Are you aware that more than 810 million web applications, which account for over 30% of all web applications globally, are powered by the WordPress content management system? This amounts to approximately 59% of the fastest-growing companies among the top 100, generating an impressive 76 million new blog posts on WordPress every month. And the most common CMS (Content Management System) in the world, common with Wikipedia and Facebook? Answer is PHP.
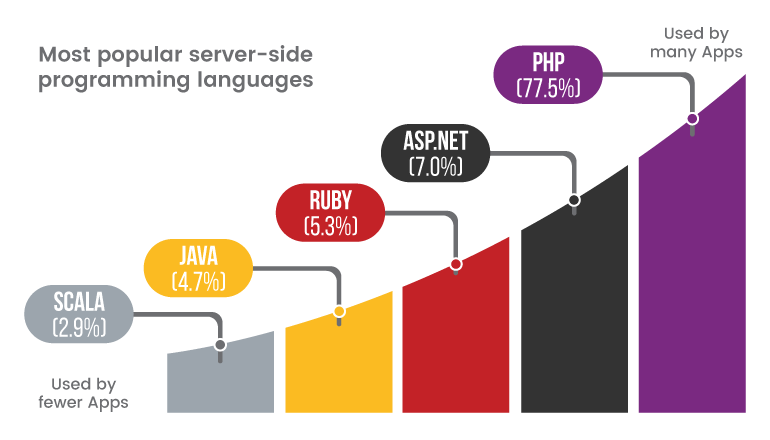
77.5% of all the web applications whose server-side programming language we know are powered by PHP behind the scenes. Without much fanfare, PHP has become the de-facto technology underlying most of the web as we know it today. However, this widespread adoption has brought forth a new concern: the issue of PHP security.
Versions of PHP
The chart presented below illustrates the distribution of PHP versions among web applications.
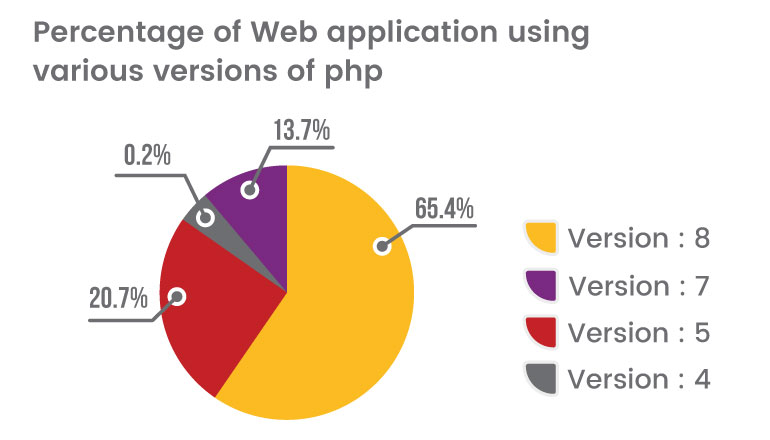
Updating PHP versions is crucial for cyber security because it allows for the installation of important security patches, reducing the risk of vulnerabilities being exploited by hackers. Outdated PHP versions can be targeted by malicious actors who actively search for software that lacks security updates, potentially leading to unauthorized access, data breaches, and the installation of malware. By keeping PHP up to date, organizations can comply with security standards, protect against malware threats, and benefit from improved performance and stability.
Why Safeguarding PHP Matters
The significance of PHP security lies in the widespread use of PHP as the underlying technology for a large portion of applications. With PHP powering a significant percentage of the web, ensuring the security of PHP-based applications becomes crucial.
Here are a few reasons why PHP security matters:
- Web App Protection
- User Data Privacy
- Reputation and Trust
- Compliance with Regulations
- Continuous Evolution
Risky functions and parameters in PHP
There are certain functions and parameters that can be considered potentially dangerous if used incorrectly or without proper validation.
- eval(): The `eval()`: Function allows execution of arbitrary PHP code. If user-supplied data is used without proper validation, it can lead to code injection vulnerabilities.
- exec() and system(): These functions allow executing shell commands on the server. If user input is directly passed to these functions without proper sanitization, it can lead to command injection vulnerabilities.
- $_GET, $_POST, and $_REQUEST: These super global arrays contain user-submitted data through GET, POST, or both methods. If this data is not properly sanitized or validated, it can lead to security vulnerabilities such as SQL injection or cross-site scripting (XSS) attacks.
- include() and require(): These functions are used for including files in PHP scripts. If the path of the included file is based on user input or can be manipulated, it can lead to directory traversal attacks or include file vulnerabilities.
- serialize () and unserialize (): These functions are used for serializing and unserializing PHP objects. If untrusted data is passed to `unserialize()`, it can lead to object injection or remote code execution vulnerabilities.
Staying up-to-date with PHP security advisories and using the latest stable versions of PHP can help protect against known vulnerabilities.
Top 3 PHP Vulnerabilities and how to fix them
SQL Injection
SQL injection vulnerabilities occur when user-provided data is improperly included in database SQL queries, creating an insecure situation. By manipulating the input, an attacker can exploit this vulnerability to escape the intended data context and manipulate the structure of the query itself.
To prevent SQL Injection:
- Validate user input for special characters in both client side and server side
- Utilizing parameterized queries, commonly referred to as prepared statements, for all database access is widely regarded as the most effective method to prevent SQL injection attacks.
XSS (Cross-Site Scripting)
Cross-site scripting vulnerabilities occur when user input is stored on the server and subsequently embedded into application responses without proper security measures. This allows an attacker to exploit the vulnerability by injecting malicious JavaScript code into the application. Consequently, any user who views the affected application content will inadvertently execute this malicious code within their browser.
To Prevent XSS:
- Application should strictly sanitize and validate user input fields in order to block HTML and JavaScript tags as inputs, to prevent injection-related attacks.
- Application should not accept special characters such as(.,<,>/,@,(,),\) as user inputs.
- Use HTML Entities to block malicious script executions.
- Use Escaping Functions or encode the malicious inputs before processing on the server.
Cross-Site Request Forgery – CSRF
Cross-site request forgery (CSRF) vulnerabilities can occur when applications solely rely on HTTP cookies to identify the user who initiated a specific request. Since browsers automatically include cookies in requests without considering their source, it becomes possible for an attacker to create a malicious application that can forge a cross-domain request to the vulnerable application.
To Prevent CSRF:
- The most effective way to protect against CSRF vulnerabilities is to include within relevant requests an additional Anti CSRF token that is not transmitted in a cookie: for example, a parameter in a hidden form field.
- The Anti-CSRF token should possess a significant amount of entropy and must be generated using a cryptographic random number generator. This ensures that it is practically impossible for an attacker to deduce or anticipate the value of any token issued to another user.
- The token should be linked to the user's session, and the application should verify that the correct token is received before executing any action associated with the request. By validating the token, the application ensures that the request originated from the intended user and helps prevent unauthorized actions.
Conclusion
Verify and Validate!
The main lesson learned from most web security issues is the importance of utilizing appropriate authentication and session management functions. It is crucial to thoroughly verify and validate all input received by your web application on the server side, as the client-side browser can be easily manipulated beyond your control.
In numerous cases, web applications rely on multiple open-source libraries to enhance their functionality. However, these libraries can contain their own security flaws and vulnerabilities. Hence, it is imperative to employ a vulnerability scanning service to ensure the security of not only your code but also the dependencies used by your web application. This includes regularly patching the dependencies with the latest updates to ensure their safety in a production environment.


.png)
.png)
