If my data is on the cloud, then it is secure.... Isn’t it?
Was that a question or a doubt or a statement?
It all depends on how you perceive it to be. Most business owners feel that cloud space equals cloud security. Now, before I reveal the answer let’s see the story below;
Accenture is no doubt the biggest name in software on the planet. Lock Bit ransomware was used to attack Accenture. The bad guys said that they had stolen 6TB of data and asked for $50 million as a ransom.
The biggest server that was left open seemed to have customer account login information for Accenture. One backup database had almost 40,000 passwords, and most of them were written out in plain text.
Cloud leak shows that even the most advanced and secure companies can lbe vulnerable to data leaks and risk serious consequences.
What is Cloud Penetration Testing?
Cloud computing is the use of the Internet to supply IT resources on a pay-as-you-go basis. Instead of purchasing, owning, and maintaining physical data centers and servers, we can use a variety of technology services such as computing power, storage, and databases.
As we all know, we use a variety of major cloud computing providers for our workloads on a daily basis, including AWS, Google, Microsoft Azure, and Oracle. As cloud services become more prevalent, attackers will focus on cloud services and vulnerabilities. Attackers target managed cloud service providers and their customers with numerous persistent strikes.
Companies that use cloud technologies must ensure that they are secure. They require cloud penetration testing at this time. Penetration testing on the cloud is a type of attack simulation done in order to uncover exploitable flaws or misconfigurations in a cloud-based system. Companies use cloud penetration testing to learn about their cloud system's strengths and weaknesses in order to improve its overall security posture.
How Does Cloud Penetration Testing Differ from Penetration Testing?
Penetration testing, in layman's terms, is the process of conducting offensive security tests on a system, service, or network in order to identify security flaws.So, cloud penetration testing is just simulating an attack on your cloud services in order to assess their security.
What is the Purpose of Cloud Penetration Testing?
The main goal is to identify security flaws in your cloud service before hackers do. Depending on the type of cloud service and the provider, several manual and automated procedures and tools may be employed.
However, because you do not own the cloud infrastructure/platform/software as an entity but rather as a service, running cloud penetration tests presents several legal and technological issues.
Most Common Cloud Vulnerabilities
1. Insecure APIs
APIs are commonly used in cloud services to transfer data across different applications. However, as witnessed with Venmo, Airtel, and other companies, unsecure APIs can lead to large-scale data leaks.
When HTTP methods like PUT, POST, and Erase are used incorrectly in APIs, hackers might upload malware or delete data.API compromises are also caused by improper access restriction and a lack of input sanitization, which can be discovered during cloud penetration testing.
2. Server misconfigurations
Misconfigurations of cloud services are the most common cloud vulnerability today (misconfigured S3 Buckets, in particular ).The most well-known case was the Capital One data breach, which exposed the personal information of around 100 million Americans and 6 million Canadians.
Improper permissions, data encryption, and the distinction between private and public data are the most typical cloud server misconfigurations.
3. Weak credentials
Your cloud accounts may be subject to brute force assaults if you use common or weak passwords. The attacker can use automated tools to make estimates, then use those credentials to gain access to your account.
The consequences could be devastating, resulting in a total account takeover. These assaults are extremely popular since people tend to reuse passwords and use passwords that are easy to remember. During cloud penetration testing, this can be validated.
4. Outdated software
Outdated software has serious security flaws that might put your cloud services at risk. Most software providers do not use a streamlined updating system, and customers can opt out of automatic updates. As a result, cloud services become obsolete, which hackers can detect using automated scanners.
As a result, many cloud services that use obsolete software are vulnerable.
5. Insecure coding practices
Most companies strive to build their cloud infrastructure as cheaply as feasible. As a result of bad coding techniques, such software frequently has SQLi, XSS, and CSRF problems. The top ten are the ones that are the most common among them. The bulk of cloud web services have been compromised as a result of these vulnerabilities.
Performing Step-by-Step Cloud Penetration Testing
Step 1: Understand the cloud service provider’s policies
It is critical to create a testing plan based on the cloud service provider's policies before beginning the tests. This is due to the fact that each CSP has its own policy on:
- Types of cloud pentest that can be performed.
- Endpoints that can be tested.
- Permissions to perform the tests.
- Scope of the tests.
Step 2: Create a cloud penetration testing plan
The second step is to devise a strategy for doing cloud penetration testing. Because every auditor is different, there is no clear method for constructing a strategy. However, here are some measures you can take to create a strategy:
- Map out all the endpoints like user interface, APIs, subnetworks, etc for which testing is to be done.
- Decide which endpoints to exclude based on policy restrictions, user permissions, etc.
- Decide the route for performing the pentest i.e. from application or database.
- Figure out how well the application server and VMs can take the load of the tests that you wish to perform.
- Find out the laws that need to be followed while performing tests.
- Figure out which tools to be used and what types of tests will be performed on which endpoints (Automated or Manual).
- Finally, get the approval for your plan from the client and inform them when you wish to begin.
Step 3: Execute the plan
It's now time to put your strategy into action. Run the tools as desired and monitor the vulnerability replies. Although some tools are well-known, such as Nmap, Sqlmap, and OpenVAS, there are several CSP-specific tools that you can include in your strategy. The following are some of the tools you can use in your cloud penetration testing strategy:
- AWS Inspector: A customized security solution for AWS. It can be used as a basic minimum or preliminary testing tool.
- S3Scanner: An open-source tool to scan S3 buckets for misconfigurations and dump their data.
- Microburst: A collection of PowerShell scripts to scan Azure services for security issues. So, to use them you need to have PowerShell installed which is present by default on Windows OS.
- Azucar: This is another popular Azure scanning tool built using PowerShell just like MicroBurst.
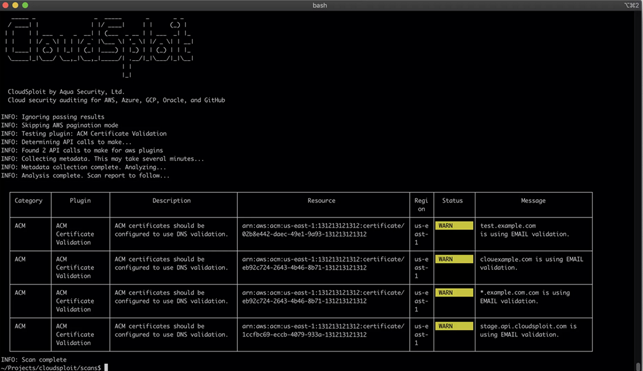
- Cloudsploit: This is a popular open-source tool that can scan multiple types of cloud service providers like Azure, AWS, Google Cloud Platform, OCI, etc.
Benefits Cloud Penetration Testing
- User access and authentication controls.
- Server security configuration and build
- Secure cloud application from hackers.
- Prevent cross client information leakage
- Protect against ransomware and malware breaches.
- Client virtual segmentation and compartmentalization.
- Security system administration program.
- Increased ROI and IT benefits.
- Data encryption.
- Cloud security from DDOS attacks.
To conclude, penetration testing in the cloud is similar to traditional systems, but it does necessitate more preparation and communication. The majority of cloud-related risks stem from non-functional criteria that aren't met, or aren't expressed at all, and so aren't tested or supported. A thorough security testing plan should be implemented to avoid such problems.\
Unless you're planning a security test to examine how their detection team reacts to penetration testing, collect as much information as possible ahead of time and work with the minimum number of contacts at the service provider as possible. This makes the environment more legitimate and normal.
Also,Make sure that IT departments and/or cyber security staff check to make sure that AWS cloud servers are set up correctly. Attacks on servers that aren't set up right can do a lot of damage to the company's reputation, clients, and finances.