About
Dirsearch is Tool that performs bruteforce attack of sensitive directories and files that are found on the websites.
Demo

Installation Manual
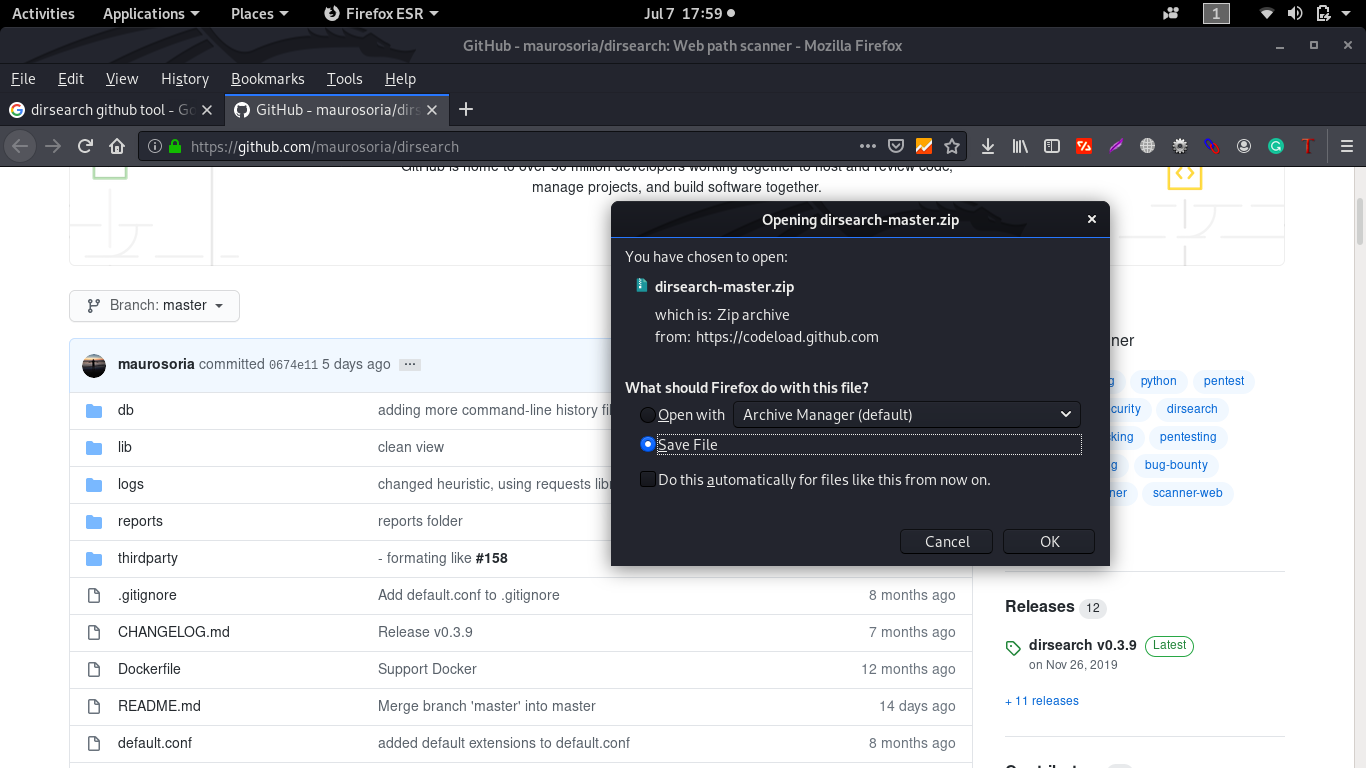
Step 1: Download or Clone the Dirsearch tool in to your system.
