Introduction:
A type of internet-based computing that provides shared computer processing resources and data to computers as well as other devices are on demand. Cloud is a large server on which different services and datum are stored and one can access it, whenever required. The availability of high-capacity networks, low-cost computers and storage devices as well as the widespread adoption of hardware virtualization, service-oriented architecture, and autonomic and utility computing have led to the growth in cloud computing.
Contents:
- How does cloud works?
- Characteristics
- Security issues in cloud
- Service models
- Deployment models
- What is cloud security?
- Security concerns for cloud based services
- Top cloud security threats
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case study?
- Last but not the least
- You may be interested on
How does cloud works?
In most simple terms, imagine the cloud as something similar to a local storage service in order to safeguard your datum. Example- Residence (where things are kept safely). Now, you can be relaxed and comforted as there is a storage place for your data, where top security is a guarantee.
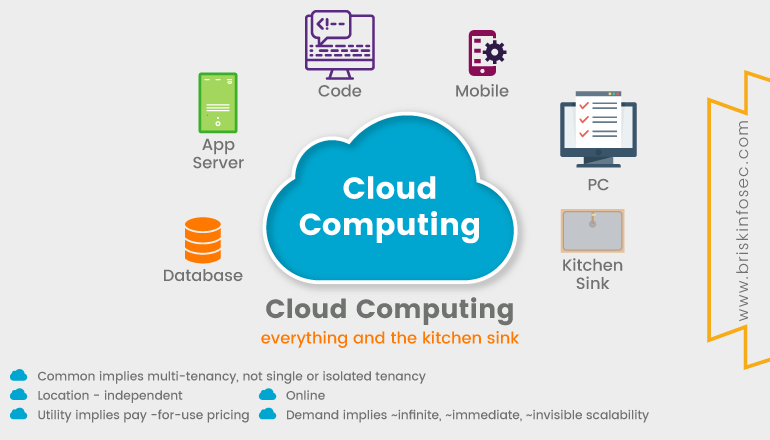
Characteristics:
Cloud computing exhibits the following key characteristics:
The organizations must improve cloud computing services as it increases the users flexibility with re-provisioning, adding as well as in expanding technological infrastructure resources.
Cloud has three distinct components. They are cited below:
-
Client Computers
-
Distributed Servers
-
Datacenter
Client Computers
Clients are devices that the end user interacts with cloud (mobile, thick client, thin client).
Distributed Servers
Often servers are in geographically different places, but server acts as if they are working next to each other.
DataCenters
It is a collection of servers where application is placed and is accessed via internet.
Security Issues in Cloud:
The security issues in the cloud are classified into two different categories
- Security issues related to cloud service providers.
- Security issues related to users lethargy during the change of service provider.
The responsibility of the provider is to ensure that their infrastructure is secured and their client’s data is protected with different authentication measures. When the organizations opted to host their applications on the public cloud, the sensitive data is at risk. The problem in cloud computing environments are the concerns regarding to competent security.
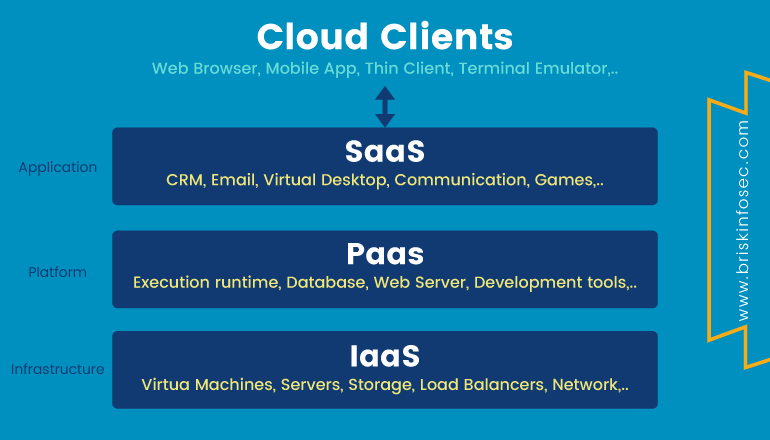
Service Models:
- SaaS (Software as a Service)
In Software as a Service models, user gains access to application software and database. Cloud providers manage the infrastructure and platform that runs the application.
- PaaS (Platform as a Service)
In Platform as a Service models, cloud providers deliver a computing platform that typically includes the operating system, programming-language execution environment, database, and web server. PaaS is offered by top class firms like Microsoft Azure and Oracle cloud platform.
