- What is agile development?
- Is cybersecurity a part of agile framework?
- Pain Points for securing agile development?
- Is agile enforcing in house security team?
- How third party security team could secure the agile development projects?
- How OWASP helps in building secure agile model(explanation based on waterfall model)
- Adopting security in Hardware development Life-cycle(HDLC)
- Case study - Lockheed Martin
- Conclusion
What is agile development?
Many of us think that developing an agile model requires lot of time and resources. Even in Today’s virtual world after this pandemic, many companies try to face issues in following their existing mode. To overcome this, we decided to tune up the existing model what we use traditionally in office. We follow one of the most-predominant spiral model like many others we just need to tune this process a little bit to get working in the virtual environment. “So like Japanese we use to send 60-70% of the time in meeting“to understand and start to work based upon the requirement. Agile is deployed in all sectors even-though it was invented by IT team.
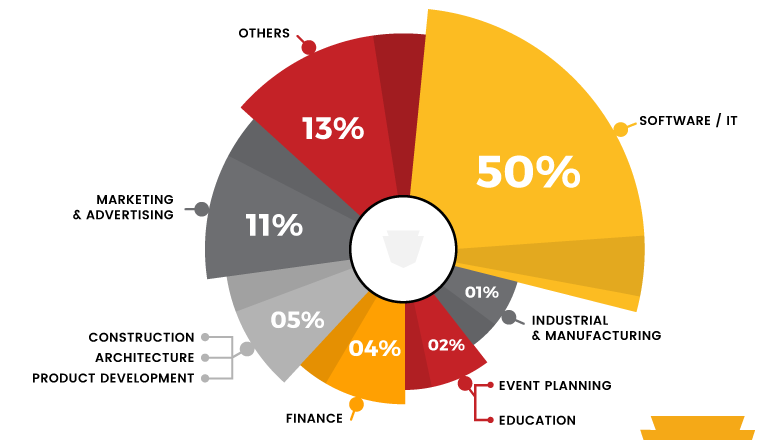
It is proven that the organization incorporating SCRUM framework within the agile model showed up a drastic growth. SCRUM is a lightweight protocol which is used by the organization to get the daily status update of the product development in progress. It acts like a bridge between various team members in the organization who are all working on the various projects. So, if a team faces issues while progressing, a volunteer from other team would help to reduce the project complexity and makes the organization to deliver the project on time to their stakeholder.
Is cybersecurity a part of agile framework
We all know agile is a buzz word but, have you ever thought how cybersecurity helps in building secure framework for your projects. Adopting cybersecurity in agile model increases the project effectiveness, process consistency, enhanced project visibility and team collaboration across the business. The Chief Security Information Officer (CISO) is provided with four basic points that the industry should follow to implement cybersecurity framework in agile process.
- Employees should create an agile model in their own way, it should not be provided.
- Create an agile model from a trusted team in your organization.
- Create a collaborative environment.
- Provide some useful case studies to create them.
Here, the main concern is to create an agile model keeping the cyber constraint in mind, no organization can build a successful cyber agile model in a day or month. It requires some trial and error with your team member's and organization but, one build they will lose longer and kaizen should be followed periodically.
Pain Points for securing agile development
Secure agile development isn’t a painless job in the case of small organization. Since, they have small teams; they may face various issues as their responsibilities grow or when they implement any new thing which leads to,
- Poor analysis of the product
- Creates backlogs
- Blocked Team members
- Fail to create a test plan
All these problems occur due to improper planning implementation in the agile process. Separate environment and credentials should be provided for testers as this also consumes some time which leads to later release of the product. But these above testing problems can be reduced by proper planning and by the use of third party testers.
Is agile enforcing in house security team?
Building a secure agile model and following them doesn’t guarantee that the organization is secured; it has to be updated periodically to the employees. To overcome this issue we should perform,
- Periodic training/knowledge transfer to the employees without external instructors as they would know the plan.
