Contents:
- Introduction
- About Docker
- Inception of BNPT-Docker
- Working with tools using Docker
- Benefits and scope of BNPT-Docker
- Conclusion
- Curious to read our case studies?
- Last but not the least
- You may be interested on
Introduction:
To scan a target, both cybersecurity veterans and novice pen-testers primarily use the open source scanning tools. In order to obtain the best possible results, one has to use every available tool one-by-one which is ‘time-consuming and patience-exhausting’.
Sounds tedious right?
Don’t worry. We have built a simple and effective solution for you - a Docker image named as ‘BNPT Docker’.
About Docker:
Docker is a container management system created for managing the Linux containers. With this platform, we can create, test, and deploy containers in virtual environment. Docker works like almost virtualization but actually it isn’t. Virtualization is achieved with a software commonly called as ‘hypervisor’. This allows the user to install an operating system on the base machine through hypervisor. Also, it would occupy resources of the base machine even if not required. But, Docker would use only the required amount of resources and also won’t create an operating system. Instead, it will share the kernel of the local machine. So with this kind of platform, developers can easily perform their tasks.
Inception of BNPT-Docker:
Once you are familiar with Docker concepts, you can create a new Docker image and integrate tools into it. Creating Docker image is simple and easy.
In BNPT-Docker, best open source tools for performing network penetration testing are chosen and integrated into the Docker environment. A file named “Dockerfile”, is helpful while integrating the tools into the BNPT-Docker, because this file commands the Docker daemon to create the Docker image based on our requirements. This is one of the way to integrate the tools into the Docker.
Tools that are integrated into the BNPT-Docker are below:
- Nmap
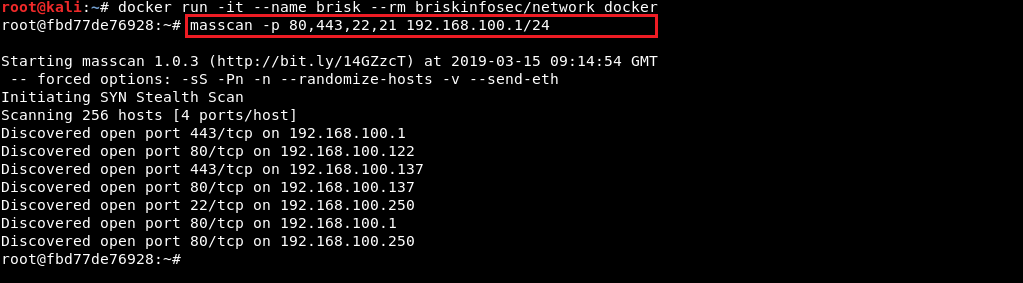
- Masscan
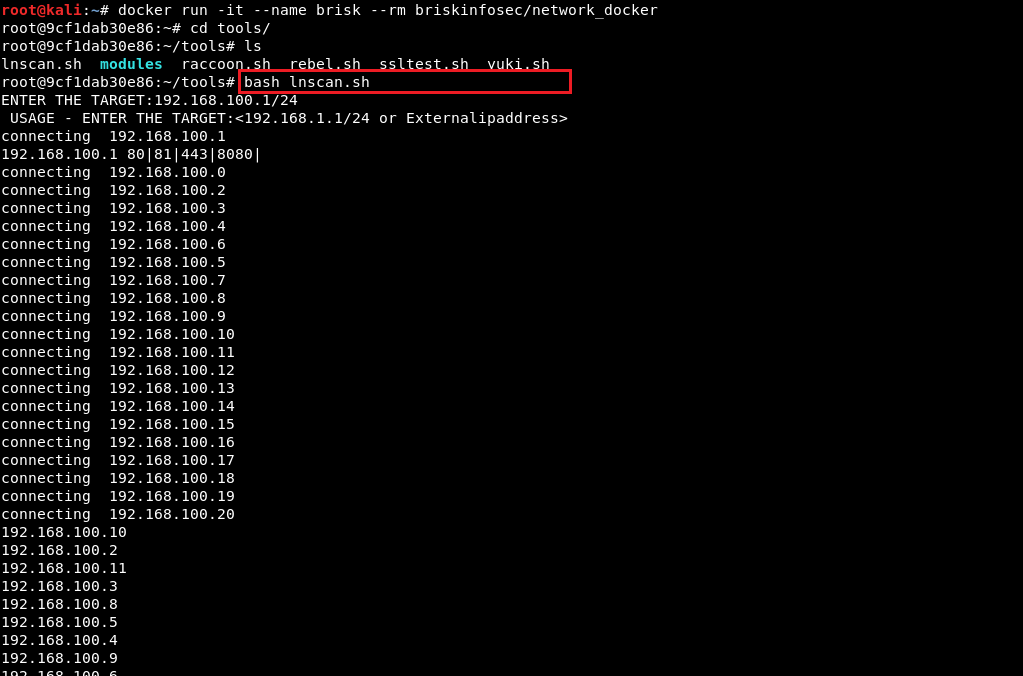
- LNScan
- Hping3
- SSLtest
- Rebel-Framework
- Raccoon-Scanner
- Yuki-Chan
Working with tools using Docker:
Before getting started, check whether the Docker is properly installed on the machine. If not, then install using the following method:
$ curl -sSL https://get.Docker.com/ | sh
$ sudo systemctl start Docker
Alternate method is:
$ sudo apt-get update
$ sudo apt-get install Docker-ce Docker-ce-cli containerd.io
After the installation, start the service. Then, the Docker image should be pulled to your local machine from the Docker hub. The command to do this:
$ service Docker start
$ Docker pull briskinfosec/bnpt_Docker
Then we have to initiate the container. When initiating, Docker daemon will communicate with Docker image and create a container, and yield us a shell of the container to our terminal.
The command to achieve this is:
$Docker run -it --name brisk --rm briskinfosec/bnpt_Docker
- -run will start the container.
- -i will start the container in interactive mode.
- -t will give us a tty (teletype) shell of the container.
- --name will allow us to give a name to the container instead of generating a random name (brisk is the name given to the container).
- --rm will remove the container, once it is exited.
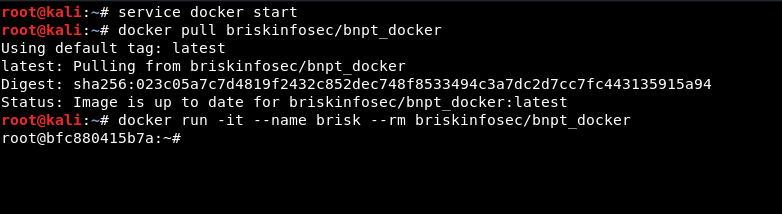
Now, we will look at the tools we have integrated into it.
Once we have the access to the container, it is really easy to handle the tools.
- Nmap is a network scanning tool, which is used to discover hosts and services by sending crafted packets and analyzing the response.
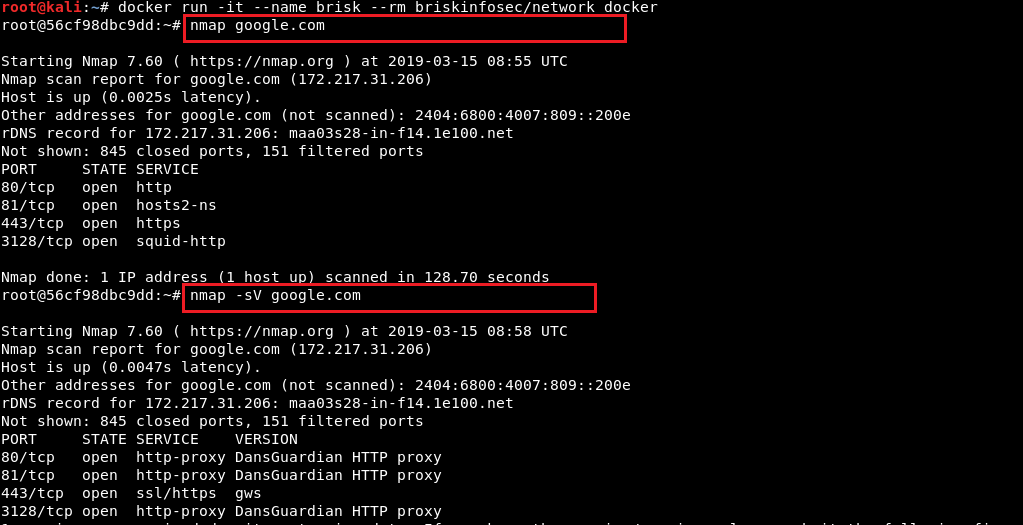
- Masscan is the fastest internet port scanner. It can scan the entire internet under 6 minutes, transmitting 10 million packets per second. It produces results similar to Nmap, the most famous port scanner.
- LNScan (Local Network Scanner), is an internal network scanner which is only used for enterprise security self-tests.
- Hping is a command-line oriented TCP/IP packet assembler/analyzer. It supports TCP, UDP, ICMP, and RAW-IP protocols. It is mainly used for manual packet crafting.
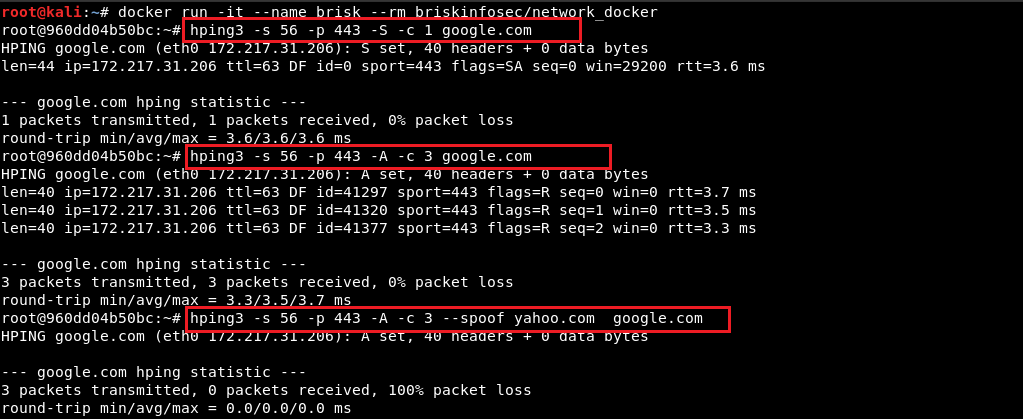
- SSLtest will check for SSL related vulnerability on the target. This action is performed using SSL Labs API.
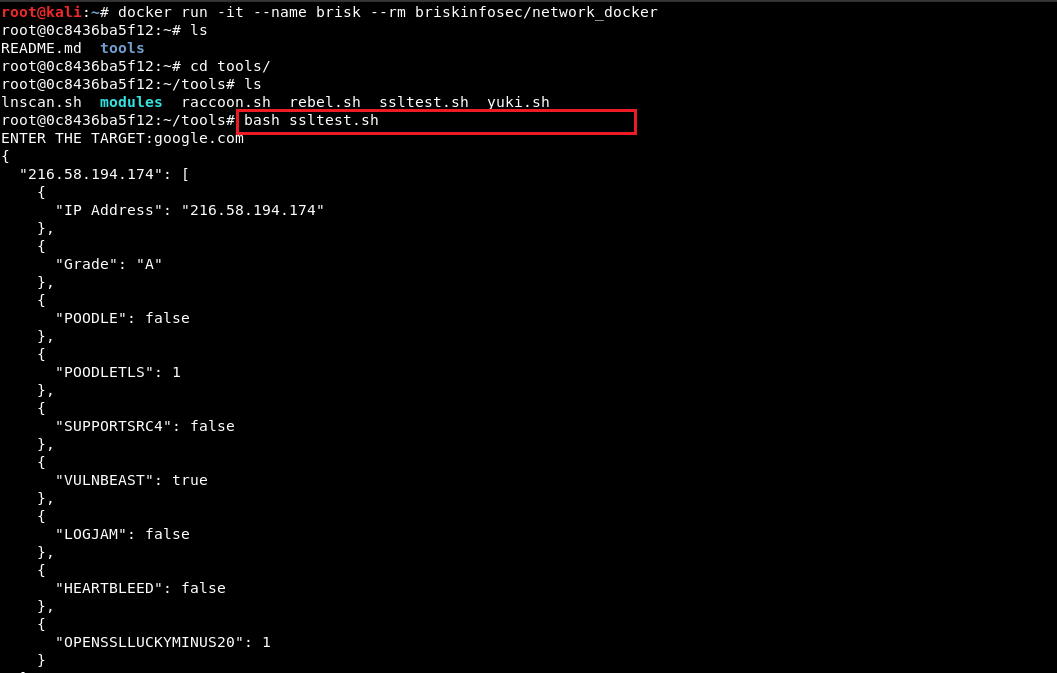
- Rebel Framework has a list of modules which could be used during penetration testing.
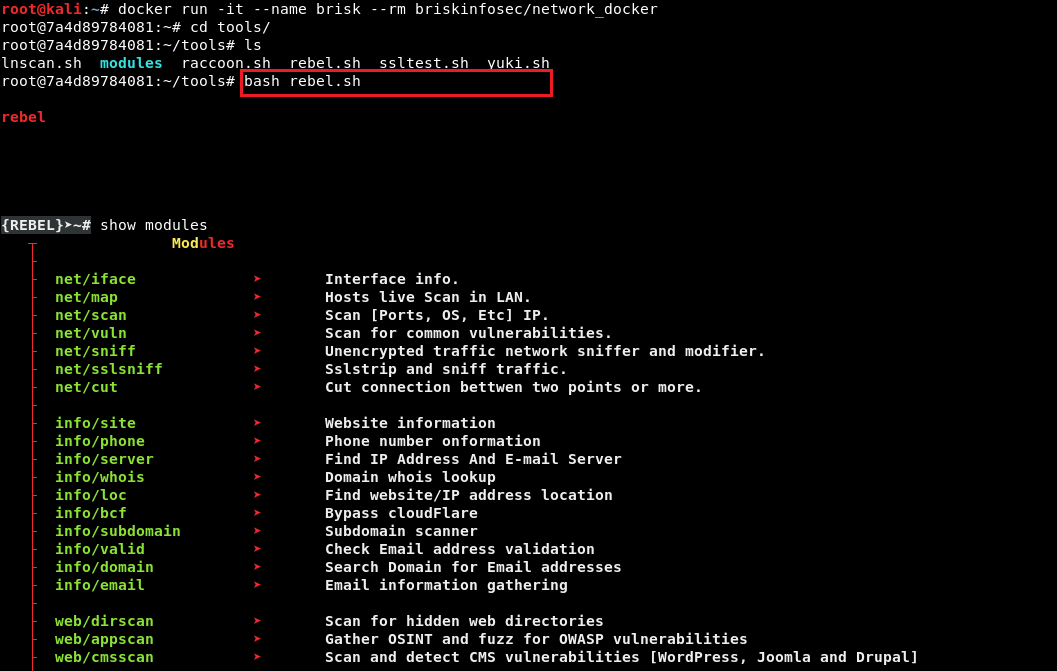
- Raccoon-Scanner is a reconnaissance and vulnerability scanner. It performs automated scans with the pre-built tools, created using python. This will perform the vulnerability scan automatically and categorize the results.
- Yuki-Chan is also an automated penetration testing tool, which can be used to perform security testing on the target.
Benefits and future of BNPT-Docker:
With this BNPT-Docker, it is easy to run the tools required for penetration testing by skipping the installation process. Also, it will not disturb the host machines dependencies because everything already exists in it. It is faster when compared to the virtual machine in all stages of starting, deploying, and running. It only uses the required amount of memory to run with this ability. Further, it won’t be a huge process for the host machine to handle.
Conclusion:
This BNPT-Docker is just a beginning of something great. Our next version of this Docker would have additional tools, with a customized script to automate all those tools, which reduces the work of users whom are using BNPT-Docker.
You can find the BNPT-Docker here (https://github.com/briskinfosec/BNPT_Docker).
Curious to read our case studies?
Our case studies showcase the unique strategy used in performing successful security assessments. Read them out. You’ll know that our top-notch security providence is one of the prime reasons, we are being cited as one among the “Top 20 most promising cybersecurity organizations”.
Last but not the least:
Docker as a single image, contains various tools that can be utilized as per our wants. Instead of using each and every tool one by one, Docker proves it’s supremacy, as it’s a ‘one click and does all’ stuff.
Similarly, we prepare our Threatsploit Adversary report. It’s a report that contains the global collection of cyberattacks, its impacts, the organizations affected by them, and much more. Instead, of searching here and there for cyberattacks and wasting time, just a single click on our Threatsploit report is enough. You’ll see all your needs, in front of you.


