Contents:
- Introduction to Ipv6
- How a typical Ipv6 address looks like?
- How do you enable ipv6 on your end users?
- Difference between Ipv4 VS Ipv6
- Advantages of Using Ipv6
- Disadvantages of using Ipv6
- Common Misconception of Ipv6
- Tips to deploy an ipv6 network
- Ipv6 protocol security vulnerabilities
- How to perform IPV6 assessment?
- Conclusion
Introduction to Ipv6:
Internet Protocol (IP) is a system that allows hosts to identify and connect to other hosts online. Ipv4 was implemented in the early 80s. Many years after ipv4 was designed, due to the sudden monstrous growth and usage of internet, internet experts started to warn about the address usage constraint from ipv4. So, that’s where the IETF (Internet Engineering Task Force) comes in with IPV6 protocol. IPv6 was intended to replace the widely used Internet Protocol Version 4 (IPv4) that is considered as the backbone of the modern Internet. Let's take a look at the number of unique addresses it provides and the number is
2^128 = 340,282,366,920,938,000,000,000,000,000,000,000,000. So much unique IP addresses.
How a typical IPv6 address looks like?
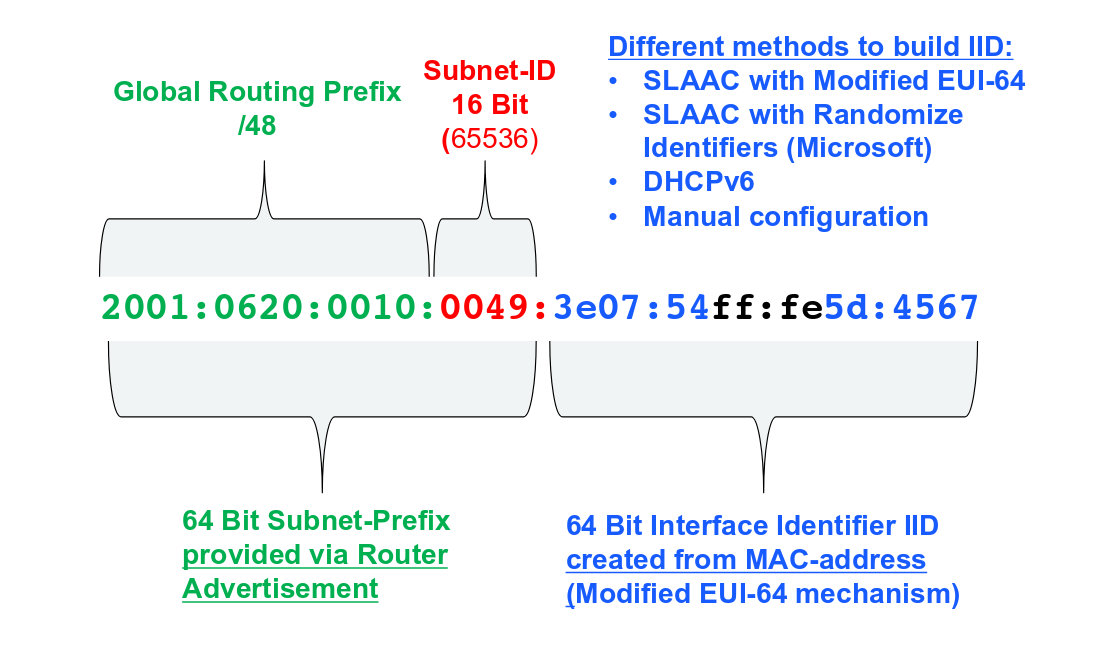
How do you enable ipv6 on your end users?
All versions of windows operating systems and their editions that are currently supported by Microsoft are capable of using IPv6 and IPv4. In most cases, windows operating system comes with both ipv4 and ipv6 enabled by default. Also, here are the steps to enable and configure the ipv6 in windows
- Right-click on the Network icon in your computer’s Notification Area. If you’re using Windows 7 or Windows 10, the Notification Area will be located at the bottom right of your screen in your Taskbar. If you’re using Windows 8 or 8.1, on the other hand, you are going to have to click on the Desktop tile in the bottom left corner of your screen to see the Notification Area where the Network icon will reside.
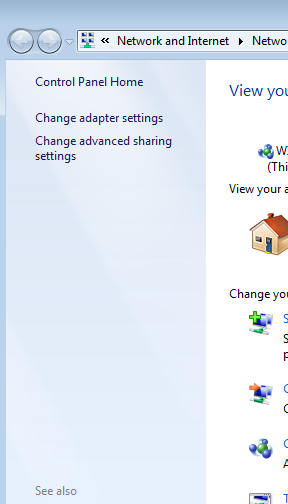
- Click on Open Network and Sharing Center in the resulting context menu.

- Click on Change adapter settings in the left pane of the window.
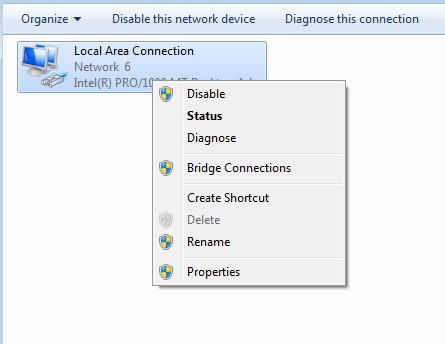
- Locate the network connection that is currently your computer’s active network connection and right-click on it.
- Click on Properties in the resulting context menu.
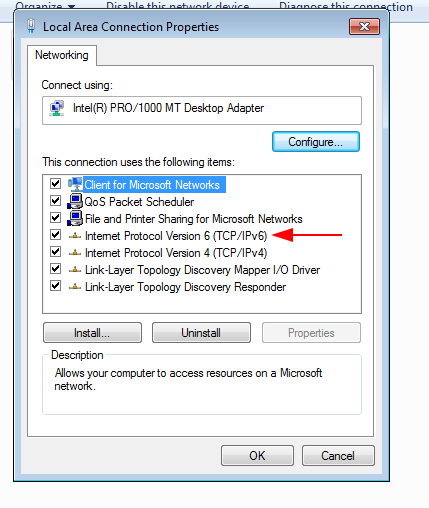
- Next, click the section, locate the Internet Protocol Version 6 (TCP/IPv6) option and check the checkbox beside it to enable it or turn it on.
- Click on OK.
- Close the Network and Sharing Center.
- To find out what is your ipv6 address, type the following command in your command prompt.
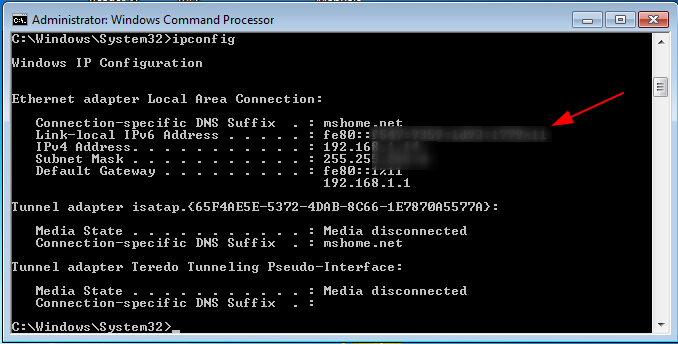
Let's perform a simple port scan on windows with our kali Linux machine using IPV6.
Before performing port scanning, I’ll show you how we enable ipv6 on our kali machine.
- First open up kali setting menu, click on the small gear option on the right side of the menu, the Wi-Fi or Ethernet connection you are connected to.
