Most of the personnel’s believe that cloud services are one hundred percentage secure as it is from industry giants, but the reality is being a cloud native won’t completely save you from external threats. This is because certain practices are still in our hands and it is our responsibility to rectify security problems. Eg: storage drives, API keys, and internal communication system. We can never predict when we are going to be the victim of an cyberattack. In this blog, you’ll gain a deep knowledge on cloud security threats and countermeasures to prevent them.
Contents:
- Importance of cloud security
- Cloud security loopholes
- Securing the infrastructure
- End Users Responsibilities
- How Briskinfosec helps you?
- Curious to read our case study?
- Last but not the least
- You may be interested on
Importance of Cloud Security:
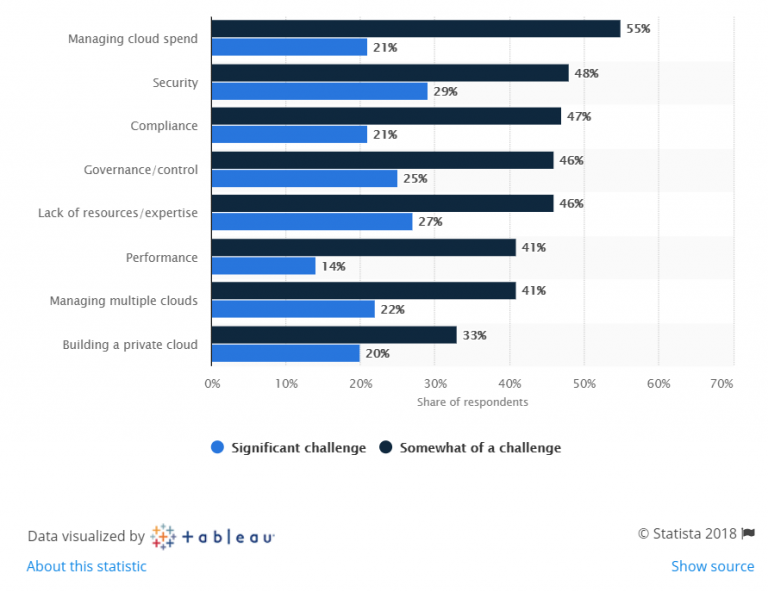
In today’s world, every large scale and small-scale organizations move their environment to cloud as they feel it is cost effective and safe. It’s 2019, yet organizations find it difficult to tackle security issues. Statistical survey report of 2018 says, countless organizations find security as a challenge.
In the year 2017, Accenture’s 4 AWS S3 storage buckets, which were kept for public access was found to be unsecured as it exposed the names, addresses, account details, and pin numbers of millions of US-based Verizon customers. It was identified that the buckets disclosed these data to anyone who enters the buckets web address in the browser. Buckets - titled with the AWS subdomains, “acp-deployment,” “acp-collector,” “acp-software,” and “acp-ssl”, revealed significant internal Accenture data, including cloud platform credentials and configurations. This prompted Vickery to notify the corporation. The four AWS buckets were secured the next day. In the same year, Verizon data was leaked by its vendor, ‘Nice System’. The reason for this was found to be because of poor security misconfigurations.
Cloud Security Loopholes:
Major Security loopholes:
Loss of data while migrating to the cloud:
Loss of data is seriously a real threat to an organization when it falls in the wrong hands. Loss of data can be very much possible at the initial stage of cloud adoption as the platform for data changes. Data security in cloud computing technology is a must.
Cloud Infrastructure:
When an organization newly adopts to cloud technology at the initial stage, there could be security misconfiguration issues which creates a good possibility for data tampering. The cloud providers spend millions on security but still data breaches happen. 90% of the time, it’s due to the employee’s fault because they log into their cloud solutions account from mobile phones, tablets, and desktops or PCs, hence making the system more vulnerable to various external threats.
Poor authentication:
Multilayered authentication must be implemented to stall hackers. Phishing and social engineering attacks may trick the user to obtain the credentials.
Access control:
Only authorized user should access the cloud environment, application, and data.
Encrypt Sensitive details:
Cloud application uses API for accessing services, databases, and applications where these sensitive data must be encrypted.
Securing the Infrastructure:
Password Control:
Educate the user about strong password policy and not to share password with anyone.
Vulnerability Management:
Regularly scan for vulnerabilities and perform Penetration Testing to find out the real-world threats. Report and patch the vulnerability on regular intervals.
Encryption:
Make sure that your data is encrypted in both static and dynamic state.
Data Recovery:
Be aware of the data backup, retention, and recovery policies and processes for your cloud vendor.
Monitoring:
Ensure you have continual security monitoring in place across all environments and instances.
End Users Responsibilities:
Review default settings:
Most of the time, certain settings come with default options by the provider. So, never assume that your vendor will take complete care of your security. Hence, it’s better if you configure your own security policies rightly. Remember, it’s you who must eat when hungry. Similarly, it’s you who must care about your security, if you truly need it.
Authentication Configurations to your Organization
All locations where data will be uploaded should be password-protected. Strict password policy should be implemented.
Don’t Assume Your Cloud Data is Safe
Never think that your data in cloud is safe and encrypted. Make sure that your data is encrypted, both at rest and transit.
Check your Cloud Data Retention Policy
Understanding your cloud vendor’s data retention and deletion policy is essential. Imagine what happens when the vendor is able to access the data even after deleting it? Is there any chance that the data can be cached or copied? Review and verify your vendors policies before hoping in the cloud for the best.
Isolate Your Cloud Resources
Have separate admin accounts for development, deployment, testing, etc. In that way, if a hacker accesses and manipulates one account, he or she cannot hop on to other aspects of the environment.
Conclusion:
Your cloud vendor will provide you the basic security utilities that you run in your cloud. But, proper security assessment will show case all the vulnerabilities and various ways a hacker can gain foothold in your cloud. Apropos of that, the user must be given pompous knowledge on security and social engineering attacks.

How Briskinfosec helps you?
Briskinfosec provides efficient cloud security assessments that identifies the vulnerabilities in cloud applications and eliminates them, preventing your services from getting disrupted. Apropos of this, Briskinfosec
- Keeps your Cloud security applications in an updated manner.
- Ensures you follow your cloud process related checklist consistently and if not, assists you in following righteously.
- Implements proper and legitimate security policies.
We’ve been listed as one among the “Top 20 Most Promising Cyber Security Provider” by the “CIO Review” consistently for 2 years. We’ve also set the “India Book of Records for identifying most number of vulnerabilities”.
Curious to read our case study?
Our stakeholder, one of the prominent commercial marketing agents and cloud application providers wanted us to perform cloud security assessments on all their cloud applications. We assessed their entire applications, identified the flaws, and eliminated them. Also, we also provided awareness on cloud related threats. Check out our case study to know further.
You may be interested on:

