In this blog, we will discuss about the Surveillance, privacy, and security associated with face recognition authentication and how the way its transforming the world.
Contents:
- Surveillance, privacy, and security
- Introduction to Face recognition authentication
- The major risks associated with Facial recognition authentication
- Identity theft
- Risks related to storage of data
- Forcing facial activation
- We are in a Tomorrow land
- China
- Singapore
- Malaysia
- US Airports
- Conclusion
Surveillance, privacy, and security
Biometrics has changed the way people are being identified. Since the last decade, its growth is incredible and has transformed a lot of industries from military to telecommunication. Facial recognition is one of the biometric identification types that can be easily performed without the object’s knowledge unlike retinal scans, blood samples or fingerprints. It is a security system used to identify or verify a subject from a digital image or live footage. Most of us are used to facial biometric recognition to unlock the devices we use.
Introduction to Face recognition authentication:
Facial recognition is rapidly changing the mobile phone industry and even replacing the fingerprint entirely like in iPhone X model. Apple has already decided to remove the Touch ID by replacing Face ID. With the launch of Face ID, Apple made face recognition as a primary method to unlock phones. From authenticating the users, the recognition is also used in the payment services. Like Apple, other manufacturers are also making similar changes including Motorola, Nokia, Samsung, and other smartphone makers. It decides our life style from travelling, shopping, and much more. Facial recognition is also changing other industries. Its implementation is based on the design, hardware and the kind of software used like sensors, cameras, data analytics and related AI / Machine Learning applications.
The major risks associated with Facial recognition authentication:
Identity theft:
The identity theft on face recognition systems is severe. Risk of spoofing others identity is much higher when monetary transactions are authenticated with biometrics. In the iPhone X, it uses a TrueDepth camera system of sensors and the Galaxy S8/S9's iris scanner to handle the face recognition alone. Even though, we have seen in past that using digital photocopy, a sibling or more similar facial features like you can be enough to bypass the logins if the facial recognition is not implemented properly. The are many example to quote.