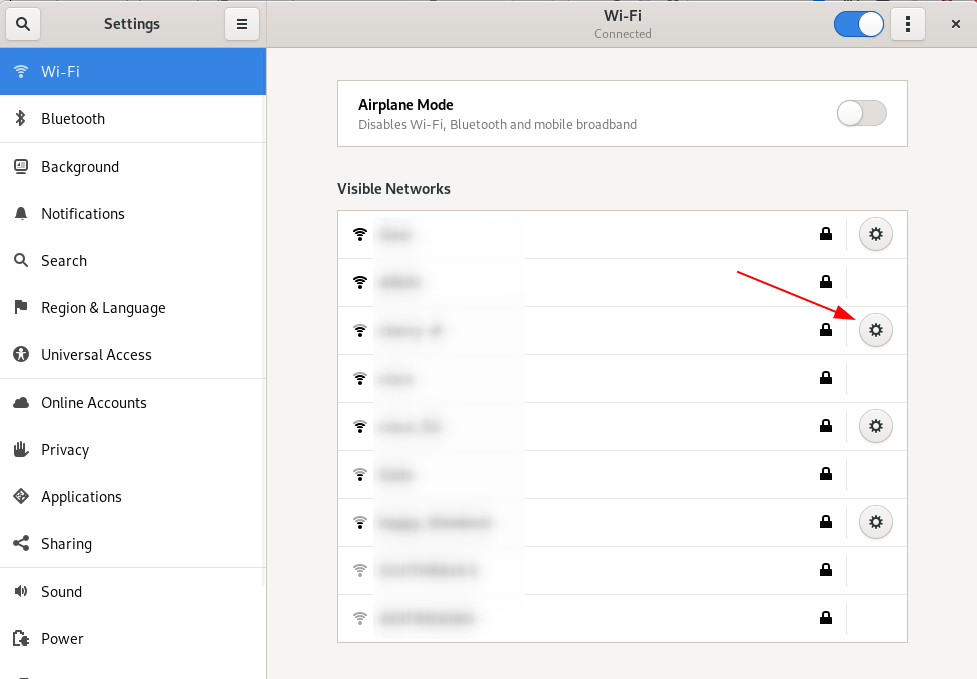
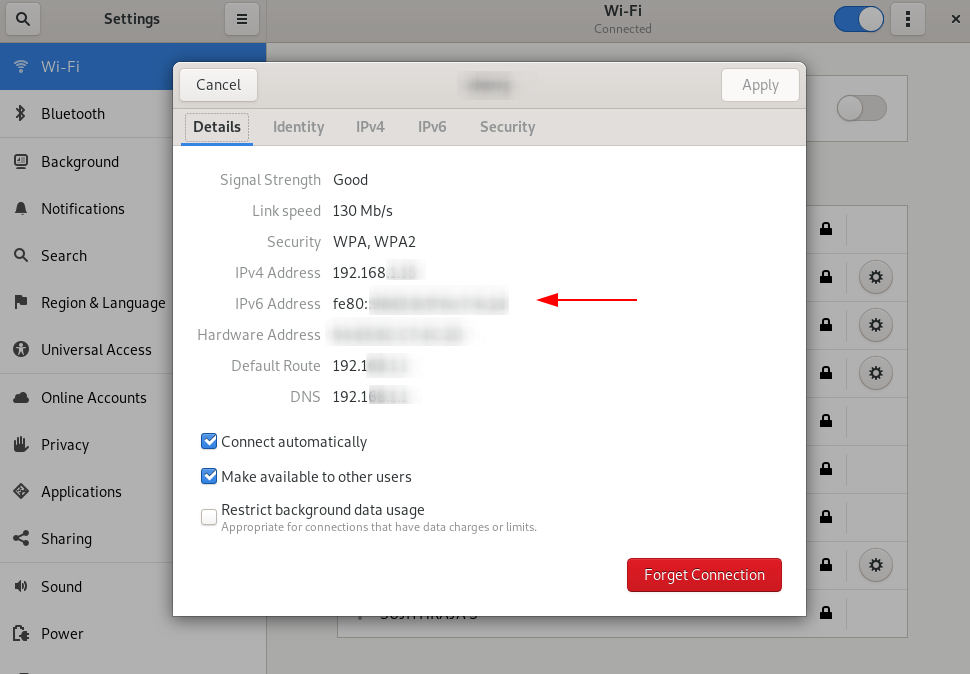
- Choose ipv6 option, select the automatic or manual option by clicking the radio button.
- Then restart your network service.
- You can view your ipv6 address here or check it by “ifconfig”.
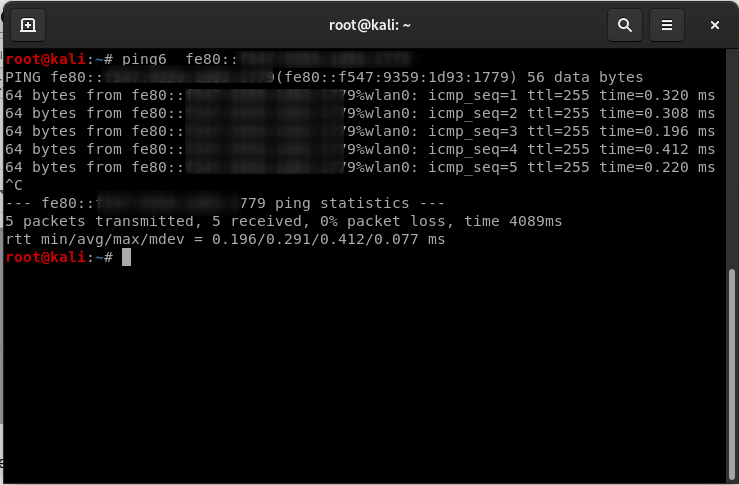
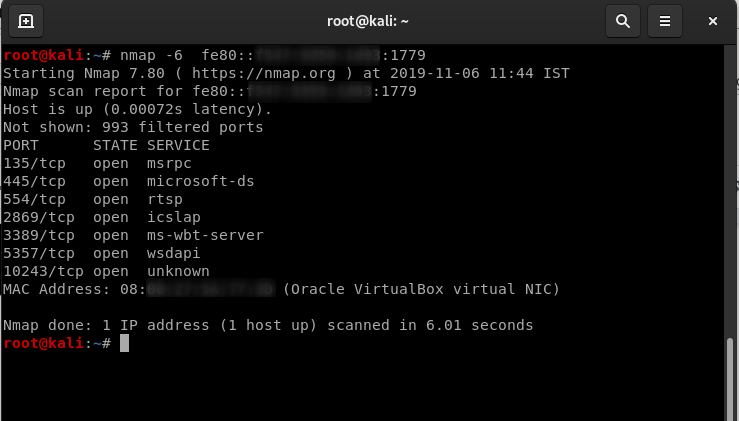
Time for port scanning using Nmap:
Pinging the target machine using Ping6
Port scanning using Nmap
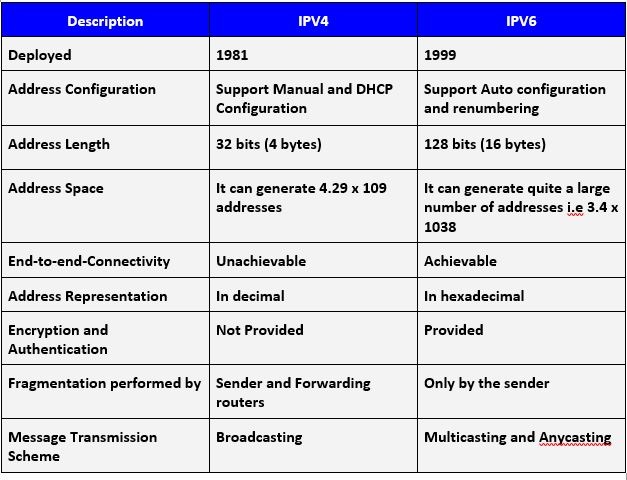
Difference between Ipv4 VS Ipv6:
Advantages of Using IPv6:
- It has huge scalability, which offers a very huge number of ipv6 address space that provides each and every hosts with unique and permanent IP address.
