Out of the entire population on the planet earth, at least most of them have a Facebook account. What if I tell you that these data's can be hacked not from your computer but from the cloud.
Facebook reported a breach affecting hundreds of millions of users which were recorded in the year 2021, where the data was publicly exposed on Amazon's cloud computing service. Although Facebook has confirmed that the issue was identified and resolved immediately.
Two third-party Facebook app development companies sparked the incident by posting the records in plain sight. The exposed database contained sensitive information that social engineers could exploit in targeted attacks or hacking attempts.
Even, last week, Mark Zuckerberg’s, followers went and it was unofficially reported that the application was hacked. Many users across the globe reported the loosing users’ phenomena. This is the case of hacking.
In order to resolve this issue, Facebook contacted Amazon,and Amazon shut down the servers that were open to the public.
To continue this case and many like these, the point to be noted is, if Facebook data is hackable from AWS then your data is too hackable. Especially,for SAAS platform.
What is Software-as-a-Service (SaaS)?
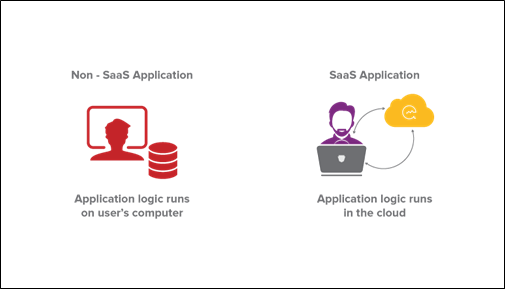
Software-as-a-Service (SaaS) is a method of delivering software to users via the cloud. SaaS users subscribe to an application rather than purchasing and installing it. A SaaS application can be accessed and used from any Internet-connected device. The application is hosted on cloud servers that may be located far away from the user.
A SaaS application can be accessed via a browser or app. SaaS applications include online email applications that user’s access through a browser, such as Gmail and Office 365.
What Is SaaS Security?
The vast majority of organizations use cloud environments, and many have multi-cloud implementations, with the average enterprise leveraging services from five cloud providers. Although cloud computing is understandably popular, it also introduces a number of security risks, including compliance issues, contract violations, insecure APIs, and misconfigurations.
Software-as-a-Service (SaaS) environments are particularly appealing to cyber criminals because they store sensitive data such as payment card details and personally identifiable information.As a result, organisations must prioritise SaaS security.
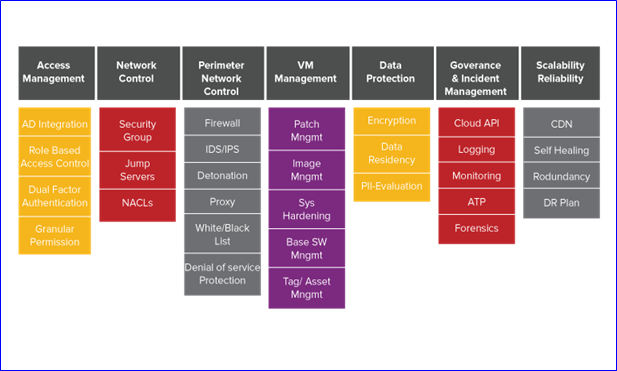
Saas Architecture
- Single tenant architecture
- Multi tenant architecture
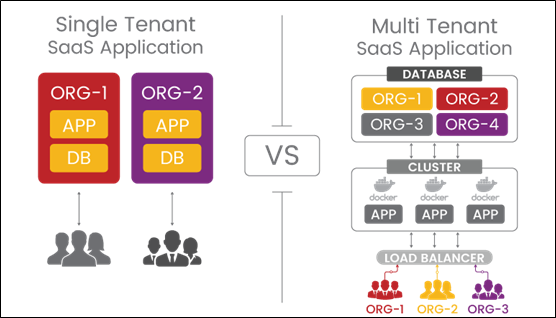
Single tenant architecture
A single-tenant architecture (also called a "siloed model") is a single architecture for each organization, where each application has its own hardware, software, and infrastructure.
Say you have ten organization. In this case, you would need to make ten separate environments, and your SaaS application or company would work as a single tenant architecture. It also means more costs, more maintenance, and a harder time keeping all environments up to date.
Multi tenant architecture
Multi tenant architecture is an ecosystem or model in which a single environment with a scalable, available, and resilient architecture can serve multiple tenants. The underlying infrastructure is fully shared, each part is logically separate, and all services are run from one place. The multi-tenant architecture changes depending on the organization or subdomain (organization.saas.com) that is logged into the SaaS application. This is completely invisible to the end user.
Single tenant Vs Multi-tenant architecture
DevSecOps in SaaS Platform
DevSecOps, which stands for development, security, and operations, automates the integration of security at every stage of the software development lifecycle, from the initial design to integration, testing, deployment, and software delivery.
DevSecOps is an approach to software development and operations that incorporates security practises such as Agile and DevOps without disrupting the development or deployment workflow. Problems with security are dealt with as they arise, when they can be dealt with in the most efficient, economical manner (and before they are put into production).DevSecOps also eliminates the need for a separate security department by making it the responsibility of the entire development, security, and IT operations team to ensure the safety of all applications and infrastructure.In other words, it helps the DevSecOps mantra of "software, safer, sooner" come true by speeding up the delivery of secure software through automation.