One of the ways to bypass face recognition was shown in Blackhat USA 2019 conference.
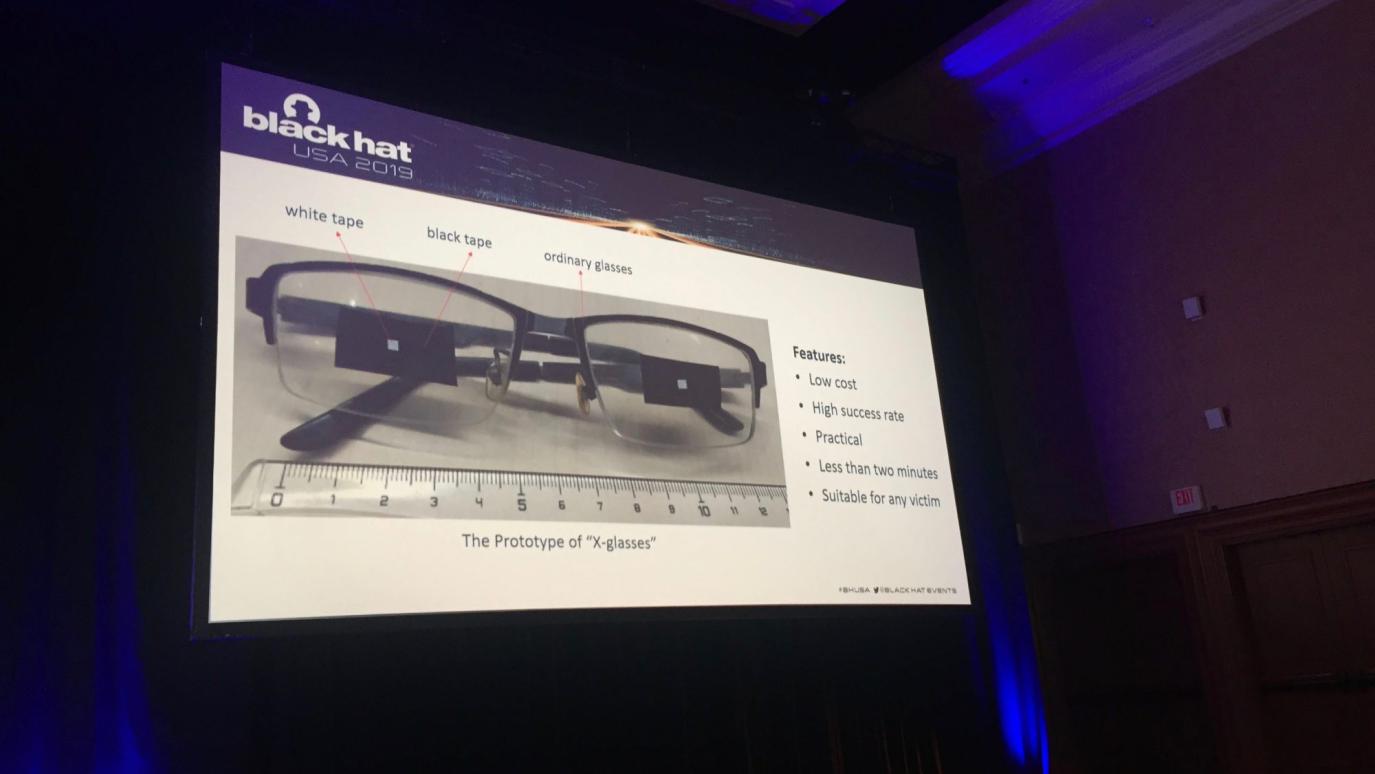
Image: blackhat presenation
Risks associated with storage of data:
The risk of storing biometric data is another critical issue with biometric identification. If your facial data is stored in a cloud server, third parties will be able to access it, even without your authorization. Increase in the number of security attacks over the years have compromised individual’s data such as personal details, financial data and even the passwords of millions of users. Systems containing a biometric data of employees, customers or citizens are a primary target of hackers and if the data is compromised, ends up in a loss that is too hard to handle because biometric data of an individual can’t be changed, if compromised.
Forcing facial activation:
Let’s say if you're captured by criminals who force you to unlock your smartphone and if your phone requires passcode or pattern to unlock, they must torture you to type or spell it out. For fingerprint locks, they need to force you to press your exact finger against the sensor. However, for face recognition, they just need to hold the phone in front of your face which can be a serious risk. But some manufacturers like Apple’s Face ID uses machine learning algorithm to analyze, whether it’s an authentic attempt to unlock or not, and it won’t work if you're not awake or conscious, and when not facing your phone.
Yes, there are other concerns like basic freedom (monitoring people), safety of your data (who all have access to it), Prevalence.
We are in a Tomorrow land:
Compared with other biometrics, facial recognition offers less protection in terms of privacy and protection level of individuals. If you care about the individual's rights and privacy, don’t ponder over it now. The changes have already begun and are happening swiftly around the world in different levels.
China:
The government is using surveillance cameras, facial recognition, AI, smart glasses and other technologies to monitor people based on their socializing manner, which leads towards both, benefit and punishment, in the society. China has started giving each citizen a social credit score. The score can rise or fall based on a wide range of behavioral analysis. If your score gets too low, you will be banned from buying a flight ticket, renting a house, getting high-speed internet, or even getting a loan.
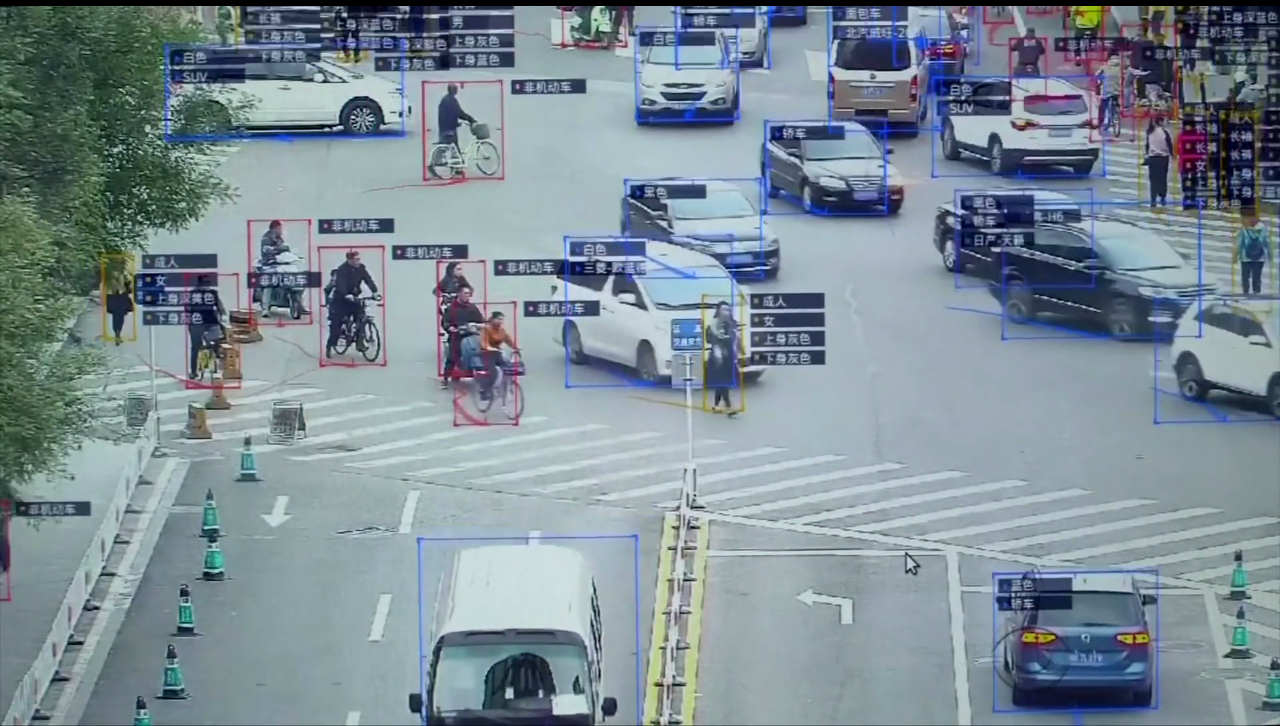
With millions of surveillance cameras in China, the government can monitor or record pedestrians and their faces will be shown in the bus stops public screens. By 2020 end, China plans to give all of its citizens a personal score, based on how they behave.
Singapore:
GovTech, the Singapore government agency that is in-charge of a “Lamppost-as-a-Platform” (LaaP) project is planning to implement surveillance cameras with facial recognition technology for over 100,000 lamp posts, to help authorities pick out and recognize faces in crowds across the city-state. The project is a part of Singapore’s “Smart Nation” plan to improve people’s lives. The government said that this would allow them to “perform crowd analytics” and even provide support in anti-terror operations.
Malaysia:
Malaysian airline AirAsia rolled out the FACES (Fast Airport Clearance Experience System) technology which uses facial recognition process to allow passengers to board their flights faster. This FACE program was unveiled at Senai International Airport in Johor Bahru, Malaysia. This is the first Malaysian airport to use facial recognition technology to board the passengers. As the system is still in its development stage in Malaysia, non-frequent and first-time foreign visitors to Senai Airport could have some doubts about having their personal information stored. Moreover, even they are suspicions about their data handling and how the data is being stored. FACES now owned by AirAsia.
US Airports
Same kind of Facial recognition systems are being used in US airports by Department of Homeland Security using technology to identify people who have stayed longer than their visas or has any criminal warrants. These types of activities have started in 2018 itself. By 2021, facial recognition will be in use at the top 20 U.S. airports for 100% of international passengers, including American citizens according to a news.
Conclusion:
Every technology has its own limitations, and facial recognition isn’t an exceptional one. Despite the risk factors associated with facial recognition, it is the future of identification and authentication practices all over the world, in which we can’t skip the changes.Surveillance, privacy, and security are the triangles which tech companies and governments are zeroing down in-order to find a reliable way to identify and monitor individuals.
You may be interested on: