Table of contents:
- Introduction
- What is Health Insurance Portability and Accountability Act (HIPAA)?
- Why is HIPAA necessary?
- Sections in HIPAA
- HIPAA sections that deal with Cybersecurity
- Violations and its consequences
- How Briskinfosec can help you?
- Case studies
- Last but not the least
- Suggested readings
Introduction:
Digitalization has been invading Healthcare industry for a while. Since then, Hackers have targeted the healthcare industries to seize critical data such as Personally Identifiable Information (PII). In-order to remain secure from such breaches, the US government has introduced a Law called HIPAA (Health Insurance Portability and Accountability Act). In this blog, you’ll get to know about the HIPAA policies, procedures and the violation penalties, etc., in depth.
What is Health Insurance Portability and Accountability Act (HIPAA)?
Health Insurance Portability and Accountability Act was introduced in 1996 by the 104th United State Congress. This act is primarily meant to enhance the work flow of the data that are handled by the health care service providers and related industries. This act mandates the standards in managing Personally Identifiable Information (PII), how to protect the information etc. And the scope extends further to health insurance coverage for workers and their families, setting up guidelines for group health plan, and governing company owned life insurance policies.
Why is HIPAA necessary?
Well, it’s unarguably the health care organizations who use, store, maintain, and transmit patient’s data. Hence, HIPAA is more important for health care sectors to safeguard the data privacy and data security from external threats. Breaching of such information leads to severe penalties for the data guardian. All these make HIPAA undeniably important to ensure the critical information stay secure.
Apart from ensuring privacy, reducing fraudulent activity, and improving data systems, HIPAA is believed to save providers, billions of dollars annually. Yes, by predestining and mitigating security threats, organizations would save billions and focus on their business growth.
Sections in HIPAA:
This act consists of five sections.
I: Health Care Access, Portability, and Renewability:
This section focuses on health care access, portability and renewability, as well, deals with the health insurance coverage scheme for the workers who’ve changed or lost their jobs. Also, it will limit the new health plans coverage based on the pre-existing conditions.
II: Preventing Health Care Fraud and Abuse; Administrative Simplification; Medical Liability Reform:
This section emphasizes in safeguarding from:
- Health care frauds and abuse
- Medical liability reform
- Administrative simplification that needs the establishments of national standards for electronic health care transactions
- National identifiers for providers, employers and health insurance plans.
III: Tax-related health provisions governing medical savings accounts:
This section sets up guidelines for pre-tax medical spending accounts which helps in changing the health insurance law and deductions for medical insurance.
IV: Application and enforcement of group health insurance requirements:
This section deals with the group health plans. Also, it helps in modification for health coverage.
V: Revenue offset governing tax deductions for employers:
This section governs the insurance policies owned by the company and makes provision for treating the people without United States citizenship and repelled financial institutions rule to interest allocation rules.
HIPAA section which deals with Cybersecurity:
Health and human care has enforced 5 rules for administrative simplification. Those are as follows:
Privacy rule:
The HIPAA Privacy Rule regulates the use and disclosure of Protected Health Information (PHI) by "covered entities." These entities include health care clearinghouses, health insurers, employer-sponsored health plans, and medical providers. Upon request, covered entities must disclose PHI to an individual within 30 days. Also, entities mentioned earlier must provide and disclose PHI as required by law enforcement, for the investigation of suspected child abuse.
Privacy Rule requires medical providers to give individuals PHI access when an individual requests information in writing. A provider has 30 days to provide a copy of the information to the individual. An individual may request the information in electronic form or hard-copy.
Transaction and code set rule:
HIPAA was created to improve health care systems efficiency by standardizing health care transactions. HIPAA added a new Part C titled "Administrative Simplification" that simplifies healthcare transactions by requiring health plans to standardize health care transactions.
Security rule:
Security Rule complements the Privacy Rule. While the Privacy Rule pertains to all Protected Health Information, the Security Rule is limited to Electronic Protected Health Information. It lays out 3 types of security safeguards: Administrative, Physical, and Technical.
Administrative safeguards:
These are the policies and procedures that synthesize both the Security rule and Privacy rule. This is said to be the key element of HIPAA compliance checklist. Apart from that, a proper security officer and a privacy officer should be assigned to protect ePHI as well in governing the conduct of workflow.
The administrative safeguards comprise of:
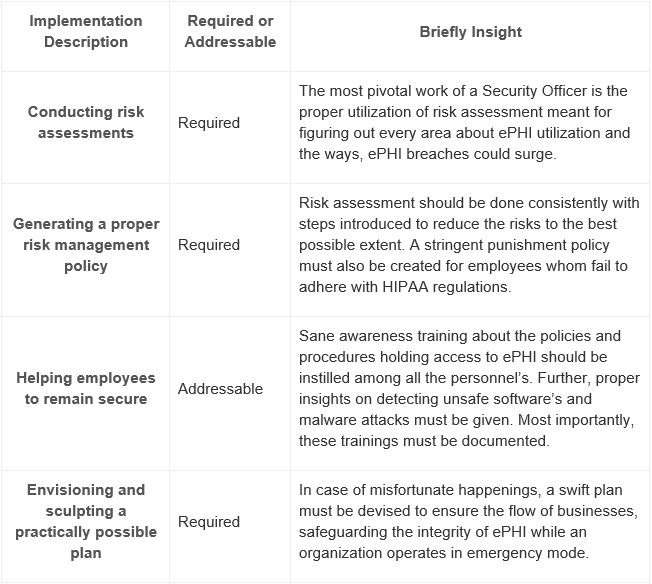

Physical Safeguards:
This focuses on providing physical access to ePHI, without bothering the location. They also specify how workstations and mobile devices could remain secured from unknown entities.
