WordPress plugin LiteSpeed Cache has a cross-site scripting vulnerability because it does not properly sanitize user input.An attacker can take advantage of this vulnerability to run arbitrary script code in the browser of a user visiting the harmed site.It is possible for an attacker to gain access to cookie-based authentication credentials and use them to conduct other attacks. The LiteSpeed Cache plugin for Wordless version 3.6 is at risk; earlier versions may also be at risk.
What is Litespeed Cache
Server software called LiteSpeed can speed up a website.With an event-driven architecture, the LiteSpeed server is able to handle more traffic while using less resources and increasing page speed.

Allowing customers to keep their previous settings, the LiteSpeed server includes an Apache substitute with .htaccess support.It is also compatible with a number of popular hosting control panels, such as WHM, Direct Admin, and Plesk.
For dynamic content on web sites, there is an option to use the LiteSpeed Cache solution from the company LiteSpeed Technologies.
The caching and optimization capabilities are quite comprehensive.
LiteSpeed Cache is also available as a WordPress plugin on a wide range of platforms, including WordPress.com.
Website content is cached by WordPress Speed Cache (LSCWP).
It will allow web pages to load more quickly and reduce the number of requests the server has to handle.
Only the LiteSpeed server can perform server caching functions.
Open LiteSpeed, Nginx, and Apache are just a few of the web servers that can benefit from the optimization features. One option is to use a content delivery network, such as CDN (Content Delivery Network).
Categories of LiteSpeed web server
1.LiteSpeed Enterprise - Multi-website hosting solution that can be used in a shared hosting environment is LiteSpeed Enterprise. Changes to the.htaccess file are detected and the server does not need to be restarted.
2.OpenLiteSpeed - It is an open-source version of LiteSpeed Enterprise that has all the same features as the paid version.It necessitates a restart each time a new .htaccess file is loaded.The server is therefore frequently used to host a single website.
3.LightSpeed Cache - Authenticated Stored Cross-Site Scripting CVE-2020-29172
WordPress plugin LiteSpeed Cache has a cross-site scripting vulnerability because it does not properly sanitize user input. Cross-site scripting (XSS) vulnerabilities in earlier versions of the LiteSpeed Cache plugin for WordPress can be exploited using the Server IP option.Before displaying them in an error message, the plugin does not sanitize invalid IP addresses given on its Toolbox page.An attacker can take advantage of this vulnerability to run arbitrary script code in the browser of a user visiting the harmed site.It is possible for an attacker to gain access to cookie-based authentication credentials and use them to conduct other attacks.
You can use the Toolbox to submit an on-error payload such as img src onerror=alert(/XSS)>.
Vulnerable Url:- (/wp-admin/admin.php?page=litespeed-toolbox)
Step by step method to reproduce the issue
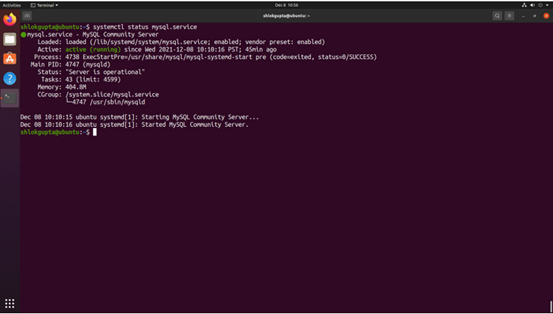
Step 1 - Set up an Apache2 server with MySQL on Ubuntu.Currently, both Apache2 and MySQL services are operational.
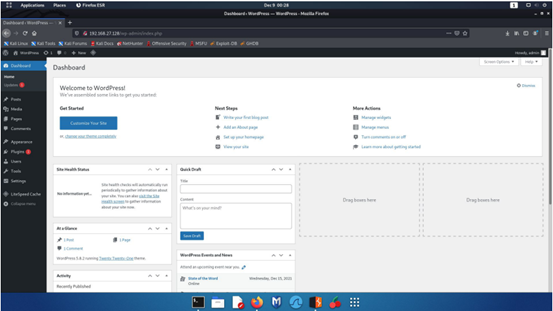
Step 2 - On the Apache server 2 install Wordpress.
