Introduction
The protection of software applications against potential flaws and security breaches in today's digital environment depends on using secure coding practices. You have a special opportunity to guide and influence the development team in putting effective security measures in place as a security specialist employed by a security organization. In this blog article, we'll look at how to leverage security team tools, construct secure code guidelines that all developers can adhere to, and audit and access secure code practices successfully.
Secure code review guidelines
Understand Security Requirements
- Review and recognize the precise protection requirements applicable to your venture.
- Familiarize yourself with relevant safety frameworks, together with the OWASP Top 10, CWE/SANS Top 25, or industry-unique recommendations.
Review Code for Security Vulnerabilities
- Conduct a thorough evaluation of the codebase to identify potential safety vulnerabilities.
- Look for common vulnerabilities, which include injection flaws (SQL, command, and LDAP injection), go-website scripting (XSS), move-website online request forgery (CSRF), insecure direct item references, and insecure cryptographic practices.
Follow Secure Coding Practices
- Ensure that the code follows stable coding practices throughout.
- Validate and sanitize all consumer entries to prevent injection attacks and ensure factual integrity.
- Implement output encoding to save your go-website scripting vulnerabilities.
- Utilize strong and well-applied authentication and authorization mechanisms.
- Apply secure session management strategies, inclusive of the usage of random and unique session identifiers, implementing session timeouts, and properly invalidating periods.
Check for Secure Configuration
- Review configuration documents and settings to make sure they're well configured for protection.
- Verify that touchy facts, which include passwords and API keys, are not uncovered in configuration documents or in the code.
- Ensure that security-associated configurations, like TLS/SSL settings, are successfully carried out.
Identify Data Sanitization and Escaping
- Verify that all person-supplied records are efficiently sanitized and escaped while used in queries, command execution, or displayed on web pages.
- Use organized statements, parameterized queries, or ORM frameworks to avoid SQL injection vulnerabilities.
- Apply the right encoding strategies.
Using security team tools to practice secure code
Free Tools used for Standard Application Security Testing (SAST)
SAST tools can examine source code or compiled code without actually running it. They aid in locating potential coding flaws and security issues.
SAST tools search the codebase for patterns and known vulnerabilities as they scan it. These tools examine the organization of the code, the flow of the data, and any potential issues, such as injection attacks or unsafe encryption implementations.
Free equipment might also not perform optimally due to elements like compatibility, maintenance, restricted functions, and community assistance. Evaluate their suitability primarily based on your specific requirements and consider opportunities or business solutions if essential.
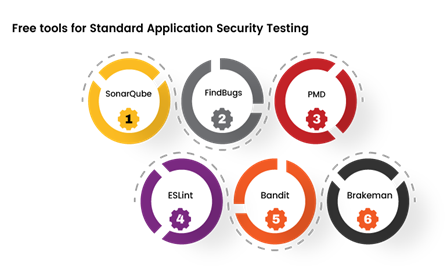
SonarQube:
SonarQube is an open-source platform that offers continuous code inspection. It supports a couple of programming languages and gives an extensive range of static code analysis guidelines. SonarQube can stumble on safety vulnerabilities, insects, code smells, and other exceptional troubles. It affords particular reports and integrates properly into the improvement technique.
FindBugs:
FindBugs is a popular static evaluation tool for Java code. It analyzes compiled Java bytecode to identify ability bugs and protection vulnerabilities. FindBugs makes use of a fixed set of predefined rules to flag problems, including null pointer dereferences, the use of insecure APIs, and more.
PMD:
PMD is a versatile source code analyzer that supports a couple of programming languages, including Java, JavaScript, and others. It enables the perception of not unusual coding mistakes, capacity vulnerabilities, and overall performance issues. PMD offers an extensive variety of policies and customizable configurations.
ESLint:
ESLint is a quite customizable static evaluation device, particularly designed for JavaScript code. It enforces coding requirements, detects ability-safety vulnerabilities, and gives tips for code upgrades. ESLint has a large set of configurable regulations and supports diverse plugin integrations.
Bandit:
Bandit is a safety-focused SAST tool built for Python code. It focuses on detecting common protection problems and vulnerabilities in Python programs. Bandit scans the source code and presents signals for capacity problems like insecure use of cryptographic features, SQL injections, and more.
Brakeman:
Brakeman is a static evaluation tool particularly designed for Ruby on Rails programs. It scans Rails code to perceive safety vulnerabilities, including code injections, go-web page scripting (XSS), and more. Brakeman provides certain reviews with vulnerability statistics and guidelines for remediation.
Free Tools for Dynamic Application Security Testing
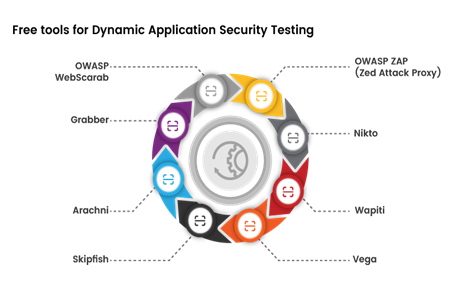
OWASP ZAP (Zed Attack Proxy):
OWASP ZAP is a widely used open-source web software security scanner. It provides complete scanning abilities, which include automated vulnerability detection, active and passive protection testing, and aid for diverse assault vectors. OWASP ZAP provides an interactive GUI and a robust API for integration with different equipment and workflows.
