How can Briskinfosec, as a dedicated cybersecurity organization walk away without cautioning you about the state and fate of cyberattacks that seems to have no precincts in affecting targets. During the month of September, many newly evolved cyberattacks have happened globally. Thinking, why evolved? Well, there are certain security cliché’s like storing data in cloud and implementing 2FA (Two Factor Authentication) prevents your data from hacks. But, the truth is No. In-spite of these being implemented, security breaches still happened.
For example,
• Several YouTube channels hacked, despite few implementing 2FA.
• Delete for everyone option in ‘What’s App’ doesn’t really delete your sent message due to a security vulnerability in it.
• Ecuador faces the biggest data breach in history with 20+ million citizens data being breached.
• A massive sum of 1.7 terabytes of Russian Telecommunications exposed due to a breach.
• Google’s widely popular adblockers have been identified with security vulnerabilities.
Trust me pal. If you think these are the only notorious cyberattacks commenced in the September month, then you’re mistaking. The above said are just like some drops in an ocean. To know more, the entire story lies here. It’d great if you check them out!
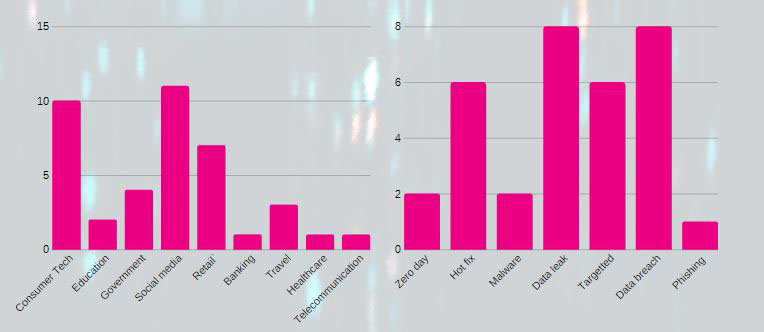
Every month, the Threatsploit Adversary Report delivers a curated overview of the latest global cyberattacks, vulnerabilities, and threat actor activities. We dive deep into real-world incidents that matter most to security teams and decision-makers across industries
This May, we bring you another edition of the Threatsploit Adversary Report, built with one goal in mind: to help you see what’s really happening beneath the surface. Behind every breach is a moment when something slipped through. Whether it’s a missed alert, a trusted vendor, or a tiny misstep in the cloud, every-thing changes in an instant
Cybercrime never sleeps, and neither do we. The April 2025. Threatsploit Adversary Report is here, breaking down the 30 most shocking cyberattacks that shook industries this month.

Get exclusive access to our latest Threatsploit Report detailing the most recent and sophisticated cyber attacks. Stay informed and protect your business from emerging threats.