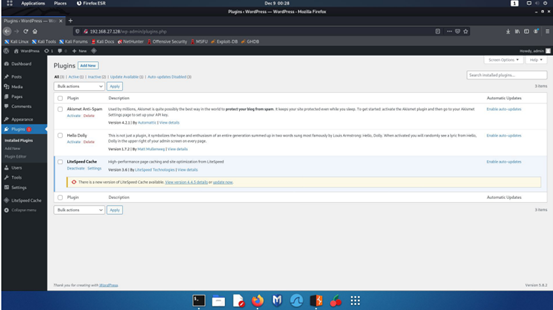
Step 3 - LightSpeed Cache v.3.6 or lower, which can be downloaded and installed using WordPress' zip-upload features, must be installed on the Apache2 server after WordPress has been installed and configured.
Step 4 - Once our plugin is installed, we can access the vulnerable module in the Debug Settings section of the Toolbox.
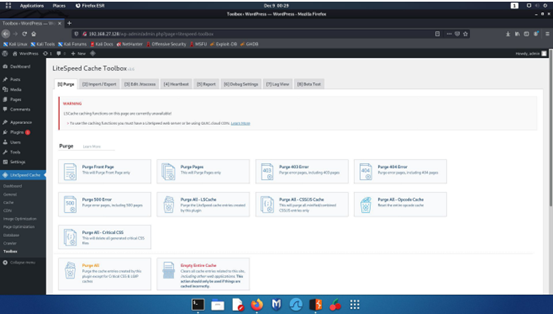
Step 5 - Once on the Debug Settings page, we can see a form with a Save Changes button that can be used to update the settings.
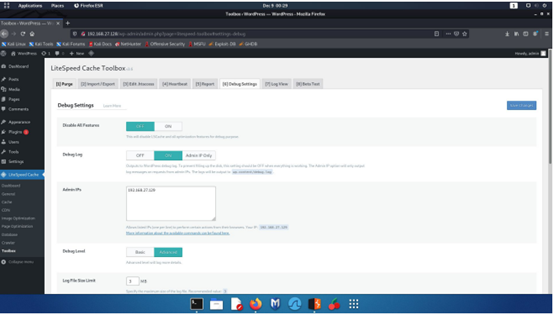
Step 6 - There is no input validation for the Admin IPs field, making it vulnerable to a stored XSS attack.Using the burp suite, we can see that the debug-ips parameter's Admin IPs field value is being sent.
In order to perform an XSS on the page, we will attempt to send a URL-encoded payload as the value for this parameter.
Payload:
URLEncode - %3Cimg%20src%20onerror%3Dalert(%2FXSS%2F)%3E
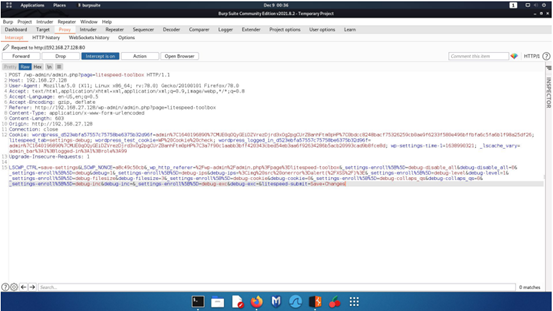
Step 7 - We have Captured the request from the proxy tool
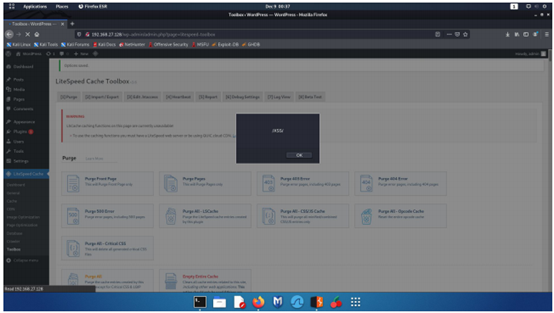
Step 8 - Here we are able to see that the payload was executed sucessfully.
Remediation
Update to plugin version 3.6.1 or latest