What day is best for you?
- Sun
- Mon
- Tue
- Wed
- Thu
- Fri
- Sat
What time works?
30 minutes meeting
Asia/Kolkata Time
Almost there!
IST
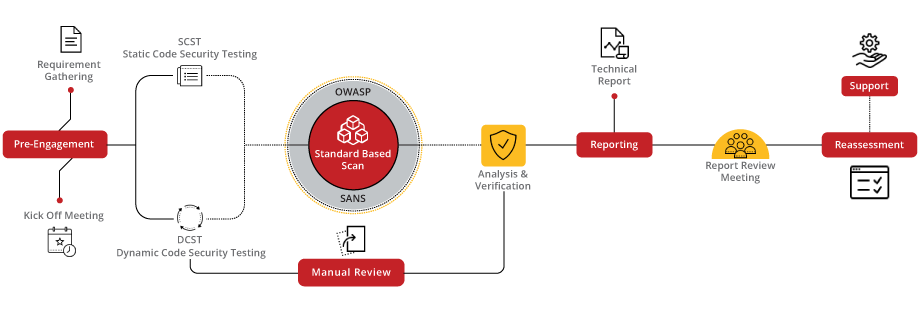
Elevate your application's defense with our Secure Code Review service, meticulously designed to identify and mitigate vulnerabilities at the code level. By integrating best practices and leveraging advanced analysis tools, we ensure your codebase is not just compliant but also optimized for security. Our process involves a thorough examination using a combination of automated tools and expert manual review to uncover potential security flaws, ensuring your application is built on a foundation of security.
Our Secure Code Review process is a detailed journey from code assessment to actionable insights, designed to fortify your application against emerging threats. By focusing on the critical aspects of your codebase, we offer comprehensive insights and recommendations for improvement, ensuring your application’s security is ironclad.
Cybersecurity starts with proper awareness. Briskinfosec’s BINT LAB researchers continuously put an extraordinary effort to help you to realise Secure code review better and faster. Just download the one-page Secure Code flyer, Secure Code Case Study and Threatsploit Adversary report.

Your passport to software integrity, ensuring robust protection against cyber threats and vulnerabilities through meticulous code scrutiny and expert-driven security practices.

Unveiling success stories, showcasing our expertise in securing software applications, and highlighting real-world examples of fortified code against cyber threats and vulnerabilities.

Your window into the evolving threat landscape, offering insights and intelligence to protect against emerging cyber dangers.
Lura cybersecurity simplified portal can help to reduce project execution time, save cost, and bring a positive return on investment (ROI) to customers:
Lura reduces the time spent on documentation and minimizes the overall duration of projects, saving time and resources.
Lura provides a convenient and secure way for customers to access status reports and VA/PT reports, improving efficiency and reducing the risk of errors.
Lura helps to ensure that our cybersecurity services meet the highest standards of quality and regulatory compliance, reducing the risk of costly compliance issues.
Lura is a secure and transparent platform that helps to ensure the integrity of security assessments and build confidence in the quality of our enterprise-grade tests.
Celebrating our achievements and collaborations, shaping a future of excellence.

























Our Case studies are the best reference to prove the dexterity of Briskinfosec.




Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Android Manifest file provides the system with necessary data like application’s configuration information, permissions, and app components. Android Manifest File can be obtained by extracting any APK File and also while doing assessment, you can use APKtool & Drozer for extracting the Manifest file from the application.
Read the blogNull Byte Injection is an exploitation technique which uses URL-encoded null byte characters to the user-supplied data. This injection process can alter the intended logic .
Read the blogThe protection of software applications against potential flaws and security breaches in today's digital environment .
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
Elevating digital safety to unprecedented levels, setting the standard for secure online environments.
Discover our vault and dive into our Carousel for dynamic updates, explore our Infographics for simplified knowledge, and browse our Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!



Embark on a journey through BriskInfoSec's comprehensive suite of cybersecurity services, safeguarding your digital landscape with tailored expertise.






Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment