Contents:
- About SIEM
- How it works?
- SIEM Architecture
- Machine Learning, Deep Learning, & Artificial Intelligence in Modern SIEM Products
- Advanced SIEM capabilities: UEBA and SOAR
- Conclusion
- How Briskinfosec helps you?
- Curious to read our case studies?
- Last but not the least
- You may be interested on
About SIEM:
SIEM Integration is a comprehensive solution for capturing, retention, and delivery of security information and events, in real-time to SIEM applications.
Our high-performance, powerful SIEM solution brings the event, threat, and risk data together to provide reliable security intelligence, rapid incident response, seamless log management, and compliance reporting.
How it works?
SIEM system can be rules-based or employ a statistical correlation engine to establish relationships between event log entries. Today, most SIEM systems work by deploying multiple collection agents in a hierarchical manner to gather security-related events from end-user devices, servers, network equipment, as well as specialised security equipment’s like firewall, antivirus, or Intrusion Prevention Systems (IPS). Later, the collector forwards events to a centralized management console where the security analysts sift through the noise, connecting the dots and prioritizing security incidents.

SIEM Architecture:
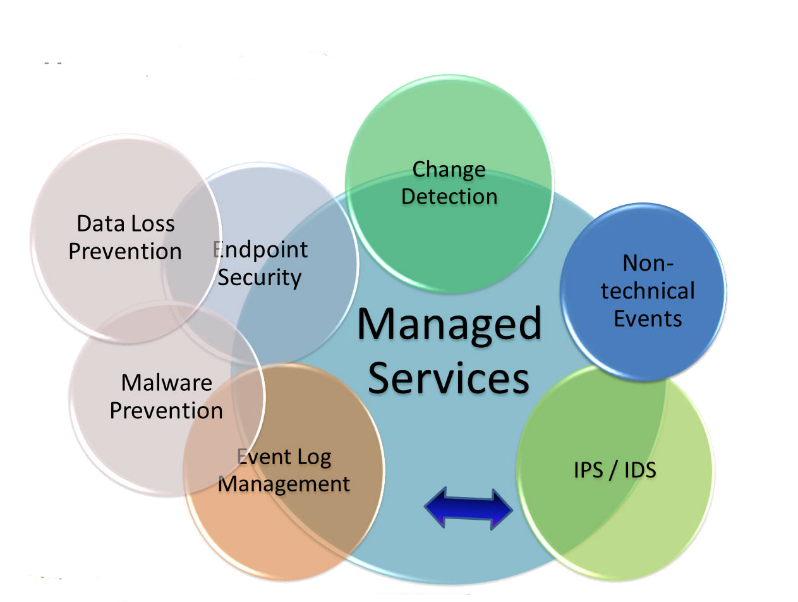
These are the most likely sources of logs that you will want a SIEM system to include:
- Intrusion Detection Systems/Intrusion Prevention Systems (IDS/IPS)
- Data Loss Prevention (DLP) systems
- Anti-virus and other endpoint security software
- Firewalls
- Unified Threat Management (UTM) systems
- VPN concentrators
- Web filters
- Honeypot or deception systems (If you have them)
- Routers and switches
- Domain controllers
- Wireless access points
- Application servers, intranet application, and databases.
Machine Learning, Deep Learning, & Artificial Intelligence in Modern SIEM Products:
In the past, most SIEM products have operated mainly on a set of rules to flag abnormalities and threats. Today, as advances in research on artificial intelligence and machine learning continue to progress, many SIEM providers are incorporating this technology directly into their products allowing for increasing accuracy in threat detection and response. As these technologies become more and more accurate and ubiquitous, expectations to see more AI based SIEM products coming to market is a certainty, and eventually, becoming the norm.
Advanced SIEM Capabilities: UEBA and SOAR:
Many SIEM systems go beyond the basics to incorporate advanced features and capabilities. Two in particular are, User and Entity Behavior Analytics (UEBA) and Security Orchestration Automation and Response (SOAR).
User and Entity Behavior Analytics (UEBA):
User and Entity Behavior Analytics (UEBA) is a type of machine learning model. For example, if a particular user regularly downloads 10 MB of files every day but suddenly downloads gigabytes of files, the system would be able to detect this anomaly and alert them immediately.
UEBA uses machine learning, algorithms, and statistical analyses to know when there is a deviation from established patterns, showing which of these anomalies could result in a potential, real threat. UEBA can also aggregate the data you have in your reports and logs, as well as analyze files, its flow, and packet information.
Security Orchestration Automation and Response (SOAR):
SOAR heralds the start of next-generation SIEM systems, with the ability not just to issue alerts when suspicious activity or threats are detected, but also to respond by carrying out actions to mitigate the threat automatically.
Security orchestration makes it possible for different security solutions from different vendors to talk to each other. By translating security data from proprietary formats into common formats that are easier to parse and store, it makes information management more powerful and efficient.
Security automation uses sets of rules called playbooks to take action without manual intervention from an analyst. By setting up rules for the most frequent kinds of alerts, for example, SOC teams can spend less time on repetitive false positive investigations.
Security response is about dealing with confirmed security issues. In more traditional environments, analysts investigate and respond to incidents entirely by hand — but bringing automation into play takes some pressure off of the analysts’ shoulders. Actions like quarantining suspicious files and disabling access to compromised accounts can be taken without human intervention. So, incidents that were once disastrous to be ignored can now be safely left for hours while security teams focus their attention to more critical issues.
Conclusion:
A SIEM goal is to alert users about the potential threats, but can be ineffective without remediation suggestions or intrusive notifications. Paired with the right log management tool, a SIEM can help you understand where and how a threat began the path it took, what it impacted, and how to fix it. A combination of log management and SIEM can also relieve burdens for IT, as technology enables real-time security analysis removing the need to learn numerous security products. The sooner the IT teams implement these solutions, the better are the organizations to get maximum protection with minimum risks.
How Briskinfosec helps you?
We avidly provide you full support in the process of SIEM integration. We have an experienced team of security enthusiasts whom possess cult knowledge in the process SIEM integration. SIEM works on rules based and its highly mandatory to do it legitimately. We, with our security veterans, assist you in properly implementing those rules-set.
Curious to read our case studies?
If you’re in a mood to find and read something innovative and significant, then our case studies is the best choice for you. They contain the innovative security strategies implemented by us during the challenge of eliminating the significant security threats that were hiding in our client’s systems. Take a look at them now!
Last but not the least:
People take hard routes to procure their wants, despite forgetting the fact that there’s an another better way to get it. With regards to acknowledgement of the most notorious cyberattacks, people look out in search engines and websites, waste too much of time, mostly end up in missing the right ones. As said, there’s always a better way to do so. Yes, it’s our Threatsploit Adversary report. It contains the collection of worldwide cyber occurred cyberbreaches, their impacts on organizations and much more. Moreover, we also provide remediation measures, helping you to remain defensive against such threats. What else? Just a single click on our report, you’ll be awe-struck!