root@kali:~#git clone https://github.com/maurosoria/dirsearch.git
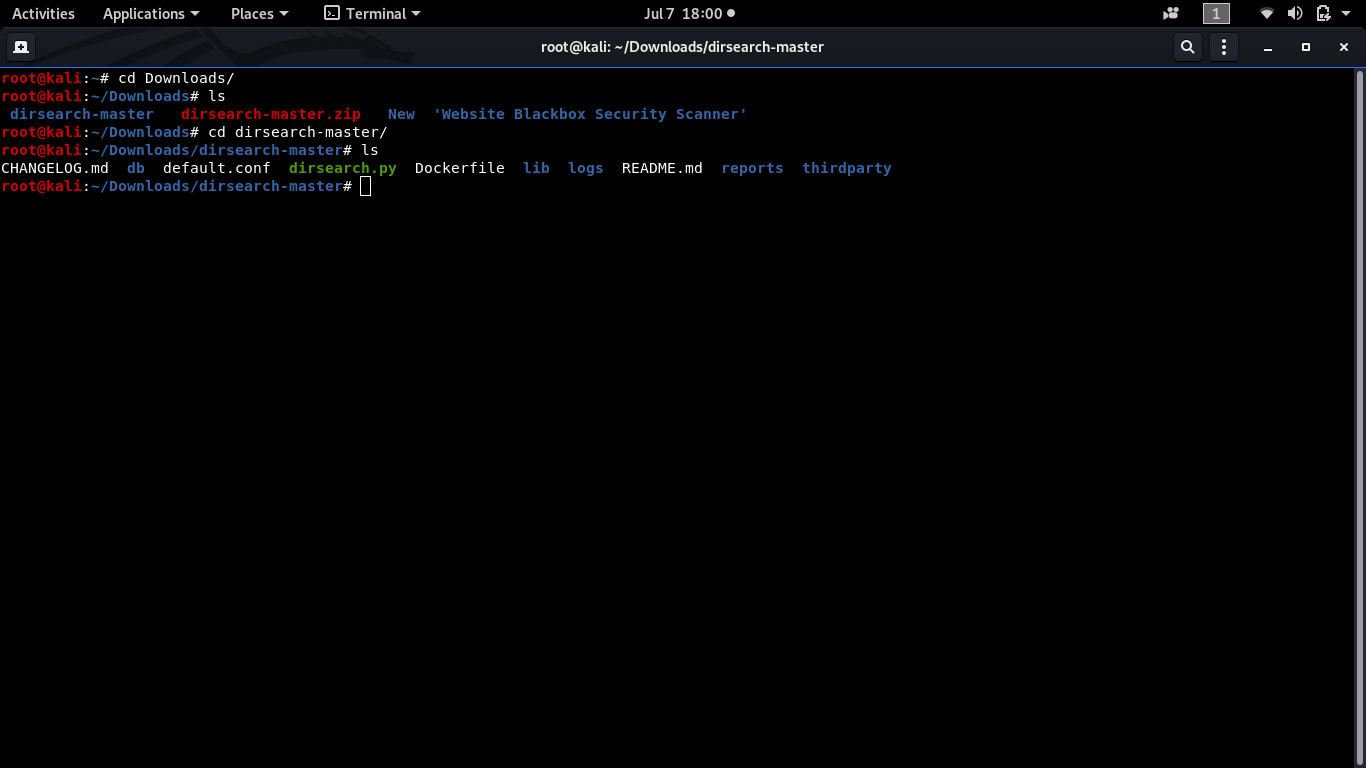
Step 2: Navigate to the Dirsearch tool folder.
root@kali:~#cd dirsearch
Step 3: Run the tool by executing the installation file.