DevSecOps Architecture
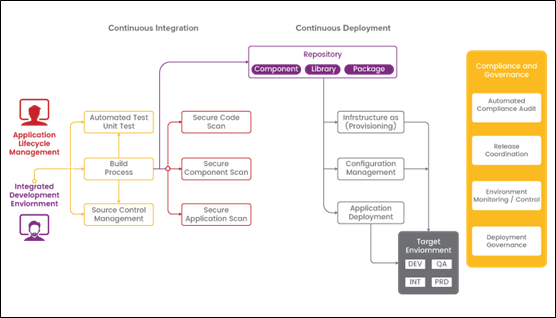
SaaS security Best Practices
1.Shared Responsibility
Two major factors influence the level of security in open systems, such as SaaS products: technology and usage. The first is the responsibility of the provider; he must create a product that is safe to use under specific conditions. On the other hand, it is the users' responsibility to follow these rules and use the application safely. It’s comparable to driving a car. The manufacturer creates a vehicle that meets all of the technical requirements, such as working brakes, airbags, and seat belts. Everything else is in the hands of the driver. Even the best technological protection may not be enough if he exceeds the speed limit, violates traffic laws, or gets behind the wheel while intoxicated. Similarly, the key to SaaS security is shared responsibility between the user and the provider.
2. Access and role management
Employees in many organizations use the application with a single administrator account, share login credentials, or never log out of the system. Outsiders, such as freelancers or subcontractors, are frequently granted access to sensitive information-containing systems. As a result, the organization loses control over what happens to its data because anyone who has access to it could be a target for a cyber attack.
What can be done to avoid this?
It's a good idea to use roles and custom permissions to ensure that each employee only sees the features and information that they need. Ensure that your credentials are secure and protected, such as with multi-factor authentication, which we will cover later. In order to detect security vulnerabilities, it is also critical to be able to trace activity from the admin account.
3. Update in case of employees turnover
When an employee leaves a company, there is always a lot of paperwork and technical issues to deal with - you must cancel benefits such as sports cards or medical packages, collect equipment, change project statuses, and prepare the person who will take over new responsibilities for on boarding. It's easy to forget to revoke a departing employee's access to tools and applications in these situations. Drives and clouds, email addresses, Slack, social media accounts, and customer information are all potential leakage points, particularly if the employee who left the company still has access to login credentials or was logged in on personal devices.
4.Multi-factor authentication
Single-factor authentication is a method of gaining access to an application with only an email address and a password. Although this is still the most common method of logging into many SaaS applications, multi-factor authentication is a far more secure option. In this case, in addition to the correct password, you will need to enter another factor to log in.This could be a numerical code or a one-of-a-kind key.To make a larger transfer, for example, you must first log in to the banking application using your login and password, and then confirm the transfer by entering the code that the bank sent to you via SMS.
5. Encryption
Encryption is a method of data security that makes data unreadable without the use of a key. Encryption converts the original text, known as plain text, into an unreadable record, known as cipher-text. In this case, an authorized user must use a key, such as a string of numbers, to decrypt the encrypted text and read the original content. This is a straightforward but highly effective method of safeguarding data against cyber attacks.
6. Password security
Application passwords are frequently the weakest link in SaaS product security.To begin with, they are frequently used by multiple people on multiple devices. Second, passwords such as "Admin123" or "Company Name 2022" are frequently easy to remember and thus simple to crack.Third, businesses rarely change their passwords, often sticking with the same login credentials for years.Fourth, passwords are not properly stored and secured.Companies use a variety of applications, and expecting employees to remember 20 complex passwords for each application is unrealistic.As a result, businesses keep all of their passwords in a secure location.That "somewhere" is usually a file on a drive where all the credentials are served up to a potential cyber criminal on a silver platter.
To function properly, passwords must be extra secure.A strong password is required; ideally, it should be a random sequence of letters, numbers, and characters.Passwords should not be reused across applications and should be changed on a regular basis.Passwords that no one remembers are insecure (unless created by the employees themselves), so they must be stored in some way.In this case, a simple mention of encryption will protect the file with your credentials.
7.Data storage and processing
Data security and SaaS security are synonymous.According to 65.75 percent of cybersecurity IT professionals, the most common potential sources of data leakage are cloud storage, file sharing, and email.The most important thing to do to improve SaaS security is to ensure that applications only collect data that the user knowingly consents to.Another consideration is WHERE the data will be gathered and WHO will have access to it.This is particularly true when SaaS products are combined with other applications.Finally, make certain that the SaaS product provider has a clearly defined data security policy as well as a track record of privacy.
8. Procedures and contingency plan
Data security, like any other habit, is a practise.And proper procedures aid in habit formation.Prepare a data security scenario, such as a checklist, and methodically check whether all points have been met each time.Understanding that something can always go wrong is also essential for data security.If this is the case, it's a good idea to have a contingency plan in place ahead of time - procedures that can be put in place to reduce losses and eliminate the threat in the event of a cyber attack.
9. Awareness
Security training should be provided to all employees.It will assist them in avoiding common errors, and teaching them how to implement basic security measures will save your company from many future problems.Employee education will also assist them in recognising and eliminating modern and more sophisticated hacking methods such as social engineering techniques.
In a variety of critical financial and regulatory areas, SaaS technology holds the promise of lower costs and more agile performance.These applications typically involve the management of sensitive customer information, regulatory compliance, and other aspects of the business. SaaS can be far more secure than on-premise applications with the right technology and best practices, and the organization has many options for retaining control over the security infrastructure, such as encryption of customer data.