- IaaS (Infrastructure as a Service)
Infrastructure as a Service models refer to online services that provides high level APIs used to dereference various low-level details of underlying network infrastructure like physical computing resources, location, data partitioning, scaling, security, backup etc.
Deployment Models:
Public Cloud:
A public cloud is a publicly accessible cloud environment owned by a third-party cloud provider. The IT resources on public clouds are usually provisioned via the previously described cloud delivery models and are generally offered to cloud consumer at a cost (or) are commercialized via other avenues. Provider companies offer resources as a service on a free of charge, or on a pay per use basis, via internet connection.
The pros of a public cloud are:
- Unsophisticated setup and use
- Easy access to data
- Flexibility to add and reduce capacity
- Cost-effectiveness
The cons of a public model:
- Data security and privacy
- Compromised reliability
- The lack of an individual approach
- Private Cloud:
There is little to no difference between public and private clouds from the technical point of view as their designs are very similar. However unlike in the public one, only one specific company owns a private cloud which is why it is also called internal or corporate. As these data center architectures reside within the firewall, they provide enhanced security.
Even though one organization runs its workloads on a private basis, a third party can also manage it and the server can be hosted externally or on premises of the user company.
The pros of a private cloud are:
- Individual development
- Storage and network components are customizable
- High control over the corporate information
Hybrid Cloud:
As it’s usually the case with any hybrid phenomenon, a hybrid cloud encompasses the best features of the above-mentioned cloud computing deployment models like public, private and community ones. It allows companies to mix and match the facets of all three types that best suits their requirements.
Hybrid deployment architectures can be complex and challenging to create and maintain, due to the potential disparity in cloud environments and the fact that management responsibilities are typically split between the private cloud provider organization and the public cloud provider.
The benefits of a Hybrid cloud are:
- Improved security and privacy
- Enhanced scalability and flexibility
What is Cloud Security?
Cloud security includes the ecosystem of people, processes, policies and technology that protects data and applications, operating in the cloud. Cloud security consultants examine how an enterprise processes and stores data and how it crafts a custom data-governance protocol, for comprehensive protection.
The Professional cloud security assessments and penetration testing are instrumental in helping to ensure the cloud-service providers meet government compliance to responsibly protect your valuable data.
Security Concerns for Cloud-Based Services
The cloud has opened up a whole new frontier for storage, access, flexibility and productivity. Since the introduction of cloud computing, more and more companies have been steadily switching to third-party cloud computing providers as they are aware of these top 6 security concerns illustrated below:
Top Cloud Security Threats:
Cloud providers are a prime target for malevolent hackers. Experts at the Cloud Security Alliance have identified the following 6 critical issues to cloud security such as:
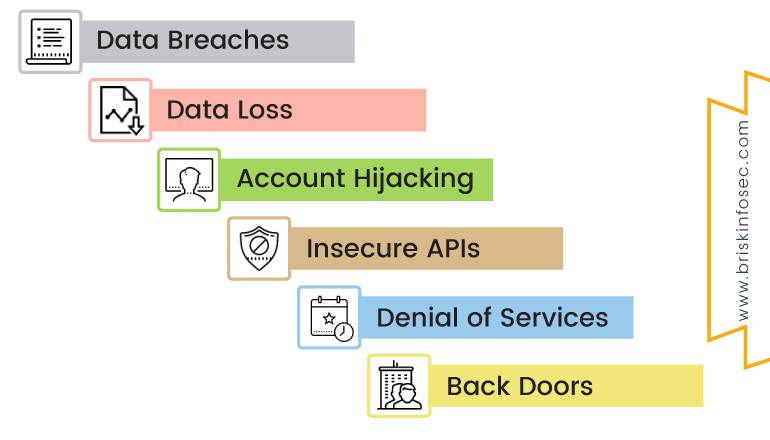
Data Breaches:
A study conducted by the Ponemon Institute entitled “Man in Cloud Attack” reports that, over 50 percent of the surveyed IT and security professionals believed their organization’s security measures to protect data on cloud services, are low. This study used nine scenarios where a data breach had occurred to determine if that belief was found in fact.
