Table Of Contents
- What Is Banner Grabbing?
- Why Banner Grabbing?
- Why Banner Grabbing Is An Serious Issue?
- Types of Banner Grabbing
- Tools
- Banner Grabbing through Browser Extensions
- Steps to Prevent Banner Grabbing In Popular Servers
- How to Prevent Banner Grabbing ?
- Conclusion
What Is Banner Grabbing?
Banner grabbing or active reconnaissance is a type of attack during which the attackers send requests to the system they are attempting to attack in order to gather more information about it. If the system is not securely configured, it may leak information about itself, such as the server version, PHP/ASP.NET version, OpenSSH version, etc.
Why Banner Grabbing?
Banner Grabbing allows an attacker to discover network hosts and running services with their versions on the open ports and moreover operating systems so that he can exploit the remote host server.
Banner Disclosure is the most common vulnerability with a “CWE-200 i.e. Exposure of Sensitive Information to an Unauthorized Actor” and a “CVSS Score of 5.0 with the Risk factor as Medium.”
Why Banner Grabbing Is An Serious Issue
Hackers grab banners all the time. Although IP can be logged, hackers usually hide their real IP before grabbing it. If they are successful in grabbing a few banners they can then use this information to find applications that are weak or have a security flaw. Attackers then focus on exploits that are targeted to the services that you are running. The reare hundreds of services that can be queried for banners and more than often, a few have flaws or are simply old versions.
Types of Banner Grabbing
Active Banner grabbing –In this, the attacker craft or modify his/her own packets and send them to the remote host server and analyses the response data in order to get the operating system information and the services running with their versions.
Passive Banner grabbing –Here the attacker collects data about our target using publicly available information i.e. by analyzing the server either with the help of “Error Messages” or by “Sniffing up the Network Traffic”.
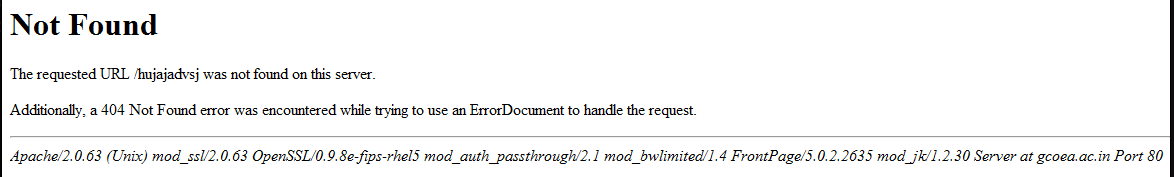
Tools
There are various kinds of tools available to perform the technique of Banner Grabbing. In this section of the article, Banner Grabbing tools are described, and below are some of the most popular and top tools available for using the Banner Grabbing technique.
Telnet: It is the most popular and best tool for using the technique of banner Grabbing. Telnet web tool is the cross-platform that is available which helps to interact with remote servers for banner grabbing. Telnet allows querying any service, only by typing telnet IP PORT, where IP represents the IP address of the network and PORT represents the portal where the remote host is running.
Wget: This tool is popularly used for Active Banner Grabbing, as this tool helps to connect to the remote host or the localhost. The syntax used for Wget is IP address -q -S, where IP address is the address of the network, -q will help to suppress the output, and -S is used as the parameter that will print the header file sent by the HTTPS server and FPS server.
cURL: works exactly the same as Wget. It also connects to the remote host or the localhost but the only difference is in the syntax format. The syntax used for cURL is curl -s -I IP address | grep -e “Server:”, where -s is responsible for avoiding showing the process of error messages i.e. it mutes the output, -I am the parameter that is responsible for showing header file all the requested pages. At last, grep is used to get the final output from the server.
Nmap: It is an amazing tool to perform Banner Grabbing. It helps to get information from the targeted system in a very easy way. The syntax used to make use of Nmap is nmap –sV –version-intensity 5 site_name -p 80, where -sV allows to lean the software version, and writing –version-intensity 5, the sender can get the maximum information needed from the targeted system.
NC: NetCat or NC is another tool used for fetching information using the banner grabbing technique. It is known to be the oldest and the most popular tool used on UNIX ad Linux. For using this tool, the syntax is written as nc -V IP POST. This helps in getting the FPS banner and the latest software version.
Banner Grabbing through Browser Extensions
Sometimes it’s a bit time consuming while grabbing banners of multiple web applications. Thus in order to make our work faster, we will be setting up some browser extensions that will help us to capture the server information with their version numbers, the running operating systems and the other frameworks that drive up the web applications.
Wappalyzer is a free browser extension available for both Mozilla Firefox and Google Chrome. It helps us to check the technologies of the web-application, majorly the server with its version and the framework running on it.

Steps to Prevent Banner Grabbing In Popular Servers
Apache Servers
ServerTokens Prod: This will configure Apache to not send any version numbers in the server response header so that the server line will be:Server: Apache. Prod is the value that provides the least information (product name only). If no Server Tokens directive is provided, it is equivalent toServerTokens Full(with the result being, for example,Server: Apache/2.4.2 (Unix) PHP/4.2.2)ServerSignature Off: This will ensure that Apache does not display the server version in the footer of server-generated pages. Note that this is the default setting.
IIS Servers
1. First, hide the IIS version. The HTTP header “X-Powered-By” reveals the version of IIS used on the server. To stop this, remove the header:
- Open the IIS Manager.
- In the Connections tree, select the website that SS is running under.
- Click the HTTP Response Headers button on the right. The HTTP Response Headers panel appears.
- Click to select the X-Powered-By HTTP header.
- Click the Remove button in the Actions panel. The header disappears.
2. Second, hide the ASP.NET version. The HTTP header “X-ASPNET-VERSION” reveals the version of ASP.NET being used by the SS application pool. To stop this, remove the header:
- Open the
web.configfile for SS, which is located in the root directory for the website. - Inside the tag, add the tag.
- Save the file.
Third, hide the server type. The HTTP header line Server: Microsoft-HTTPAPI/2.0 is added to the header by the .NET framework. To remove that information, you must update the Windows registry.
Ngnix Servers
1. Open NGINX configuration file
$ sudo /etc/nginx/nginx.conf
2. Hide NGINX Server Version & Name
The NGINX server information can be hidden using server_tokens header. Add the following line to http block.
http{
...
server_tokens off;
...
}
3. Restart NGINX
Finally, run the following command to check syntax of your updated config file
$ sudo nginx -t
4. If there are no errors, run the following command to restart NGINX server.
$ sudo service nginx reload #debian/ubuntu
$ systemctl restart nginx #redhat/centos
How to Prevent Banner Grabbing?
- Restrict access to services on the network
- Shut down unused or unnecessary services running on network hosts
- You can override your server’s default banner behavior to hide version information. System administrators can customize default banners, configure the network host’s application or operating system to disable the banners or remove information from the banners that could give an attacker a leg up.
- Keep your server and systems up to date to secure your applications against known server exploits.
Conclusion
The technique of banner Grabbing can be used by the authorities to get credential information from some systems and can also be used by non-ethical hackers who would try to invade and steal information from the targeted system for authorities. The former is known as white hat hacking while the latter is called grey hacking. It helps tally the information available on a system by connecting to its host server. The technique is of two types, one is Active Banner Grabbing while the other is Passive Banner Grabbing. There are several tools available for attempting Banner Grabbing. A few examples of these tools are telnet, cURL, Wget, etc


