Starbucks does have the best coffee in the world. But, do they have the best cybersecurity defense? Johnstone discovered It was possible to execute arbitrary code by uploading a webshell using the resume feature at https://ecjobs.starbucks.com.cn and then using the resume upload capability.This vulnerability was spotted by John stone on Starbucks webapp.
Starbucks was all in praise for this bug bounty. Now, let's understand this further so that we can avoid such vulnerabilities"
Administrators and the security team must exercise caution when dealing with files uploaded by users because they could be used as a point of entry by cybercriminals.
If these files aren't properly vetted, a remote attacker could upload a malicious file to the webserver, resulting in a major breach. Malicious files can be uploaded if proper file validation procedures are not followed. Code will be executed as a result.
According to OWASP, unrestricted file upload vulnerabilities can be used in two ways. To prevent this kind of attack, web applications usually have restrictions in place, but hackers can use a variety of methods to circumvent these restrictions and gain access to a reverse shell.
Step 1: Overcoming Whitelists

Whitelisting is another common form of online security. Whitelisting is exactly the opposite of blacklisting, in which the server only accepts a limited number of extensions.
If you want to upload a profile picture, for example, the app may only accept JPG, JPEG, or PNG files. Blacklisting is better than this method of prevention, but it can still be easily evaded.
Files with double extensions can be served by some web servers, such as Apache.
The server will accept a PHP file that also has a JPG extension attached to it:
shell.php.jpg
A null byte injection can also be used to get around whitelist filters. Injecting between a prohibited and an allowed extension can lead to a bypass because anything after the null character is ignored when the file is saved:
In this case, shell.php%00.jpg
Or:
shell.php\x00.jpg
It's also possible to use Burp and modify the hex request to achieve this goal. During the request, we'll replace the G character with a null character, so name the image php-backdoor.phpG.jpg.
Make sure you've intercepted an upload request before you can look for G: Hexadecimal representation.
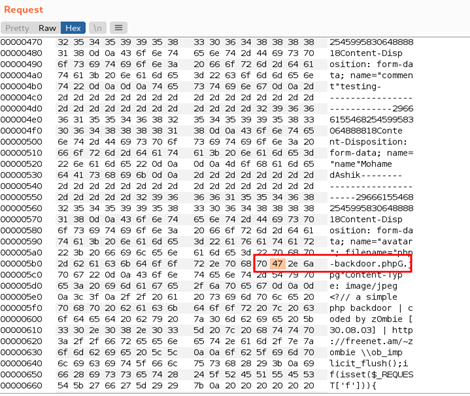
Send the request by replacing the 47 with 00:

It's possible to use this technique in situations where null byte injection fails.
To get around whitelisting, you can use file type headers to deceive the server. GIF files can typically be uploaded in the same way that images can. The upload can be tricked by including GIF89a; at the beginning of the shell:
GIF89a; _ GET['cmd']) ; ?>
Step 2: Overcoming Blacklists
There are a number of ways to get around blacklisting. The term "blacklisting" refers to a security measure that prevents particular data strings, in this case, specific extensions, from being delivered to the server. Initially, it may appear to be an ideal solution for preventing dangerous extensions, often executables, from being uploaded, but it is a simple one to circumvent.
There are additional extensions that can be used to bypass blacklist filtering in addition to the usual extensions. PHP files can have these extensions:
.pht, .phtml, .php3, .php4, .php5, .php6, .inc
JSP is another popular web shell extension; nevertheless, the following are some suitable substitutes:
.jspx, .jspf, .jsw, .jsv
Filters can be tricked into accepting a file by merely altering the case of the extension, such as this:
.pHp, .Php,.phP
Step 3: Exif Information
Exif data in an image can be used to circumvent file upload limits in the next approach. An image processing server can be instructed to run a piece of legitimate PHP code in a comment.
If it hasn't previously been installed, we can utilise exiftool to accomplish this task by using the package manager to do so:
~# apt install exiftool
After that, we can add a comment to our image with a simple command shell:
~# exiftool -Comment="" image.jpg
Now that the code has been successfully added, we can see it by running the file command on our image:
~# file image.jpg
image.jpg: JPEG image data, JFIF standard 1.01, aspect ratio, density 1x1, segment length 16, comment: "", baseline, precision 8, 1920x840, components 3
Just add a PHP extension and we'll be good to go:
~# mv image.jpg image.php.jpg
This technique can be combined with any of the approaches to bypass blacklists or whitelists.
Step 4: Other ways to bypass,
Sometimes, client-side JavaScript is the only thing that keeps files from being uploaded. If the upload still works without it, you can sometimes get around restrictions by turning JavaScript off in your browser.
If that doesn't work, it's easy to get around client-side filters by intercepting the request and changing the file extension.
Validating uploaded content can also be done by looking at the file's content type.
For example, when you upload an image, the content type of the file is usually checked to make sure it is an image and not a script or other type of malicious file.
This kind of protection is easy to get around by catching the request and changing the type of content.
In some cases, uploaded files can also be checked by how long the content is.
It depends on the situation, but a shorter payload is often all that's needed.
For example, this is how you can shorten a typical PHP command shell:
Realtime Attacks:
https://hackerone.com/reports/506646
https://hackerone.com/reports/343726
https://sidblog.medium.com/file-upload-to-rce-7c04b3b252de
https://chris-young.net/2020/04/14/file-upload-to-remote-code-execution/
[Bonus] RCE via .gif upload:
https://hackerone.com/reports/135072
Mitigation:
- Check the formats and extensions of files, Make sure you compare the file extension of the files you upload to a list of file types that are allowed. Do this on the server side, because checks on the client side can be gotten around.
- Keep your website updated
- Instead of user input, name the files randomly or use a hash.
- Use captcha to stop uploads from bots and script
- Check if the Content-Type Header is correct, A Content-Type header will be sent along with files that are uploaded from a browser. Make sure that the type given is on a list of file types that are allowed. (Keep in mind, though, that simple scripts or proxies can fake the file type, so this protection, while useful, is not enough to stop a skilled attacker.)
- Don't show the path of the file you uploaded.
To summarise, file uploads pose a serious threat to websites and apps and have serious consequences for organisations and users who don't know what's going on. Developers should do everything they can to stop uploads that aren't safe. To know further details on how we can support you, please reach us out


