Imagine John surfing on the internet. He likes a product from a website. He orders it & now it is time to pay for it. He puts in the banking credentials. Everything went well. Except for the fact that the money did not hit the website account but a hacker's account.
We all can be in place of John at any time & experience the same issue.
How can we protect ourselves & understand what is the cause?
To understand this, we need to know what a session is and what kinds of sessions there are.
What is a session?
A session starts when an app opens up, and it keeps track of how long and how often an app is in use.
Let’s move to the types as it is not one attack but a different type:
Types of session-based attack
- Session Hijacking attack
- Session Prediction attack
- Session Fixation attacks
- Session Sidejacking attacks
- Session Replay attacks
- Session Spoofing attacks
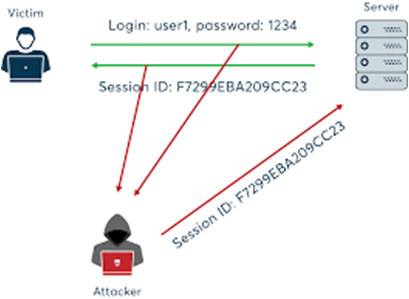
Session Hijacking Attack
Session hijacking is a way for hackers to get into a target's computer or online account. A "session hijacking attack" is when a hacker takes over a user's browser session to get personal information and passwords. This is a "session hijacking attack."
A user's session can change in many ways by a session hijacker.
A common way is for the hacker to use a packet sniffer to see what information is being sent and received between the user and the server. Then, they will use this information to get private information or log into the account.
Session Prediction Attack
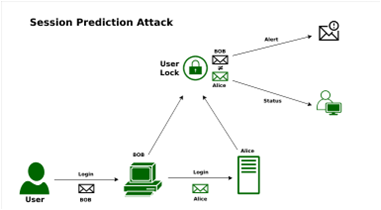
Session prediction attacks try to guess the values of session IDs. This lets an attacker get around an application's authentication system. If an attacker knows what is the session ID, they may be able to guess a valid session ID and get into the application.
To figure out who the authenticated user is, the attacker must get some valid session ID values. Then, you need to know how the session ID is made, what information goes into it, and how the program uses encryption or hashing to keep the session ID safe.
Some wrong ways of doing things employ the use a username or session ID. This is in turn made up of things like timestamps and client IP addresses.
Session Fixation Attack
Session prediction attacks try to guess the values of session IDs. This lets an attacker get around an application's authentication system. If an attacker knows what is the session ID, they may be able to guess a valid session ID and get into the application.
To figure out who the authenticated user is, the attacker must get some valid session ID values. Then, you need to know how the session ID is made, what information goes into it, and how the program uses encryption or hashing to keep the session ID safe.
Some wrong ways of doing things employ the use a username or session ID. This is in turn made up of things like timestamps and client IP addresses.
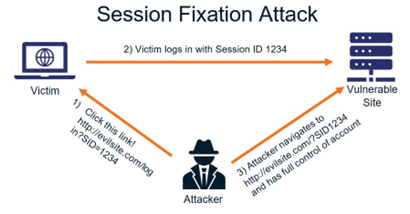
Session Fixation Attacks
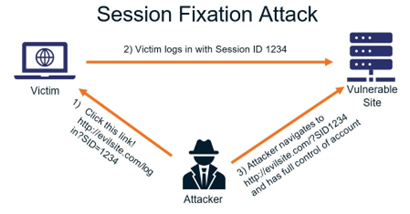
Session Fixation is a type of user attack on a web application in which a thief tricks a victim into using a Session ID that the thief already knows.
When a victim makes a request to a vulnerable application using a known Session ID, an attacker can use this weakness to make their own requests using the same Session ID, as if they own the Session.
This attack is different from Session Hijacking in that the attacker already has the Session ID and forces it on the victim, instead of using another flaw to find the token.
Session Side jacking Attack
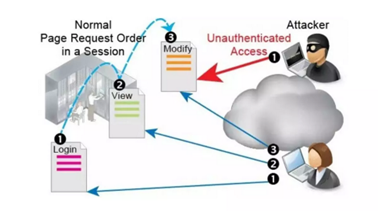
Session sidejacking takes advantage of a connection between the victim and the target system that is not encrypted.
The attacker sniffs network traffic for session tokens in unencrypted transmission.
After getting a session token. The attacker can impersonate the victim by utilizing the stolen token with the targeted application.
This is a type of session sidejacking attack in which a valid session token is used to get unauthorized access to a target system or information.
Session Replay Attack
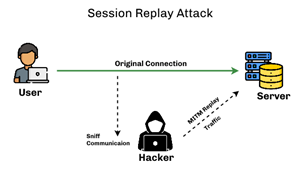
A Session Replay Attack occurs when an attacker takes a valid session ID from a user and uses it to impersonate an authorized user to undertake fraudulent transactions/activities.
Session Replay Attacks can occur when, session IDs do not have a defined session expiration time or when session data is in an unencrypted format.
Session Replay Attacks are also possible in web applications that enable the reuse of old session IDs or session credentials for permission.
Session Spoofing Attack
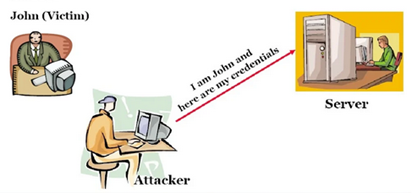
A spoofing attack differs from a hijacking attack in that the attacker does not actively take another user offline to carry out the assault.
Instead, he impersonates another user or machine to get access.The person the attacker is pretending to be could be at home or on vacation while he does this, so the real user is not affected by the attack. Because of this, the attacker is not trying to take over a user's session.
Defending Against Session Based Attack
- Modern frameworks implement safe, unguessable session IDs. If you are using a recent version of your web toolkit, check to see how the session IDs are generated.
- Make HTTPS mandatory on all of your sites, not just the login page.
- Use HSTS, for example, and set the Secure flag for session cookies.
- After the user logs in, modify the session ID.
- Log out inactive users and invalidate session IDs after a certain period of time\
Conclusion
The importance of session management process cannot be understated. Session management is a critical business asset that must be protected from potential threats and must be assessed to ensure that it is functioning properly.
The best way to protect your business's session management against potential threats is to regularly assess its security posture and implement necessary remediation.
The goal of the blog is to make sure that the session management is well understood & is as secure as possible.
We at Briskinfosec strive to simplify, educate & create awareness about cybersecurity. Write to us or contact us for any doubts & services.