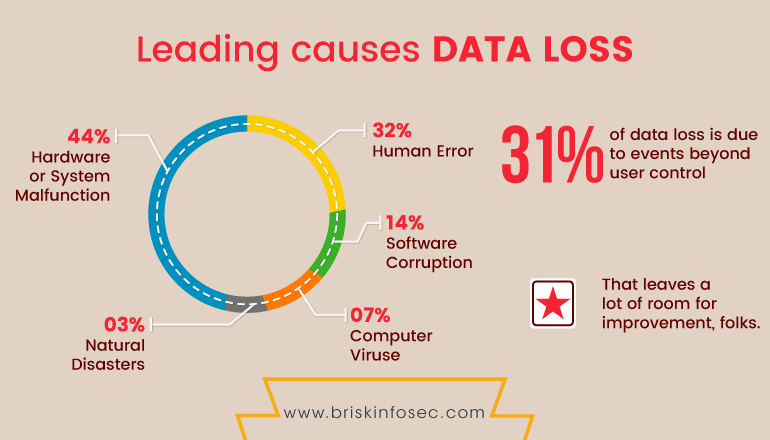
Data Loss:
Data on cloud services can be lost through a malicious attack, natural disaster, or through a data wipe caused by the service provider. Losing vital information can be devastating to businesses that don’t have a proper recovery plan.
Hijacking of Accounts:
Attackers now have the ability to use your (or your employees’) login information to remotely access sensitive data stored on the cloud. Additionally, attackers can falsify and manipulate information through hijacked credentials.
Insecure APIs
Application Programming Interfaces (API) give users the opportunity to customize their cloud experience. However, insecure APIs can be a threat to cloud security because of their nature. Not only do they give companies the ability to customize features of their cloud services to fit business needs, but they also authenticate, provide access and effect encryption.
Denial of Service (DoS) Attacks:
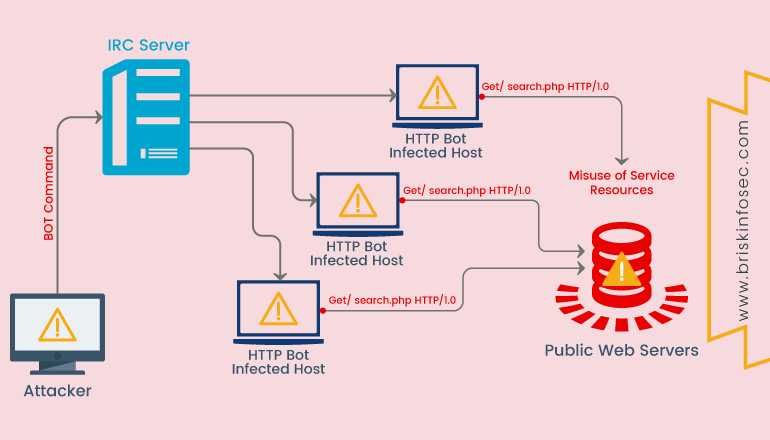
DoS is also used as a smokescreen for other malicious activities, and to take down security appliances such as web application firewalls. They also attempt to make your website and servers unavailable to legitimate users.
Back doors:
Backdoor is a way to access a computer system or encrypted data that bypasses the system's customary security mechanisms. Backdoors are also commonly put into place through malware. A malware module may act as a backdoor itself.
Conclusion
In this blog, we have provided a basic definition of cloud computing and discussed about the security issues/concerns related to public clouds, private clouds and hybrid clouds. Further, different kinds of issues related to cloud deployment models are also discussed. The three-cloud models have their own merits and challenges. Therefore, security will obviously be a necessity.
Cyber Quote On Cloud Security:

How Briskinfosec helps you?
Briskinfosec provides efficient cloud security assessments that identifies the vulnerabilities in cloud applications and eliminates them, preventing your services from getting disrupted. Apropos of this, Briskinfosec
- Keeps your Cloud security applications in an updated manner.
- Ensures you follow your cloud process related checklist consistently and if not, assists you in following righteously.
- Implements proper and legitimate security policies.
We have been listed as one among the “Top 20 Most Promising Cyber Security Provider” by the “CIO Review” consistently for 2 years. We have also set the “India Book of Records for identifying most number of vulnerabilities”.
Curious to read our case study?
Our stakeholder, one of the prominent commercial marketing agents and cloud application providers wanted us to perform cloud security assessments on all their cloud applications. We assessed their entire applications, identified the flaws, and eliminated them. Also, we also provided awareness on cloud related threats. Check out our case study to know further.
Last but not the least:
Read our Threatsploit Adversary report. It contains the monthly collection of cyber breaches, its impacts on the respective organizations, and the type of loss experienced. Our report will surely be useful, if you want to perceive sight on significant global cyberattacks in just one click.
You may be interested on:

