Content:
- Introduction.
- How does the Beast attack work?
- What is the impact of Beast attack?
- Launching a Beast attack
- How to fix the Beast attack.
Introduction:

BEAST (Browser Exploit Against SSL/TLS) is a network vulnerability attack against TLS 1.0 and older SSL protocols. Security researchers carried out the attack for the first time in 2011, but the theoretical vulnerability was discovered in 2002.
Why do we wish to talk about such an old assault technique? According to Acunetix's Web Application Vulnerability Report, 30.7 percent of scanned web servers still have weak TLS 1.0 enabled, making them vulnerable to the BEAST attack. This highlights how IT security is still a huge concern for businesses and no matter how many new features boosting security are included in the software, old assaults are still a major problem. This scenario also applies to SSL/TLS flaws such as BEAST, BREACH, POODLE, and OpenSSL Heartbleed.
How does the BEAST attack work?
The Transport Layer Security (TLS) protocol replaces the Secure Sockets Layer (SSL) standard (SSL). Both are cryptographic protocols that allow you to encrypt communication between a web browser and a web server using various cypher suites. This eliminates the possibility of someone listening in on the conversation and stealing personal information.
Using man-in-the-middle attack techniques, attackers may be able to listen in on a web server's and a browser's conversation. They have access to all information transmitted between the web server and the web browser if they do so and there is no encryption. This includes passwords, credit card numbers, and other sensitive information.
Even encryption, however, has flaws that can be exploited. The BEAST attack is a perfect example of this. The researchers discovered that TLS 1.0 (and older) encryption can be easily broken, allowing an attacker to listen in on the communication.
If your server supports TLS 1.0, the attacker can trick it into thinking that this is the only protocol available to the client. protocol downgrade attack is what it's called. The attacker can then employ the BEAST technique to listen in on the conversation.
What is the impact of the Beast attack?
An attacker who successfully exploits this vulnerability on a machine could gain access to the user's current web session's session ID. The attacker may be able to read traffic exchanged between the user and the device if combined with a social engineering assault.
The impact on individual companies is determined by a variety of elements that are specific to each one. Organizations should assess the impact of this vulnerability based on their operational environment, architecture, and product implementation, according to NCCIC/ICS-CERT.
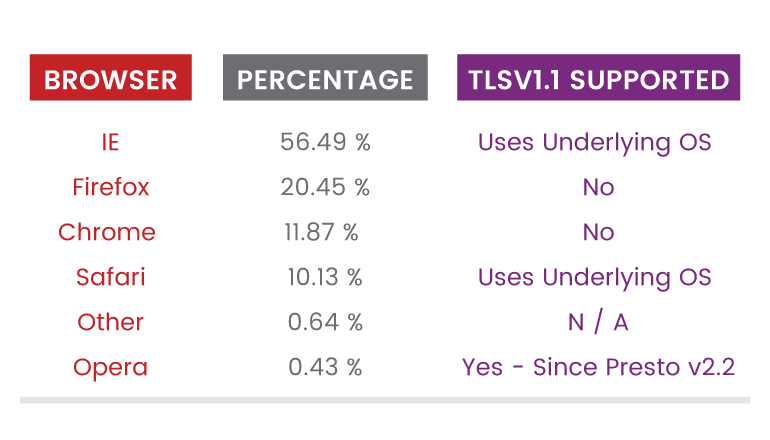
Launching a Beast attack:
Assuming that an attacker is able to "sniff" the client-server message exchange. considering the server's usage of TLS 1.0 or SSL, and the attacker's ability to dupe a user into launching a JavaScript or applet via a rogue website.
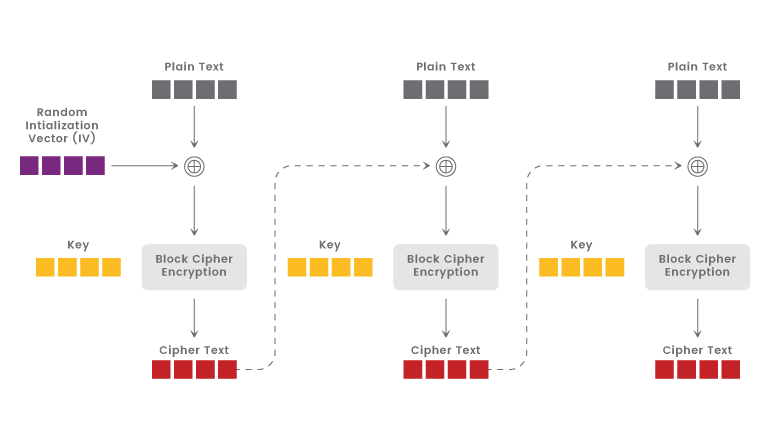
As a result, the attacker would be able to insert data blocks into the session. They'd each have a message's IV, which they'd XOR with the plaintext block they wanted to inject. They might then transmit them to the server and wait for a response, launching a man-in-the-middle attack and performing a so-called record-splitting assault. This is how they gain access to data passed between web servers and browsers, such as passwords, credit card numbers, and other sensitive data.
The problem with the BEAST attack was that only guessing a full block of cyphertext appeared to be doable at first. Unfortunately, guessing an entire block of data, even an 8-bit block, is a difficult operation that could take up to 2568 attempts. As a result, BEAST appeared to be an impractical, if not impossible, theoretical attack.
A new technique was feasible, as Thai Duong and Juliano Rizzo revealed in 2011. Instead of attempting to estimate the entire block, the duo did this. They merely isolated one byte by moving the cypher block boundaries. As a result, guessing one byte is much more manageable, as it restricts the maximum number of attempts to guess a single digit of a number to 10. bytes, with the borders shifting after each successful guess. This is the attack's designated boundary section.
How to fix the beast attack:
The RC4 cypher was originally suggested as a way to protect against BEAST attacks (because it is a stream cypher, not a block cipher).However, RC4 was eventually discovered to be dangerous. The usage of this cypher is now prohibited by the PCI DSS (Payment Card Industry Data Security Standard). As a result, you should never use this technique to defend yourself against BEAST.
BEAST has the same simple solution as other network vulnerabilities: switch off TLS 1.0 and older protocols. Here's how to do it with the most widely used web server software. TLS version 1.1 should also be disabled and only TLS 1.2 should be used (all major browsers such as Google Chrome, Firefox, and Safari support TLS 1.2).
- Apache Web Server
Edit the SSLProtocol directive in the ssl.conf file, which is usually located in /etc/httpd/conf.d/ssl.conf. For example, if you have:
SSLProtocol all -SSLv3
change it to:
SSLProtocol TLSv1.2
Then, restart httpd.
- NGINX
Edit the ssl_protocols directive in the nginx.conf file. For example, if you have:
ssl_protocolsTLSv1 TLSv1.1TLSv1.2;
change it to:
ssl_protocolsTLSv1.2;
Then, restart nginx.
- Microsoft IIS
To disable TLS 1.0 in Microsoft IIS, you must edit the registry settings in the Microsoft Windows operating system.
- Open the registry editor
- Find the key HKLM SYSTEM\CurrentControlSet\Control\SecurityProviders\SCHANNEL\Protocols\TLS 1.0\Server
- Change the DWORD value of the Enabled entry to 0.
- Create a DisabledByDefault entry and change the DWORD value to 1.


