Contents:
- Introduction
- Currently Available Cars In The Market
- High Level Moving Parts
- Embedded Hardware And Software
- In-Vehicle Networking
- External Interference And Protocols
- End – End Security
- Possible Loopholes
- Prevention
- How Briskinfosec Can Help You?
- Curious To Read Our Case Studies?
- Last But Not The Least
- You May Be Interested In
Introduction:
Connected cars is the next stage of automotive development fuelling to IoV (Internet of Vehicles). They’re equipped with internet access and WLAN (wireless local area network). They follow safe and legitimate standards which makes them to communicate properly, thereby driving the human safely. They use Dedicated Short-Range Communication (DSRC), with FCC granted 5.9GHz band of very low latency. They’re are internally composed of mechatronics, telemetry and AI to interact with the environment.
Currently Available Cars In The Market:
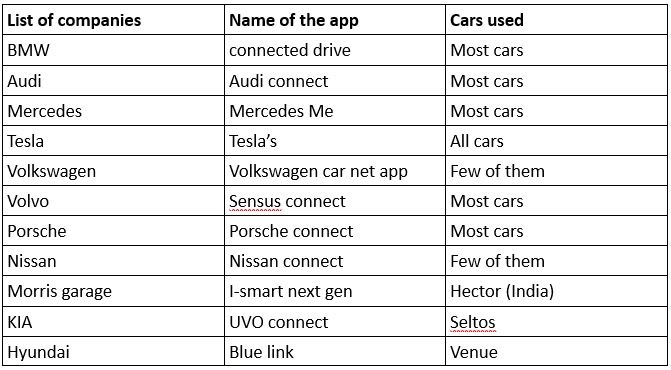
Almost all the giant and mid-sized car companies have connected cars with a mobile app interface. Below is the list of companies that have connected cars and their indigenous apps to interact with their own cars.
As per the business insider report, there’ll be about 380 million cars connected to the internet by 2021. These above car interfaces are upgraded in SOTA (Software Over The Air) update and FOTA (Firmware Over The Air) update manner.
SOTA – It refers to the downloads that pertain to the software components.
FOTA – It refers to the downloads that pertain to the firmware components.
Cars available in the middle end segment are
- Hector from Morris garage
- Venue from Hyundai
- Kicks from Nissan.
- Cars from BMW and Mercedes as well with tier 1 level too.
These devices have various features like start/stop, voice assistant, current status of the vehicle and regulating A/C’s functions which provides an earthly heaven for humans. These features intake the cyberattacks to the car via smartphones. Below shown is a Blue link app from Hyundai.

These cars come with the stock embedded sim that supports 5g and ipv6. They also have the facility of ‘Geotagging’. Geotagging refers to the adding of the latitude and longitude details by the user for identification (anti-theft) purposes i.e it immediately shuts down if a non-user drives the car.
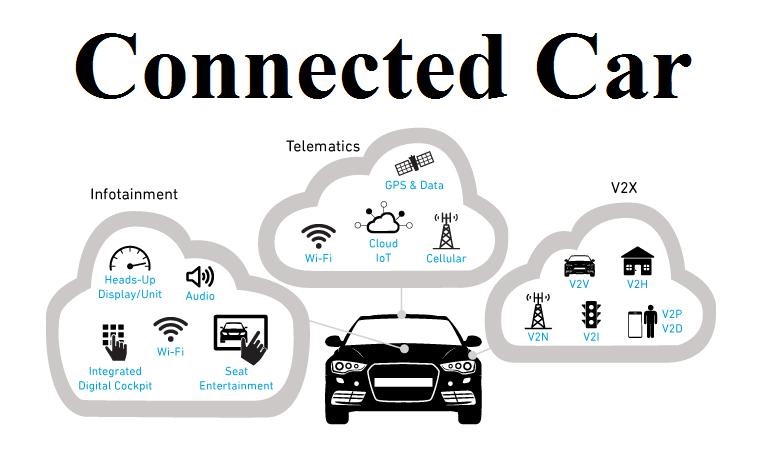
High Level Moving Parts
The below parts work behind each and every function which the user uses for interacting with the car. They are classified as
- Embedded hardware and software
- In-vehicle networking
- External interfaces
- End-to-End security
Embedded hardware and software
This section contains two major sections. They are
- High Level Networking
- Low Level Networking
To start with the classification of High-Level Networking, the hardware parts consist of four major components. They are
- Firmware
- Embedded security
- Electrical device security
- ECU testing.
Here, every part has its own unique functions where the data can be shared to the next device, once it completes its part. Even the music system of the car plays a prominent role in the embedded security feature. The prime reason is, if the music system gets compromised, then the entire security of the car is not built from the hardware design level. Hence, it can be easily compromised. A solid proof for this is the Jeep Cherokee, which was exploited through the entertainment system (music) that’s present in the car. This occurred due to the flaws that were present in the hardware design. Through this, hackers seized the control of the steering and braking systems access. Similar type of breaches occurred in general motors like Chevy Impala, BMW Connect Drive, Tesla and Nissan Leaf. Since the breaches had occurred in almost all the cars, security concerns inevitably arise. Apropos to it, the breaches could’ve also occurred due to software flaws.
In-vehicle networking (Low Level Networking):
This is about Low-Level Networking. Here, majority of the automobile manufacturers use only CAN and LIN. Few of them use ETHERNET and FLEXRAY. CAN protocol was invented by Bosch, and LIN by Lexus. These two are the major game changers for the networking protocol. Most importantly, even a single car can use all of these protocols in a synthesized manner.
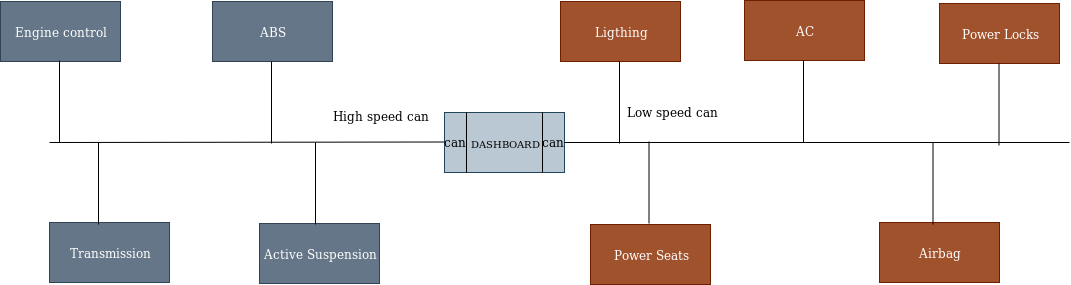
CAN (Controller Area Network)
CAN is a protocol that’s developed initially for Automotive. But today, they’re used widely, ranging from medical field to fighter jets.
CAN (Controlled Area Network) is divided into two parts namely. They are:
- High Speed CAN
- Low Speed CAN
These are prioritized based on the importance i.e., their level of importance. Systems when switched on, shed priority to high speed CAN which comprises of systems like engine, transmission, ABS (Anti-Braking Suspension) and suspension. The remaining systems like light control, power seats, AC, airbags and power locks come under low speed CAN. The reason is, they aren’t turned at the instance, when the car turns on
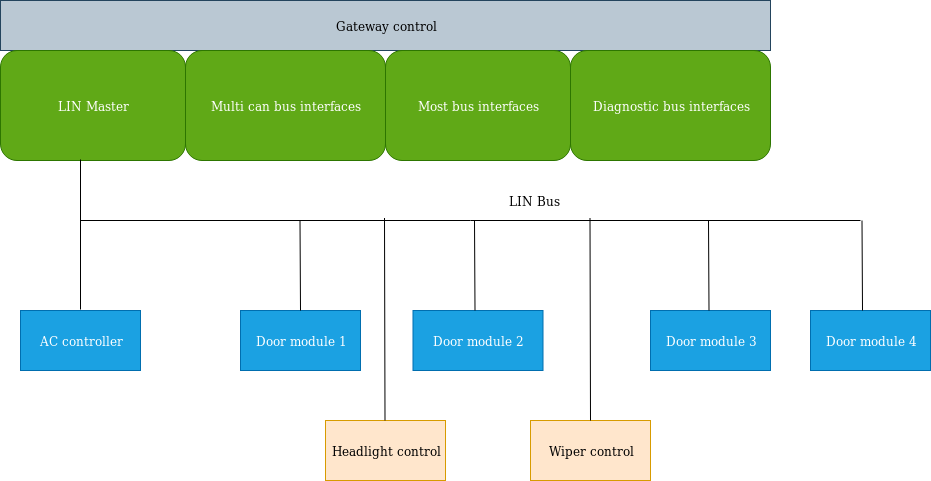
LIN (Local Interconnect Network)
LIN is almost similar to CAN protocol but differs in the testing phase. CAN protocol consists of 3 wires in which two are data lines and the other remains ground. LIN uses half duplex type with CSMA/CD and when it comes to LIN category, it consists of 2 lines. One is used for data transfer while the other acts as the ground. Since LIN is devoid of arbitration and prioritisation, the master controls all the information; each master can control up to 16 slave nodes.
Ethernet
Ethernet is a third type of communication protocol. It’s used by one of the highly reputed brands, BMW. The main use of this protocol is to transfer the data faster than CAN and LIN. Moreover, this protocol is familiar in the world of networking. It’s also worthy to remember that the traditional security vulnerabilities in CAN doesn’t affect ethernet.