The physical safeguards include:
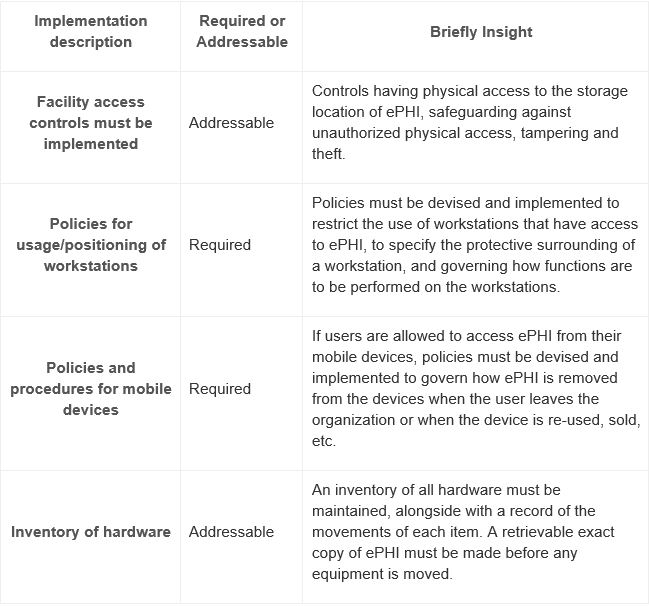
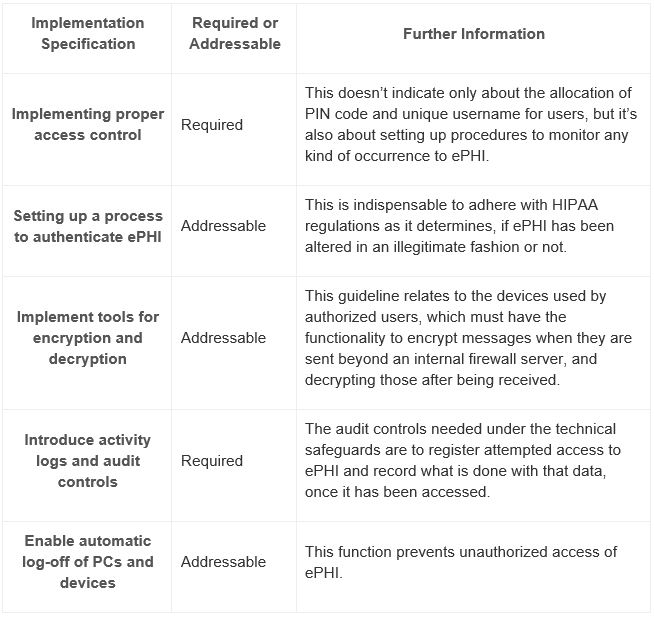
Technical Safeguards:
This is about the focus towards technology that’s given to protect ePHI, and also about providing access to the data. The only ‘must be’ factor is that, both at rest and in transit, ePHI must be encrypted to NIST standards when going beyond an organization´s internal firewalled servers. This makes the confidential data unreadable, undecipherable and unusable to the intruders, even if they breach the data.
The technical safeguards encompass:
Violations and its consequences:
U.S Department of Health and Human Services (HHS) and the Office for Civil Rights (OCR) are responsible for enforcing the HIPAA Privacy and Security Rules. This OCR deploys the privacy and security rules in several ways. Couple of them are as follows:
- Reviewing the complaints whether the policy is covered with it.
- Educating the employees on the HIPAA compliance.
These OCR monitors the information. Also, policies shouldn’t be violated, and if so, would result in civil and criminal penalty.
List of violations and its repercussions are as follows:
- Individual violating the HIPAA rules unknowingly would be charged $100 as minimum and $25,000 as maximum per violation, with an annum charges of $25,000 to $1.5 million for repeat violations.
- Violating HIPAA due to reasonable cause and not due to willful negligence would be charged $1000 as minimum and $50,000 as maximum per violations, with annual charges of $100,00 as minimum to $1.5 as maximum for repeat violations.
- Violation of HIPAA with willful neglect, but when corrected within the required time period, would be charged $10000 as minimum and $50000 as maximum.
Below are the criminal violation and its penalties:
- Covered entities and specified individuals who "knowingly" obtain or disclose individually identifiable health information would be charged up to $50,000 and face imprisonment up to 1 year.
- Any offenses committed under false pretenses would be charged up to $100,000 and face imprisonment of 5 years.
- Any individual committing crime with the intent to sell, transfer or use individually identifiable health information for commercial advantages, personal gain or malicious harm would be charged $250,000 and face an imprisonment up to 10 years.
How Briskinfosec helps you?
Briskinfosec offers comprehensive compliance services. With regards to HIPAA, Briskinfosec checks the extent to which our client’s medical data are secured. To strengthen our client’s data to the best, our security auditors successfully implement the latest policies and procedures of the HIPAA standards. Brisk also carries out security assessment in auditing the policies correctly and ensure the procedures are successfully followed by the organisation.
Case studies?
Case studies are the best examples for readers to understand the process of various security assessments, and the techniques used by the company during assessment. Check out our case studies to understand the way we perform our assessments.
Last but not the least:
Browsing internet about the companies affected by attacks, the type of loss faced, and all these to be searched one by one through night and day, indeed is time-consuming and patience-exhausting. Doesn’t this sound tedious?
Don’t worry!
Briskinfosec prepares Threatsploit Adversary Report on a monthly basis, by collecting various cyberattacks and its impacts on the respective company. Instead, of searching here and there, just a single click is more than enough. You’ll be amazed, as what you’ve bought is a billion could’ve never got.