- Comes with SLAAC (Stateless Address Auto Configuration) mechanism for providing Address Auto Configuration for lack of effort to put and cost effective for deployment.
- It has enhanced security features and a far lucid authentication factors when compared to IPV4.
- Improved data integrity
- Offers multicast functionalities
- Efficient packet-forwarding
- Network Layer security, offers better encryption and authentication for communication.
Well, these are the positives. When we discuss about the good side, we must also discuss about the bad side as well.
Disadvantages of using Ipv6:
- Ipv6 provides a huge number of IP addresses and so it’s difficult to remember each and every IP address. When compared to IPV4, it is very hard to remember.
Example: IPv4: 192.168.1.1
IPv6: AB23:A120:0000:0000:1C2A:ACB3:2322
- Many devices still don't have support of IPv6 i.e those that are only ipv4 compatible.
- Many vendor devices still have bugs and issues in them.
- Migrating from ipv4 to ipv6 takes a lot of time.
- Devices that don’t support IPV6 must have dual stack setup configured manually.
- Communication problems will occur because ipv4 and ipv6 devices cannot communicate with each other directly.
Common Misconception of IPv6:
By the way, there is a general misconception when it comes to ipv6 security. It is
“IPV6 is more secure than IPv4” and “IPv6 is less secure than ipv4”
The truth is both are wrong. When we look at the sentence that ipv6 is much secure that ipv4, it is meaningful, but it is also not.
In today's networks, whether we have implemented/deployed ipv6 in them or not, ipv6 is largely compatible. All the modern day operating systems and networking devices comes with dual stack option in them, which means by default, the ipv6 is supported. Your network will still be having the same vulnerability attack surface of ipv4 and ipv6, even if you haven’t actively deployed ipv6 in your network.
Therefore, saying ipv6 is more secure than ipv4 is meaningless because they both share the same vulnerabilities of ipv4 and ipv6.
Tips to deploy an ipv6 network:
Implementing ipv6 network in your organization is not the hardest part. Implementers need not completely remove ipv4 network or completely replace the ipv6-enabled devices. The network can be deployed in the form of parallel method, calling it as “dual stack” which adds ipv6 network capabilities over or along with the ipv4 capabilities. Before discussing about the deployment, let's take a look at the statistics on how much of ipv6 network has covered the economy.
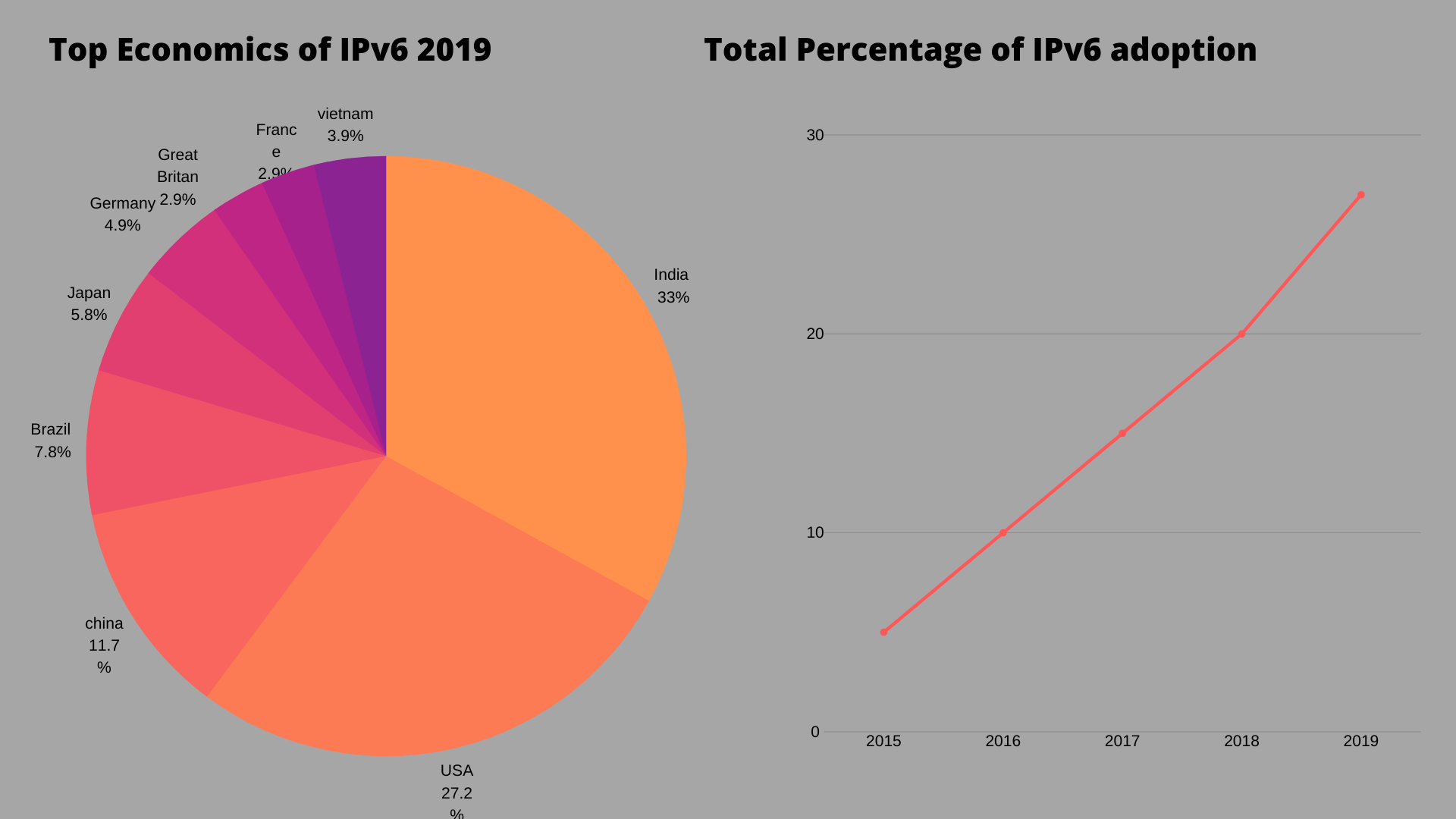
Deploying ipv6 network in your organization can be done with following steps. This will also give you some ideas and guidance.
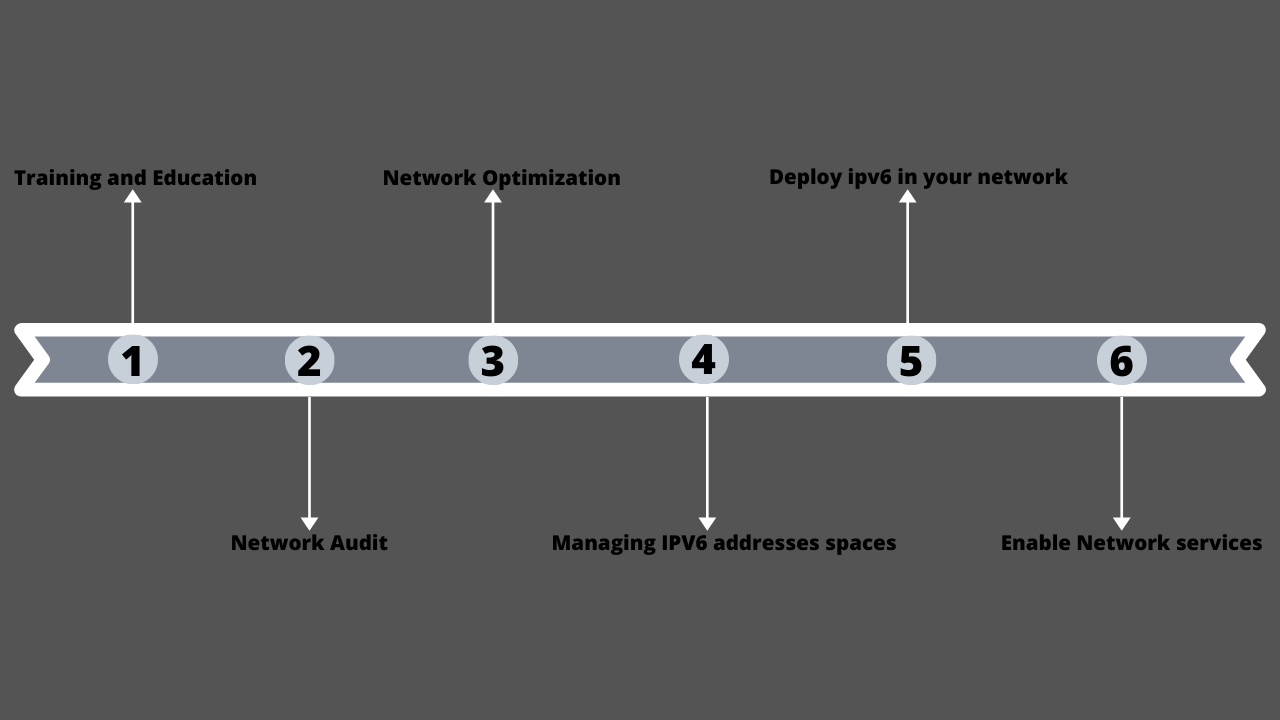
Training and Education
It is very important to provide training and education about the ipv6 deployment to the implementers.
Network Audit
It is necessary to find out what kind of equipment you’ve deployed on your network. The truth is, when it comes to ipv6, almost all the vendors have issues and bugs. So, implementer should know about the equipment to be used according to their software used which is compatible with ipv6.
Network Optimization
Deploying ipv6 network in an organization takes time to achieve. So this could be your perfect time to clear out your existing network. Most of the organizations network has been periodically changed into what they are now with different implementation phases.