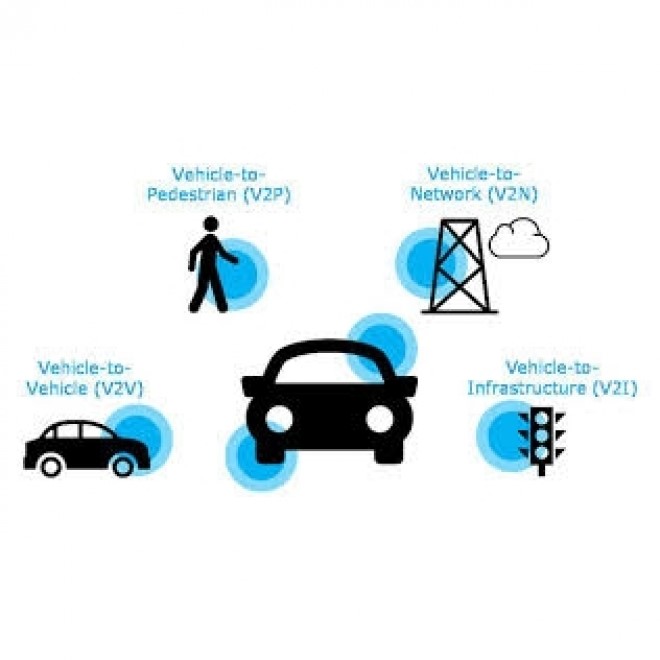
External Interfaces:
External interfaces/communication has two different parts, V2V (Vehicle-to-Vehicle) and V2X (Vehicle-to-Everything). Both of these, use proprietary RF and 802.11 as the communicating protocols.
Vehicle-Vehicle Communication
This is the communication that occurs between vehicles through which information like speed, distance and location are shared. By using these key parameters, they can drive carefully without needing human hands on steering.
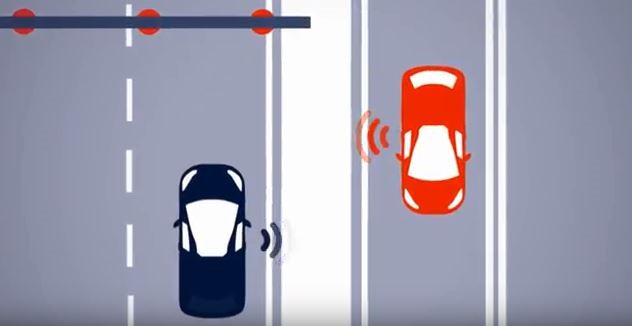
Vehicle-X Communication:
This phase involves communication with various interfaces. For example, it communicates with the pedestrians, traffic lights, other cars for entering and exiting the lane, cloud server and with the base stations. By gathering such information, the car calculates these details internally with the help of CPU (ECU). But the major drawback here is the network connectivity problem. The network speed varies from urban to rural. Henceforth, the ISP (Internet Service Providers) should take of these connectivity issues.
If the hackers have knowledge about the transmission protocols on the connected cars, then they can take over the entire control of it. Hence, security plays a major role in securing and maintaining the data of the connected cars.
End To End Security
Security concerns should start form the preliminary stage of hardware and software development. Today, we have these security guidelines which the manufactures must follow. First is the EVITA (E-Safety Vehicle Intrusion Protected Applications) which was released on 2011. This was later followed by the SAE (Society for Automotive Engineers) in 2016. Regarding security, Briskinfosec provides security standards for connected cars, as per the SAE and EVITA standards.
Possible Loopholes:
- Attacks on V2V system.
- Attacks on OTA firmware upgrades.
- Attacks on ISP.
- Attacks on sensors and system interfaces.
- Exploitation of embedded firmware and partial code re-writes.
Prevention:
- Provide End-to-End encryption.
- Hardening the encryption standards.
- Providing authentication to access all the device information.
- Radio layer hardening.
- Frequent upgradation on software and firmware.
- Providing encryption standards to physical layer.
How Briskinfosec Can Help You?
BriskInfosec has subject matter experts to test and provide security solutions for client tailored Automotive Cybersecurity needs. In the case of connected cars, our subject matter experts who can create a very detailed attack surface, map and test the device’s both internal and external security thereby providing client specific solutions. Our team tests both internal and external communications that can arise in the domain of automotive cybersecurity. They’re also specialized in the area of asymmetric attack vectors and can provide solutions for automotive needs. To know more about this, kindly reach us out.
Curious To Read Our Case Studies?
Our case studies reveal you the honest security assessment strategies used by us to fix all the classified vulnerabilities of our client’s systems/applications. Well, if you are in a notion to find and read something beneficial and intriguing, then our case studies are something that surely shouldn’t be missed.
Last But Not The Least:
Just imagine, you’re on a herculean task to accomplish something and the only way you knew to do it is by taking the route of hard work. One day, a saviour knocks your door and offers you a blessing by
providing you the route of smart work in order to achieve it without strain. Won’t you accept it? I’d assume you would!
Similarly, with regards to the significant cyberattacks that’d happened globally on every month, the impacts they’d caused to organizations and individuals, the losses faced by them and much more, and to know about all these, you have two options. First, you can take the route of hard and time-consuming work by searching in search engines and websites, day and night, in order to know them.
Well, the other one to know about them is through Briskinfosec’s Threatsploit Adversary reports, the route of smart work. It’s our report which we prepare on a monthly basis exclusively to create cybersecurity awareness to people. Even the best mitigation measures are given by us, just for you in order to stay secured against such threats. Just check it out. You’ll feel it as a blessing in disguise!

