Introduction
Computerized reasoning (artificial intelligence) is encountering noteworthy developments in the domain of emerging digital elements and advances. Its capability to reform and expand specialized processes is generally perceived, making it an incredible asset for both people and machines. Computer-based intelligence can drive significant change, empower checks, work with transformation, and even contribute to the making of specialized arrangements. Its effect is especially apparent in the field of network protection, where ongoing advances have had huge ramifications. Man-made intelligence-controlled danger hunting has emerged as an important methodology for distinguishing complex and obscure dangers. Furthermore, the utilization of generative man-made intelligence to recreate assaults has demonstrated its effectiveness in reinforcing protections.
Transparency in AI models' decision-making has increased trust and comprehension thanks to explainable AI. Anomalies and insider threats are also being successfully detected by AI-enhanced identity and access management systems. In response to attackers' ever-evolving tactics, AI-based phishing detection methods have developed. The utilization of protection-saving computer-based intelligence methods guarantees secure and cooperative information investigation while shielding protection.
Ultimately, simulated intelligence-driven digital danger insight empowers quick identification of arising dangers. These new patterns represent the ground-breaking job of simulated intelligence in network safety, enabling associations to upgrade their alarming statement location, reaction, and general strength notwithstanding developing digital dangers.
About AI and its capabilities
Man-made reasoning (simulated intelligence) is a rapidly developing field that looks to make canny PC frameworks equipped for performing undertakings like people. These artificial intelligence (AI) systems look at huge amounts of data, find patterns, and make thoughtful decisions. They are very good at machine learning, computer vision, and natural language processing, which gives them the ability to automate things, increase productivity, and deal with difficult problems. From remote helpers like Siri, Alexa, and Google Partner to clinical determination and artificial intelligence-driven digital danger insight, simulated intelligence tracks down applications across different spaces, moulding an eventual fate of development and unfathomable potential.
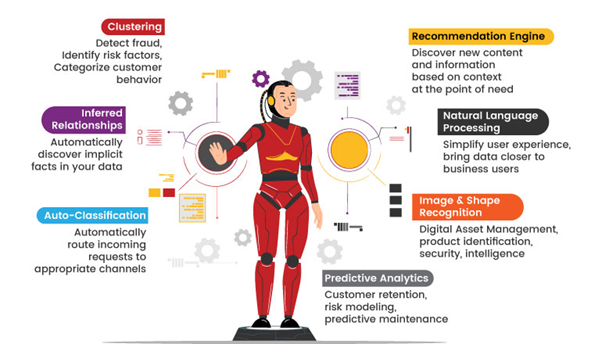
Advanced language models like ChatGPT, which can converse with users in natural language and provide valuable insights and information, have also emerged as a result of AI. Powered by the GPT-3.5 architecture, ChatGPT has the potential to make AI more accessible and useful in everyday life by facilitating seamless interactions and providing users with assistance on a wide range of topics. As artificial intelligence matures, it keeps on driving development in mechanical technology, independent vehicles, money, and amusement, changing organizations, and making more brilliant cycles.
AI Vs Human in Cybersecurity
There are various stages in cybersecurity that require the intervention of both humans and tools. Tools here indicate both AI or any other software that is used in prevention and defense and also reacts as a solution for various cybercrimes and risks to an organization.
Risk and Threat Identification
One of the important processes or phases in cybersecurity is cyber risk and Threat identification. Risk identification involves a lot of process and critical thinking, and because AI is said to be an adaptive technology, it is considered to excel in that process. AI-powered tools such as user and event behavior analytics (UEBA) can detect, analyze, and respond to any anomalies that may indicate an unknown compromise. To argue the comments and the general stigma that AI excels in risk and threat identification, the AI works on a pattern feed with just the observation or understanding of the human; its capabilities are just limited to the information available or feed, and it somewhere can’t think outside the box.