Nikto:
Nikto is an open-supply net server scanner that focuses on identifying capability vulnerabilities and misconfigurations in net servers. It scans for not unusual troubles, including outdated server software, insecure configurations, and acknowledged vulnerabilities. Nikto offers a command-line interface and generates unique reviews with actionable pointers.
Wapiti:
Wapiti is a command-line vulnerability scanner designed to assess the security of internet packages. It plays black-field checking out, studying the application's reaction to various attacks to pick out capacity vulnerabilities like XSS, SQL injection, and record inclusion. Wapiti is customizable and affords alternatives for authentication, custom scripts, and output codecs.
Vega:
Vega is a loose and open-source internet vulnerability scanner and testing platform. It provides a user-friendly GUI that lets testers configure and customize scans in line with their precise necessities. Vega scans for an extensive variety of vulnerabilities, such as XSS, SQL injection, and directory traversal. It presents special scan reports and permits similar guides for trying out and analyzing.
Skipfish:
Skipfish is a web utility safety scanner developed by Google. It employs a quick scanning technique to identify capabilities, vulnerabilities, and safety problems. Skipfish performs a thorough HTTP/HTTPS evaluation and includes a hard and fast of energetic and passive protection exams. It generates exact reviews with findings and suggestions for remediation.
Arachni:
Arachni is a feature-rich net application security scanner that mixes both automatic and guided testing abilities. It helps with a huge range of vulnerabilities, including XSS, SQL injection, and file inclusion. Arachni is especially customizable and can integrate with different tools and frameworks. It offers both a command-line interface and a web-primarily-based user interface.
Grabber:
Grabber is an open-source net scanner designed for efficiency and ease of use. It performs safety scans for numerous vulnerabilities, which include XSS, SQL injection, and command injection. Grabber supports multi-threading for faster scanning and gives specific reviews with recognized vulnerabilities.
OWASP WebScarab:
WebScarabis an open-supply device developed with the aid of OWASP that focuses on intercepting and manipulating net utility visitors. It allows testers to modify HTTP/HTTPS requests and responses, allowing in-depth evaluation and testing for safety vulnerabilities. WebScarab can be customized and extended through plugins.
Free tools for dependency scanning
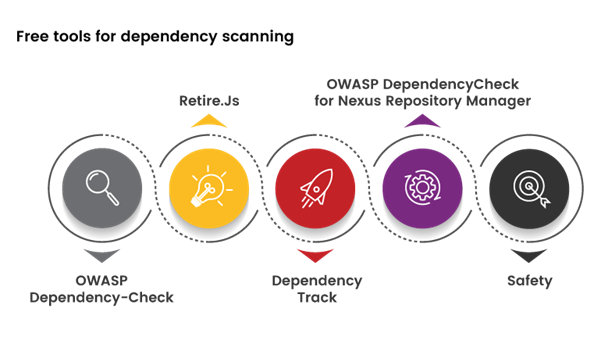
OWASP Dependency-Check:
OWASP Dependency Check is a broadly used open-source tool for scanning project dependencies and identifying recognized vulnerabilities. It supports numerous programming languages and package deal managers. Dependency-Check analyzes dependencies by evaluating them in opposition to vulnerability databases, including the National Vulnerability Database (NVD). The device provides precise reports highlighting susceptible components and variations.
Retire.Js:
Retire.Js is a specialized tool for scanning JavaScript dependencies used in web applications. It focuses on detecting vulnerable versions of JavaScript libraries that could have recognized security troubles. Retire.Js has a complete library database and can be included in construction procedures or used as a command-line device.
DependencyTrack:
DependencyTrack is an open-source platform designed for handling and monitoring software dependencies. It includes capabilities such as vulnerability scanning, dependency management, and reporting. DependencyTrack integrates with numerous statistical assets to recognize vulnerabilities in your dependencies.
OWASP DependencyCheck for Nexus Repository Manager:
This integration brings OWASP Dependency-Check functionality immediately into the Nexus Repository Manager. It allows the scanning of project dependencies for vulnerabilities during the artifact addition procedure. Leveraging the Dependency-Check tool facilitates recognizing vulnerabilities in your mission's dependencies.
Safety:
Safety is a command-line device for Python developers that scans Python dependencies for recognized protection vulnerabilities. It integrates with the Python Package Index (PyPI) and examines your mission's necessities in a vulnerability database. Safety may be easily incorporated into your development workflow to ensure the use of steady and up-to-date dependencies.
Conclusion
As a protection expert at a safety agency, you've got the unique possibility of forcing steady code practices for your organization. By fostering collaboration, undertaking effective code audits, using security team gear, and organizing comprehensive, stable coding tips, you could empower the improvement group to build sturdy and secure software programs. Remember, this is an ongoing attempt that calls for constant conversation, guidance, and schooling. Together, your safety team and improvement group can construct a strong foundation of stable coding practices, ensuring the confidentiality, integrity, and availability of software programs in an ever-evolving risk landscape.
In the realm of software development, secure code is the key that unlocks the door to a safer future.

.png)
.png)