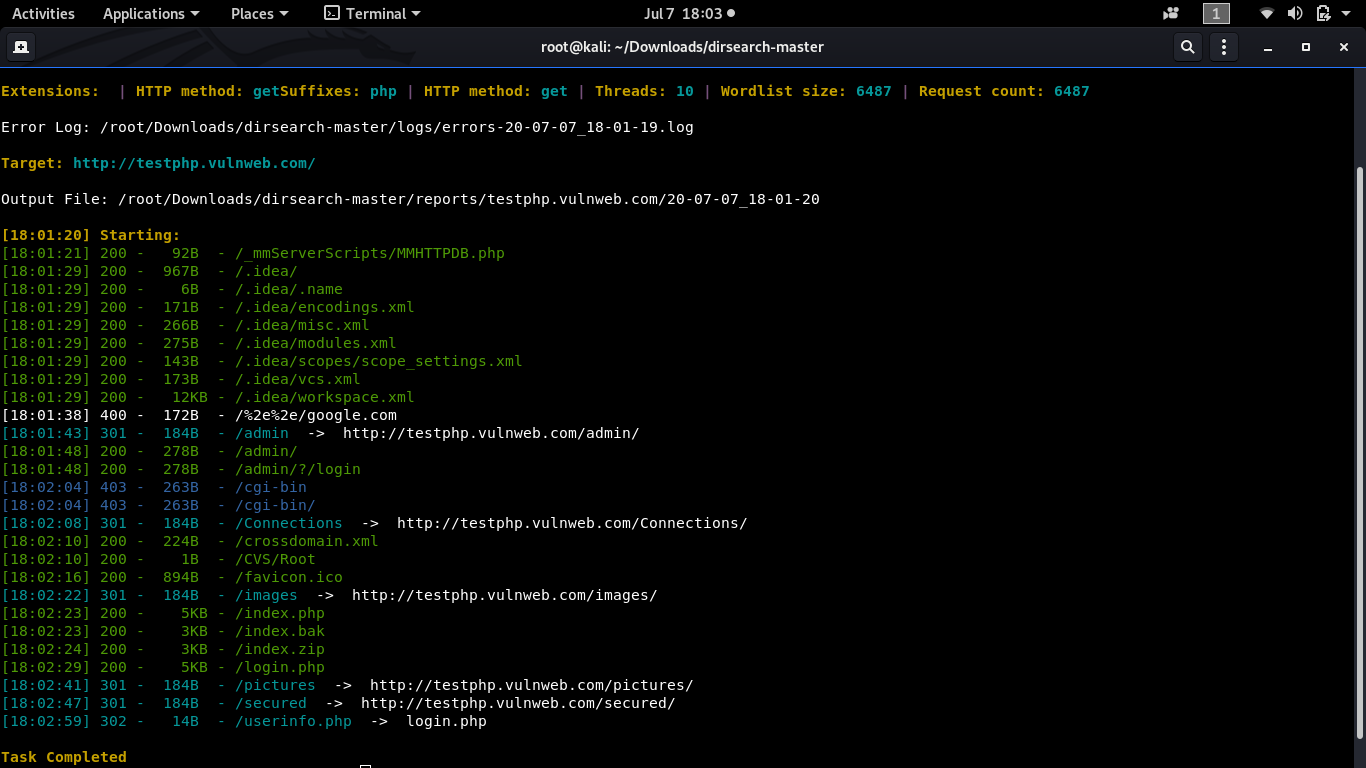
root@kali:~#python3 dirsearch.py -u -e
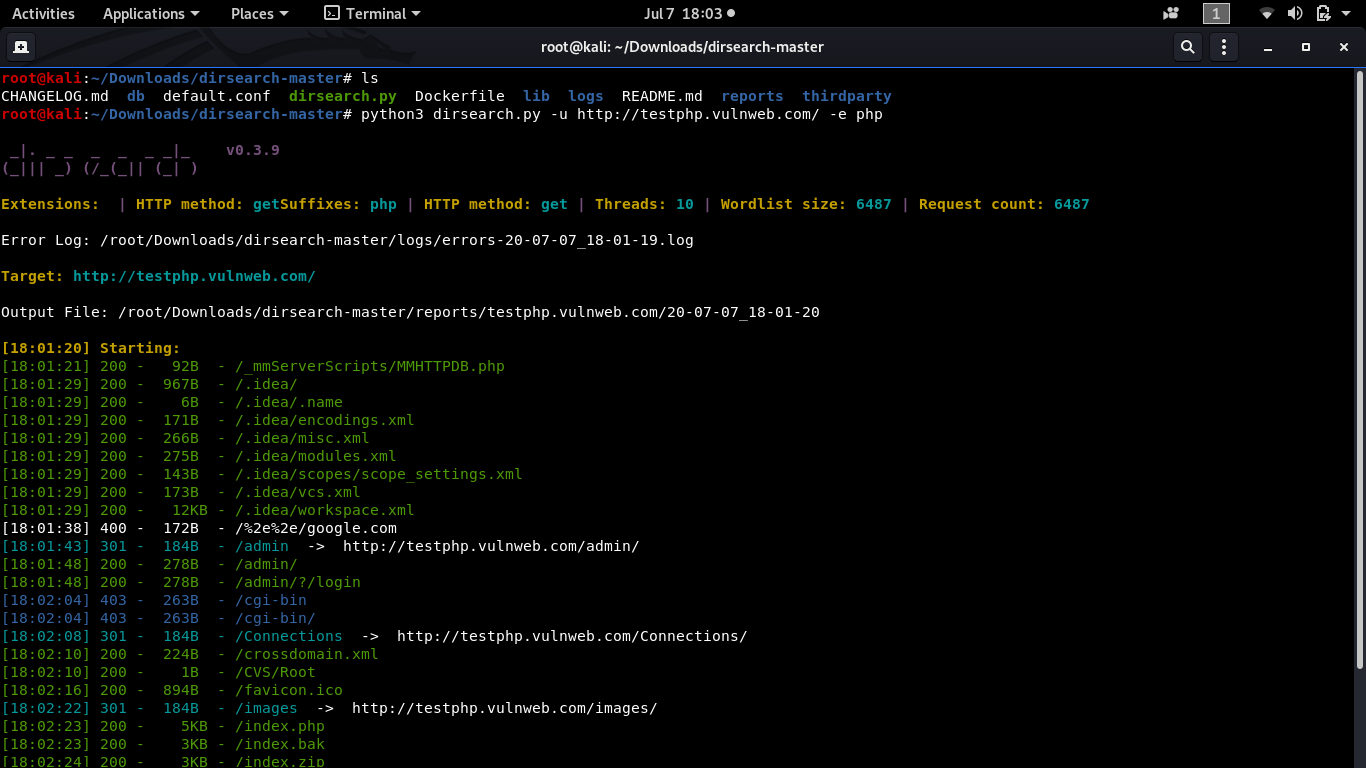
Sample Output:
Options:
To know the Dirsearch tool help command use,
root@kali:~#python3 dirsearch.py -h, --help
Compulsory Arguments:
-u URL, --url=URL URL target
-L URLLIST, --url-list=URLLIST
URL list target
-e EXTENSIONS, --extensions=EXTENSIONS
Extension list separated by comma (Example: php,asp)
-E, --extensions-list
Use predefined list of common extensions
Supported Platforms
-
Windows XP/7/8/10
-
GNU/Linux
-
MacOSX
Features
-
Multithreaded
-
Keep alive connections
-
Support for multiple extensions (-e|--extensions asp,php)
-
Reporting (plain text, JSON)
-
Heuristically detects invalid web pages
-
Recursive brute forcing
-
HTTP proxy support
-
User agent randomization
-
Batch processing
-
Request delaying
-
Option to remove dot from extension when forcing (--nd, example%EXT% instead of example.%EXT%)
-
Options to display only items with response length from range (--min & --max)
-
Option to whitelist response codes (-i 200,500)
-
Option to remove output from console (-q, keeps output to files)
-
Option to add custom suffixes to filenames without dots (--suff .BAK,.old, example.%EXT%%SUFFIX%)
Usage:
How to use
General usage: root@kali:~#python3 dirsearch.py –u https://www.example.com/ -e php
Some examples how to use dirsearch - those are the most common arguments. If you need all, just use the "-h" argument.
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --recursive -R 2
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --recursive -R 4 --scan-subdirs=/,/wp-content/,/wp-admin/
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --exclude-texts=This,AndThat
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt -H "User-Agent: IE"
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt -t 20
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --random-agents
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --json-report=reports/target.json
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --simple- root@kali:~#report=reports/target-paths.txt
-
root@kali:~#python3 dirsearch.py -e php,txt,zip -u https://target -w db/dicc.txt --plain-text-report=reports/target-paths-and-status.json