frequently contains spelling and/or grammatical errors, making these attacks obvious.
Some phishing emails are difficult to detect, particularly when the wording and grammar are carefully prepared.You can tell if the source is authentic by looking for suspicious wording in the email source and the link you're being directed to.
What is search engine phishing?
To get the first result on a search engine, hackers use search engine phishing, also known as SEO poisoning or SEO Trojans.You'll be taken to the hacker's website if you click on their link in the search engine.
Threat actors can steal your information if you interact with the site and/or enter sensitive data.Hacker sites can imitate any type of website, but the most common targets are banks, money transfer sites, social media sites, and shopping sites.
What are all the online phishing database available for better awareness
There are some online sites where we can check to see if the link or file shared with us contains any malicious code.
PhishTank
On PhishTank, a free community platform, anyone can report, verify, track, and exchange phishing data.It provides accurate, actionable information to anyone looking for bad actors, whether for themselves or others (i.e., building security tools).PhishTank is managed by Cisco Talos Intelligence Group (Talos).
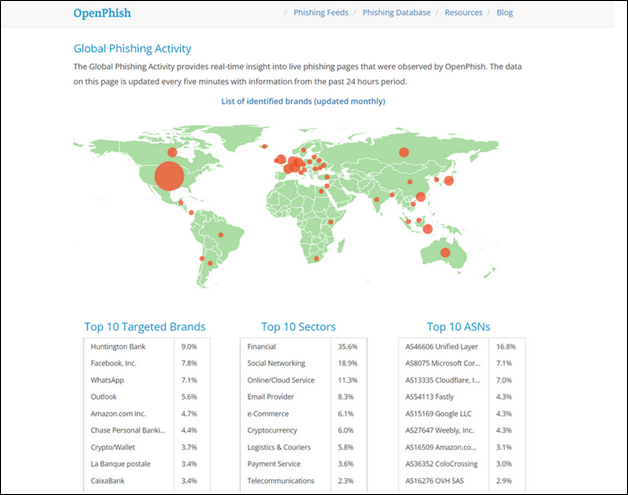
OpenPhish
The OpenPhish service provides real-time information about active phishing threats.It also includes a free community feed that is updated every 12 hours with a list of phishing URLs.Premium OpenPhish feeds are refreshed every 5 minutes and contain additional information such as targeted brand, industry, page language, country, and more.
How to prevent from phishing attacks
- Educate your employees and hold training sessions on phishing scenarios.
- Install a SPAM filter capable of detecting malware, blank senders, and other types of spam
- Maintain the most recent security patches and updates on all systems.
- Install an antivirus solution, schedule signature updates, and monitor the antivirus status on all of your devices.
- Create a security policy that addresses, among other things, password expiration and complexity.
- Install a web filter to prevent access to potentially harmful websites.
- All critical company information should be encrypted.
- HTML email messages can be converted to text-only email messages or disabled entirely.
- Employees who work from home should be required to use encryption.
A company can take several steps to protect itself from phishing. They must monitor current phishing tactics and ensure that their security policies and solutions are capable of keeping up with evolving threats.
It is also critical that their personnel understand the various types of attacks that can occur, the risks they face, and how to respond to them. When it comes to phishing attempts, having knowledgeable personnel and secure systems is critical.
Phishing is a social engineering attack that is commonly used to obtain sensitive information from users, such as login credentials and credit card information.It occurs when a hacker impersonates a trustworthy entity and persuades a victim to open an email, instant message, or text message.Following that, the recipient is duped into clicking a malicious link, which can result in malware installation, system freeze as part of a ransomware attack, or the disclosure of sensitive information. Please be aware & in case of queries reach out to us