During you network optimization, try to follow this simple guideline
- Reduce the complexity in the network as much as possible
- Components standardization should be provided in your network
- Try to provide network planning this time, as we probably use smaller network plan on the previous network.
Managing IPV6 addresses spaces
Acquiring an IPv6 address space is very easy as well as the transit for it. You can request ipv6 address space from your RIR - (Regional Internet Registry), if you already own an ipv4 address space.
Deploy ipv6 in your network
Deploying ipv6 in your network will be easy. If you have done everything so far, configuring network device interfaces with ipv6 addresses are just straight forward and setting up and configuring routing protocols like OSPFv3 are quite simple.
Enable Network services
Once your network components are completely configured, you are almost ready to connect your end-user using ipv6. Configuring and enabling ipv6 to end users is just a straightforward step after your verification that your end devices supports ipv6.
Ipv6 protocol security vulnerabilities:
During the implementation of ipv6 protocol, the implementer should follow to create an interoperable protocol, which defines the specification of ipv6 by IETF. IPv6 deployment is relatively new to the market and software’s created for these systems aren’t been field tested as thoroughly as their IPv4 counterparts. There is some sort of time where bugs are found, and vendors must need to address quickly to arrest the bugs. Still many groups of security experts are performing many tests against ipv6 for finding issues before the time of complete IPV6 deployment.
