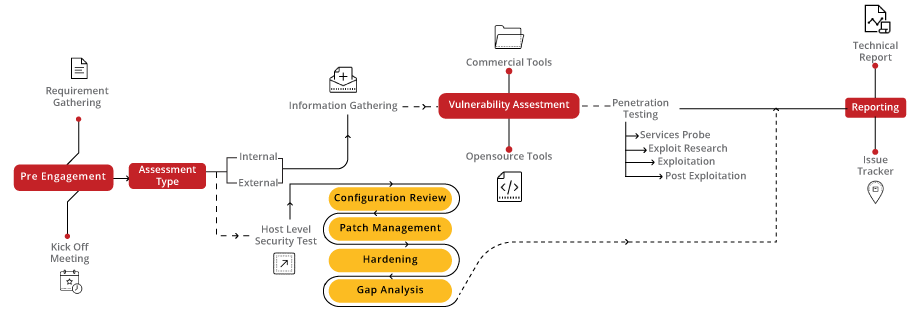
Our Infrastructure VA/PT Audit service offers a comprehensive examination of your digital infrastructure to identify vulnerabilities, assess risk levels, and fortify defenses against potential cyber threats. By conducting thorough assessments of network devices, servers, and critical systems, we aim to enhance the security posture of your infrastructure and safeguard against unauthorized access and data breaches.
Our approach to Infrastructure VA/PT Audit begins with a detailed assessment of your network devices, servers, and critical systems. We then analyze configurations and conduct thorough vulnerability scanning and penetration testing to identify potential security weaknesses. Our team provides actionable recommendations and mitigation strategies to enhance the security resilience of your infrastructure.
Cybersecurity starts with proper awareness. Briskinfosec BINT LAB researchers continuously put an extraordinary effort to help you to realise cybersecurity better and faster. Just download one-page the Network VA/PT Audit Flyer, Mobile App Security Case Study and Threatsploit Adversary Report.
Celebrating our achievements and collaborations, shaping a future of excellence.
Our team is backed by industry-recognized certifications, ensuring top-notch cybersecurity expertise.

















Our Case studies are the best reference to prove the dexterity of Briskinfosec
Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Nowadays the biggest danger that we come across and also something that we are about to face in future is The cyber threat the crime that happens via internet and technology.
Read the blogIn today's world, Cybersecurity has expanded quickly and attracted a large audience
Read the blogYour product is designed to handle sensitive customer data, ranging from personal information to financial records.
Read the blogBrowse our selection of handy cybersecurity tools. Arm yourself with the right defenses to safeguard your digital life.
OSRFramework is a GNU AGPLv3+ set of libraries developed by i3visio to perform Open Source Intelligence collection tasks.
Read the tool of the dayh8mail is an email OSINT and breach hunting tool using different breach and reconnaissance , or local breaches such as Troy Hunt's "Collection1" and the infamous "Breach Compilation" torrent.
Read the tool of the dayWeb applications use parameters (or queries) to accept user input, take the following example into consideration
Read the tool of the dayElevating digital safety to unprecedented levels, setting the standard for secure online environments.
Explore the Cybersecurity Toolkits to dive into the Carousel for dynamic updates, peruse the Infographics for simplified knowledge, and view the Awareness Posters for impactful reminders. Stay ahead in the cybersecurity game!

Your gateway to a world of knowledge, insights, and inspiration, tailored to fuel your curiosity and broaden your horizons.
Expert guidance, tailored solutions- your direct path to insightful, precise answers.
Book Free Appointment
Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.