Introduction
ISO 27001, the International standard for information security, has been updated to ISO 270012022 after 9 years. The new controls in ISO 27001:2022 aid in identifying risks and devising mitigation plans, ensuring data security, gaining customer trust, and maintaining organizational reputation and growth. Updating to the new ISO standard is crucial for business growth. Let's explore the benefits organizations can gain from the ISO 27001:2022 update and summarise the key differences between the old and new versions.
Old vs. New
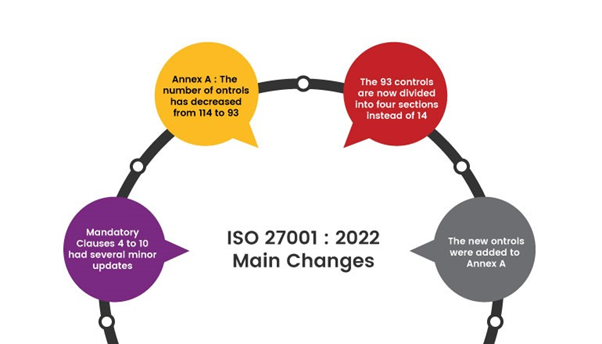
Here is a summary of the changes that happened in ISO 27001:2022.
- Minor revisions have occurred in clauses 4 to 10, with notable changes in sections 4.2- Themes and attributes., 6.2-Terms and conditions of employment, 6.3-Information security awareness, education and training, and 8.3-Information access restriction. New content has been introduced in these areas.
- A total of 11 new controls have been incorporated into Annex A of ISO 27001:2022, while no pre-existing controls have been removed.
- The overall count of controls has been reduced from 114 to 93 in the new ISO 27001
- Modifications encompassed the merging of certain controls, as well as the division of others, all aimed at diminishing the total count.
|
Controls |
ISO 27001:2013 |
ISO 27001:2022 |
|
Threat intelligence |
Not explicitly defined |
Collecting and analysing information about the threats to your organization |
|
Cloud Security |
Not explicitly defined |
Securing your cloud-based applications and data |
|
Business continuity |
Defined as a process |
Protecting your organization against disruptions to its IT systems |
|
Data leakage prevention |
Not explicitly defined |
Preventing the unauthorized disclosure of sensitive data |
|
Information security for use of cloud services |
New control |
Addressing the specific security risk associated with the use of cloud |
|
ICT readiness for business continuity |
New control |
Ensuring your IT systems are ready to support your business continuity plan |
|
Physical security monitoring |
New control |
Monitoring physical security measures to detect and prevent unauthorized access |
|
Configuration management |
Revised control |
Ensuring that your IT systems are properly configured to meet your security requirements |
|
Information deletion |
Revised control |
Deleting sensitive data in a secure manner |
|
Data masking |
Revised control |
Protecting sensitive data by masking it with non-sensitive data |
Steps to be followed in ISO 27001:2022 implementation
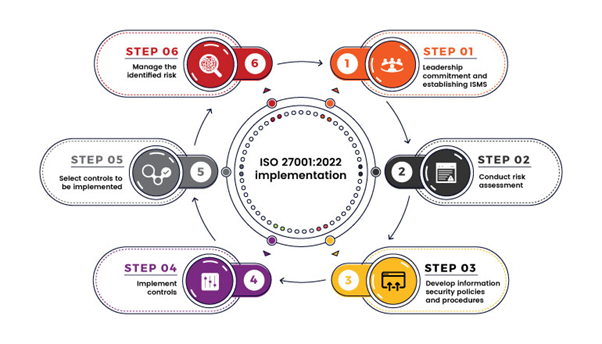
The implementation process consists of six steps for an organization to establish a robust ISMS:
Step 1 - Leadership commitment and establishing ISMS
Step 2 - Conduct risk assessment
Step 3 - Develop information security policies and procedures
Step 4 - Manage the identified risk
Step 5 - Select controls to be implemented
Step 6 - Implement controls
Leadership commitment and establishing ISMS
To establish a robust Information Security Management System (ISMS), the first step involves gaining support from top management and designated personnel. Their commitment is crucial for the successful implementation of the ISMS. During this step, the scope and objectives of the ISMS are defined, with consideration for specific business units and departments. This process also aids in identifying the information assets that need protection as well as assessing potential threats and risks that the organization may face. By involving top management and key personnel from the beginning, the organization sets the foundation for a comprehensive and effective ISMS that ensures the security of its valuable information assets and supports its overall business objectives.
Conduct risk assessment
During the second phase of the ISMS establishment, a thorough risk assessment is carried out to evaluate and identify potential risks, information assets, and vulnerabilities. Subsequently, a well-defined and documented risk assessment methodology is established. This allows for the automated determination of tolerable and intolerable risks, enabling the organization to develop effective mitigation plans to address the identified vulnerabilities.
Develop information security policies and procedures
After conducting the risk assessment, the next step is to develop information security policies and procedures aligned with ISO 27001 requirements. These policies and controls ensure effective Information Security and protect the organization's assets from potential risks
Implement controls and measures
The fourth step involves putting the defined policies and procedures into action by deploying specific controls. These controls encompass physical, technical, and organizational safeguards aimed at protecting information assets and mitigating identified risks. This proactive approach ensures the effective implementation of Information Security measures throughout the organization.
Monitor and Measure
During this step, continuous monitoring takes place, where the performance of implemented controls is regularly assessed. This is achieved through internal audits and incident reviews, which help measure compliance with established policies and identify areas that require improvement. This ongoing monitoring and evaluation process ensures that the Information Security measures remain effective and up-to-date, enhancing the organization's ability to respond to emerging threats and maintain a strong security posture.
Management Review and continuous improvement
In the last step, the organisation regularly reviews ISMS performance with top management to ensure effectiveness. This involves assessing compliance, identifying improvements, and aligning with changing business needs and emerging threats. Continuous improvement maintains robust Information Security capabilities.
Benefits of new control implementation
Implementing the new controls introduced in ISO 27001:2022 significantly enhances data security measures for businesses. By addressing potential vulnerabilities and effectively mitigating risks, organizations can safeguard their sensitive information, prevent unauthorized access, and protect against data breaches. This proactive approach not only helps maintain the organization's reputation but also instills confidence in clients and customers. As a result, businesses can attract more clients and build stronger relationships, ultimately fostering growth and success in the market. Some examples are listed below:
Regulatory compliance: ISO 27001 controls play a vital role in helping businesses align with industry-specific regulations and data protection laws. By adhering to these requirements, organizations can prevent legal and financial penalties while also showcasing their dedication to protecting data privacy. This commitment fosters trust among clients and stakeholders, strengthening the organization's reputation and credibility in the market.
Improve risk management: The new control implementation can facilitate a systematic approach to risk management. By identifying, assessing, and mitigating information security risks, businesses can reduce financial risks and reputational damage.
Increased employee awareness: Implementation of ISO 27001's new controls also includes providing employees with training. Thorough training will be given to employees on how to foster a culture of security throughout the organization to prevent human errors to protect the inside threats.
Conclusion
ISO 27001:2022 certification is crucial for establishing data security and safeguarding an organization's reputation, which in turn fosters client trust and facilitates organizational growth. At Briskinfosec, we possess a deep understanding of real-time ISO 27001 controls, which sets us apart from others. To showcase our distinct approach, we provide our clients with Free Gap Assessments, tailoring the implementation process of ISO 27001 new controls based on the unique needs of each organization. Our dedicated support and guidance throughout the implementation journey ensure robust Information Security protection for your organization.