Before studying about ipv6 security, let's see some common network attack vectors like
- Internet (DMZ, fragmentation, web pages, pop-ups)
- IP spoofing, protocol fuzzing, header manipulation, session hijacking, MITM, sniffing
- Buffer overflow, SQL injection, cross-site scripting
- Email (attachments, phishing, hoaxes)
- Worms, viruses, distributed denial of service (DDoS)
- Macros, Trojan horses, spyware, malware, keyloggers
- VPN, business-to-business (B2B)
- Chat, peer-to-peer (P2P)
- Malicious insider, physical security, rogue devices, dumpster diving
IPv6 specific threats and vulnerabilities:
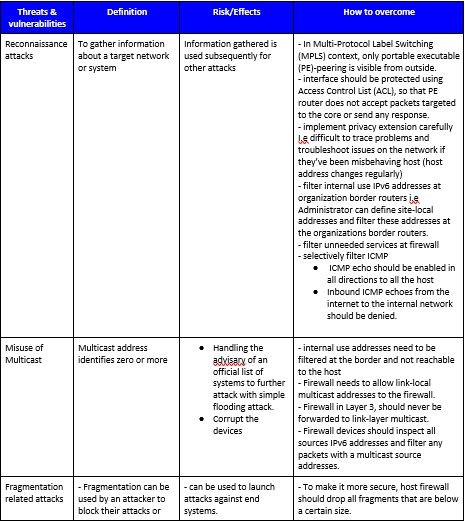
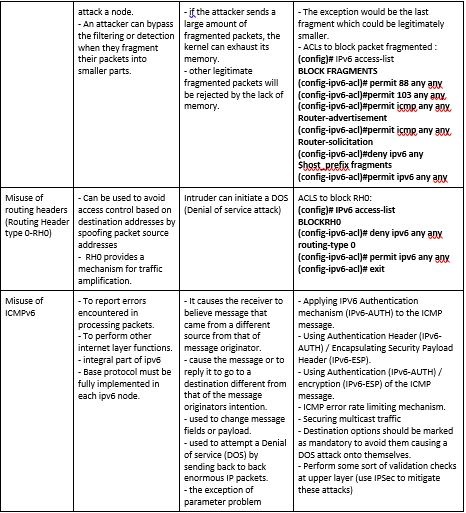

What would be the best practices for ipv6 implementation?
Some of the best practices for implementing ipv6 for building and securing the network are
- Use standard, non-obvious static addresses for critical systems.
- At border routers, filter internal-use ipv6 address.
- Make sure sufficient filtering capabilities for ipv6.
- On ipv4-only networks block all ipv6 traffic.
- Filter unnecessary services at the firewall.
- Create a proper ICMP V6 filtering policy and filter all unnecessary ICMP message types.
- Use IPSec to authenticate and provide confidentiality for end users.
- Pay closer attention to the security aspects of transition mechanisms.
How to perform IPV6 assessment?
We have listed some testing frameworks which is used for performing IPV6 security testing
SI6 Networks' IPv6 Toolkit: https://www.si6networks.com/tools/ipv6toolkit/
IPv6 attack toolkit: https://github.com/vanhauser-thc/thc-ipv6
Chiron - An IPv6 Security Assessment framework with advanced IPv6 Extension Headers manipulation capabilities.
https://github.com/aatlasis/Chiron
Conclusion:
Before ipv6 deployment in your organization network, everyone should be aware of certain best practices for security aspects in Ipv6 traffic.
- Protecting host from scanning and attacking
- Protection of IPv6 packets
- Protecting & Controlling of what traffic is exchanged with the internet.
- Authorization for automatically assigned addresses and configurations
- Prevention systems (Firewalls and intrusion detection)
There are three components required to achieve IP multicast security. They are
- End - to - End data protection.
- Multicast routing protocol security (Multicast distribution tree protection).
- Membership access control at the subnet level.
However, because both the ipv4 and ipv6 are network layer protocols, most of the vulnerabilities are similar. Participation of each and every device on the network should be protected. The most important is Ipsec. It should be considered very seriously to provide proper authentication, integrity and confidentiality in services.