- A strong relationship should be established between the developers and testers as they drive the developers from devops to the devsecops
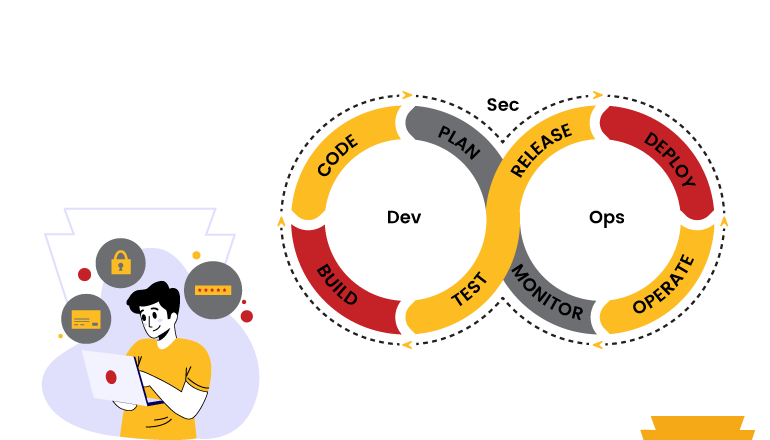
- All these testes are possible for small scale organization but for the larger one you have to think about hiring a best fit for the role.
How third party security team could secure the agile development projects?
Even though the company has an in house security team that uses AST tools to find out all security vulnerabilities in the product the main aim of the third party security vendor is to find out new vulnerability in the products which AST fails to do. We always tend to use application which is free from vulnerability, fast and a good user interface. There are some benefits while the company prefer for third party security testing,
- Has updated security checks compared with in house
- Provides clear cut idea of vulnerabilities with their severity ratings
- Testers guide the development team for fixing issues.
- Work is divided hence there is 90% probability of completing the work on time.
- Product value increases as it is certified by third party.
Third party security team thinks and performs actions like professional hackers and test the product. They also use the same tools and methods to find the vulnerabilities and would provide a detailed report with proper fixes to avoid the real time hacking. So whenever real incident happens the product is safe and no issues happens which increases the overall reputation of the company just because of a third party security testing. Finally they also provide certificates with confirming that the product follows guidelines and standards.
How OWASP helps in building secure agile model
OWASP is a non-profit organization which helps developers and testers to build a secure application. To explain this let us consider the traditionally used water fall model as an example.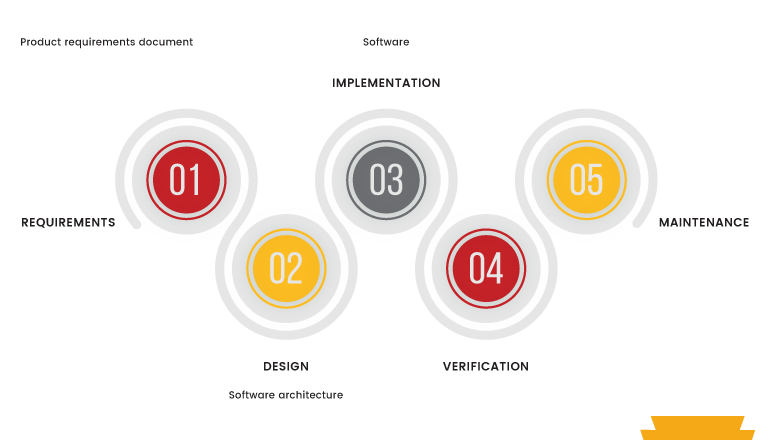
We are all familiar with the waterfall model, once the requirements is been received from the stakeholders we would start planning each phase in the above blocks by keeping the time consideration in the mind. OWASP helps in better understanding and building of scope. A typical OWASP waterfall model is shown below.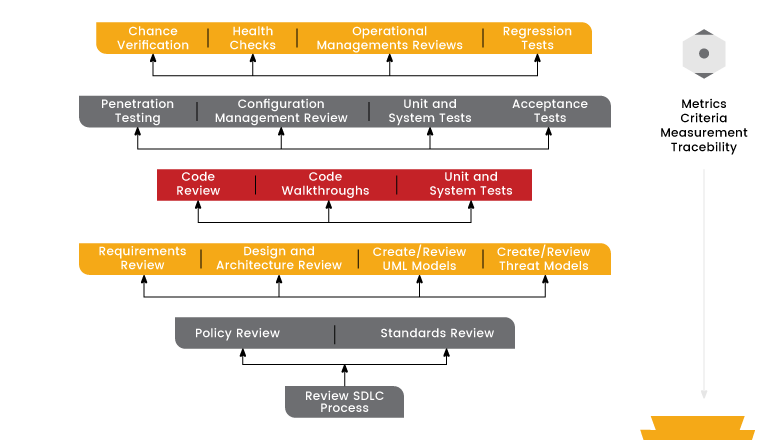
You might notice that lot of steps are being missed by a normal SDLC model while comparing with the OWASP model. Here each of the above stage is further classified to showcase the importance of the security in sub stages. We should be able to build a model that should meet with the OWASP. Hope now you would be able to understand the importance of OWASP in terms of security.
Adopting security in Hardware Development Life-cycle (HDLC)
We have seen that agile model is used only for securing SDLC as it was built by IT professions. But have you ever thought that in terms of hardware?
Adopting the agile model in securing HDLC is easy as software phase,
- We should plan and make sure that the hardware and the software phases are in parallel progress.
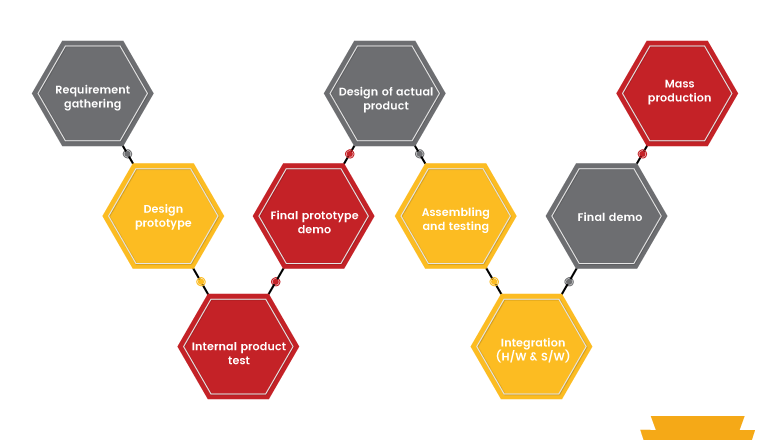
The stages includes
- Gathering the exact requirement
- Designing the prototype
- Internal product testing and revamping
- Final prototype demo
- Creating a custom footprint of the product
- Assembling and testing
- Integration part(hardware and software)
- Final demo
- Mass production
NOTE:
At the integration stage it might also lead to vulnerability and it should be mitigated based upon the severity levels.
Testing is preferred to third-party as they have given reports based on severity levels. Here, the main concern is there are frameworks like ERC and DRC check which we should follow while developing the product with in house security teams.
Case study - Lock Heed Martin
In September 1999 an unmanned U.S spacecraft decided to study the mars was lost, it most likely exploded as it heated up in the atmosphere of Mars after approaching the planet too closely. The spacecraft came too close and had serious issues. According to a research conducted by the IEEE they found that the physical units had not been provided properly.
The contractors who built the spacecraft at Lockheed martin calculated the values to use flight controllers at the JPL labs. JPL did not specify the physical units to be used, but they expected to be in newton. The Lockheed martin engineers returned the spacecraft with pound force. This resulted the variation of the spacecraft about 4.5 larger than they should have been. The errors were neither configured by software configuration process nor were caught by manual inspections. Although there were concerns about the spacecraft’s tragedy, errors in the spacecraft positions were not caught in time. This study proves that requirement gathering is most important specifying all the cases in it.
Conclusion
We have just discussed about the basic agile model and incorporating it in SDLC and HDLC process apart, from this we can also implement agile process for an individual too to track down their individual capabilities. By following the OWASP framework and the building an agile work flow will drive the organization through a better goal. There are also models like xp, crystal, DSDM (Dynamic Systems Development Method), FDD (Feature-Driven Development) which can be readily adapted to the industry without a modification but finally it depends upon the managers and the team-lead.
Last but not least once all these are well planned it is essential to conduct scrum to discuss about the status of the project and where everyone can share their difficulties which paves the wave for quick development of the product.