Humans aren’t this way; they are not just limited to information that is available or learned; they have the ability to think completely in a multi-dimensional way. The human mind is more adaptable; we as humans can identify more risks and threats than AI. Also, when it comes to understanding a process or procedure, it is easier to make a human understand it than to feed it to the AI, where misassumptions are highly possible, which may lead to a complete diversion from identifying the risks and threats that are actually related to the process or organization.

Vulnerability Management
On the other hand, vulnerability management involves identifying the vulnerabilities in a complex system. Here the AI plays a strong role; the AI has the capability to scan all the nooks and crannies of the system and can also identify vulnerabilities. whereas humans are required to do it manually or seek tool support for their efficient Vulnerability assessment. Yet all vulnerability scanning requires human intervention. Here, using an AI with the support of a human will ensure a proper and strong vulnerability is identified, all the vulnerability’s criticality is mapped, and proper suggestions are provided.
But the dominance and assistance required from AI tools and any other technology are high in this stage of cybersecurity, as they are very effective in monitoring an enormous number of systems continuously and simultaneously. AI can make automated vulnerability assessments, network scanning, and code analysis easier. When humans and AI work together, it may create a strong vulnerability management strategy that fortifies cyber security defenses.
Incident Handling
Handling an incident is more effective for AI than humans because AI has continuous monitoring mechanisms. Evolven is a great AIOps tool for incident detection and management. Evolven uses intelligent analytics and machine learning to detect and prioritize incidents automatically, learning over time to predict and prevent future incidents. It can easily detect and take a preliminary step to Isolate the incident and also communicate it to the relevant authority automatically. This helps in the quick reaction to any incident that has occurred in the system. The AI is effective in notifying and initiating isolation of any incidents where the human is required to identify and take necessary actions to handle and resolve the incident. where there are few AI tools that also help in Incident investigation and analysis. But those investigations are not analyzed in depth, and the proper findings are observed and finalized only by humans.
Decision Making
In one crucial area where humans beat artificial intelligence (AI), which is ethical considerations and decision-making, Cybersecurity frequently entails complicated ethical quandaries, such as balancing security and privacy or guaranteeing algorithm fairness and transparency. People have ethical reasoning, understanding, and empathy, which allow them to effectively traverse numerous ethical quandaries. While AI excels at data analysis and task automation, it lacks the capacity to make ethical judgments. Human intervention is still required to guarantee that cybersecurity practices adhere to ethical and regulatory requirements.
Learning and Adapting
In the ever-expanding network environment, new threats and attack strategies develop on a regular basis. People are very adaptive, continually learning and expanding their knowledge in order to handle these ever-increasing problems. While artificial intelligence (AI) may give flexibility by analyzing previous data, recognizing trends, and fine-tuning algorithms, people maintain the unique capacity to think critically, uncover new patterns, and apply specialized knowledge to context. Human touch gives us the agility and resilience required to deal with ever-evolving cybersecurity scenarios.
Conclusion
The above stages and arguments are just limited; a proper expansion of this study will bring out a significant result that can justify the observations and suggestions. With regards to the content built above, we can see that human needs in cybersecurity are comparatively higher than those of AI tools, yet humans need support from AI tools to achieve a standard of cyber security in an organization. The collaboration of Humans and AI will show significant growth in cybersecurity, where the importance of humans is high because AI is a machine language that runs in cyberspace and was even created by humans to assist them, not replace them. These AI also require cybersecurity because, even though they are designed to be adaptable and learn quickly, they still can’t protect themselves and require human intervention to deal with them. This shows AI can’t be perfect in cybersecurity, as there is no more powerful system or computer than a human mind to excel not only in cybersecurity but in everything.
We at Briskinfosec use a Hybrid testing methodology by incorporating experts, AI, and tools to ensure the proper and quality service and testing provided to our customers. We also ensure that the Expert's Dominance is evident in all our processes and that the tool or AI is used just to enhance our quality to higher standards. Manual testing is one of the important actions required to ensure a proper cybersecurity standard. Whereas we at Briskinfosec give our best quality in all cybersecurity services.



